From Roles to Rules: An Access Paradigm Shift

Ivan Dwyer
Product Marketing, Axonius

Most discussions around identity complexity focus on sprawl – too many apps, too many identity providers, too many systems. But the real challenge is constant change.
It’s worth a reminder: permissions accumulate over time. Every joiner, mover, or leaver scenario triggers new access events – role assignments, group membership, app assignments, and resource permissions. Rarely do those entitlements get revisited, however, and one-off access requests only add to the pile. When access is so scattered across disjointed systems, organizations lack both the visibility to see where potential exposures exist and the actionability to address them consistently. The result? Identity risk quietly compounds.
What if we rethought identity lifecycle management from first principles?
Access should reflect a set of truths – who can do what, in which systems, under what conditions. Attributes like department and function help define what access an identity should have. In systems thinking, these truths should be enforced as invariants – policies that are adhered to, even as conditions change.
That’s the idea behind what we’re calling Access Rules: when done right, it’s not just access control, it’s access orchestration.
Roles belong downstream. Upstream needs orchestration.
With the explosion of cloud and SaaS, roles emerged as the standard model for assigning access. Whether it’s basic user/admin distinctions or intricate IAM policies, roles define what actions an identity can take within a system. They’re simple to understand in isolation and practical for downstream enforcement.
While roles work well within individual systems, the problem isn’t how access is enforced downstream – it’s how they’re assigned upstream.
The challenge is that access needs to be coordinated globally, but roles are only enforced locally.
Every access decision is fragmented across identity providers, SaaS apps, and cloud services, each managing its own piece of the puzzle.
This fragmentation creates two critical challenges. Operationally, it forces teams to coordinate entitlements manually, system by system, with little consistency. From a security standpoint, it expands the attack surface, leaving behind orphaned accounts and excessive permissions that can be exploited.
Without a unified way to manage entitlements across the entire identity fabric, access reality drifts further from the desired state, making identity harder to manage, harder to govern, and harder to secure.
What are Access Rules?
Access Rules flip the script. Instead of assigning access manually, one ticket at a time, continuous orchestration is the operating model – declared once, enforced everywhere.
At the core are two key components:
Profiles: These define what access a person should have: the right combination of group memberships, role assignments, app access, and effective permissions. Profiles are tied to real-world context like department, region, job function, or employment type, and represent the intended access state for a given identity.
Rules: These are the policies that monitor lifecycle events (joiners, movers, and leavers) and automatically enforce the appropriate Profile. When someone’s attributes change, the Rule triggers, and their entitlements are updated across all connected systems.
This way, access always reflects what’s currently true about an identity, not what was true when they were onboarded, or what someone remembered to update manually.
Roles still serve a critical function – they’re the way access is defined inside many systems. But with Access Rules, they don’t have to be managed in isolation. With the right design, they’re the output, not the process.
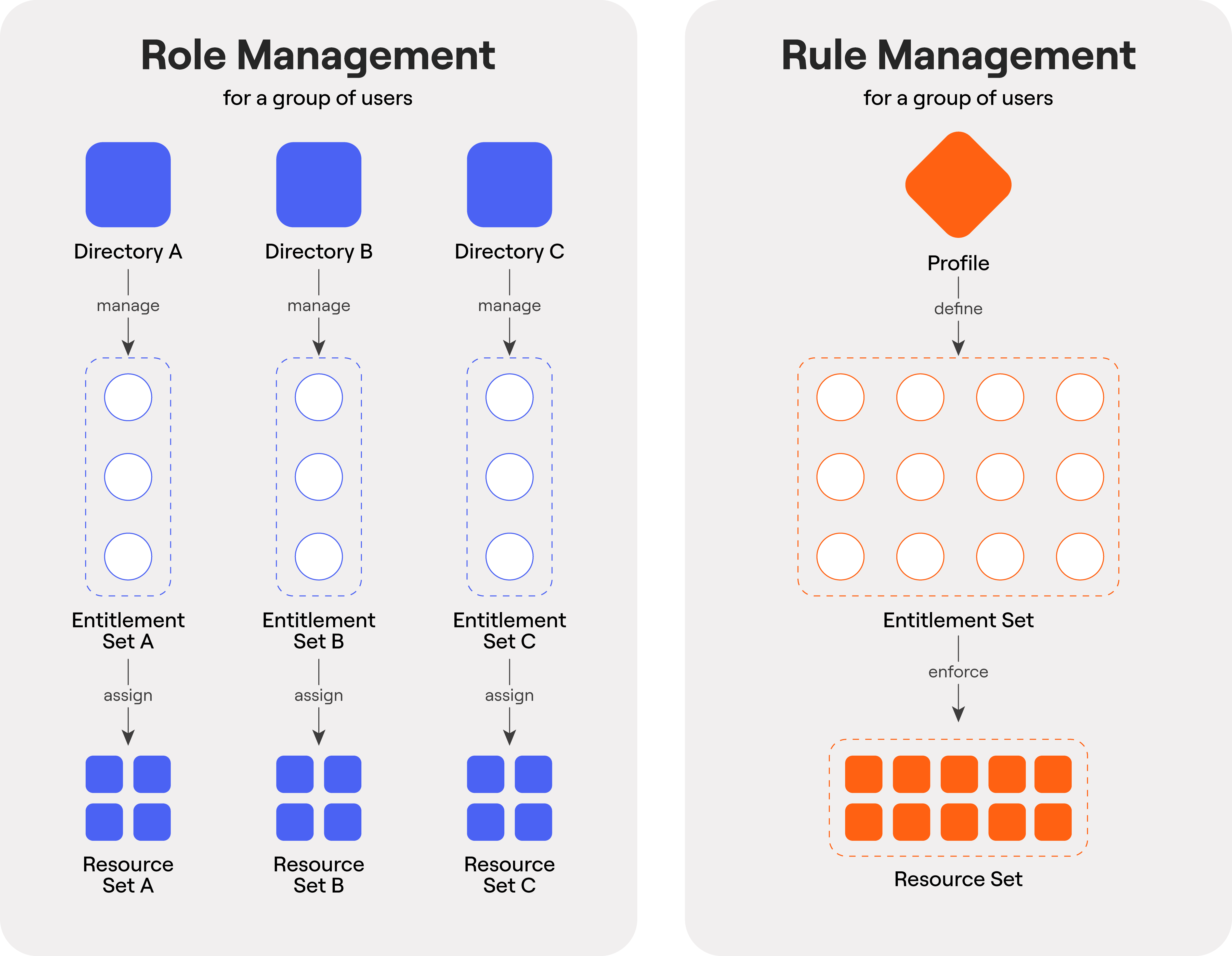
Comparing Role-Based Access Controls with Access Rules
What makes Access Rules possible?
Here’s the rub – you can’t orchestrate access from any singular identity system. As I mentioned in a previous blog post, no single identity source of truth is the one true identity system of record.
Each respective directory, application, tool, and cloud provider is only capable of understanding the account, policy, and access model within its own walls. They might govern local identities and lifecycle events, but they don’t have full visibility into all the entitlements spread across the identity fabric. And they certainly don’t have the reach to orchestrate changes across them.
That’s why Access Rules depends on two foundational capabilities:
Total Aggregation (visibility) brings together all identity artifacts across every directory, application, tool, and cloud provider into a unified model. This is how you define what access should look like, with full context.
Continuous Orchestration (actionability) provides the direct control needed to assign, update, and revoke entitlements everywhere they live – automatically, at scale, and without gaps.
With comprehensive aggregation and orchestration, Rules become the connective tissue between policy and reality. They define what should always be true, and ensure every system adheres to that truth.
The result is a self-healing identity infrastructure, where any change, misconfiguration, or drift is automatically detected and corrected to keep access aligned with policy, without manual intervention.
The Axonius approach to Access Rules
Axonius Identities brings an elevated architecture to the identity landscape: aggregate everything, orchestrate everywhere. By connecting directly with every identity provider, application, tool, and infrastructure provider through our market-leading Adapter Network, Axonius builds a complete picture of identities and their collective entitlements. With that unified context, policy enforcement is orchestrated automatically based on lifecycle events. The result is a single operational layer that unifies identity management, governance workflows, and security hygiene across the entire identity fabric.
Defining Profiles
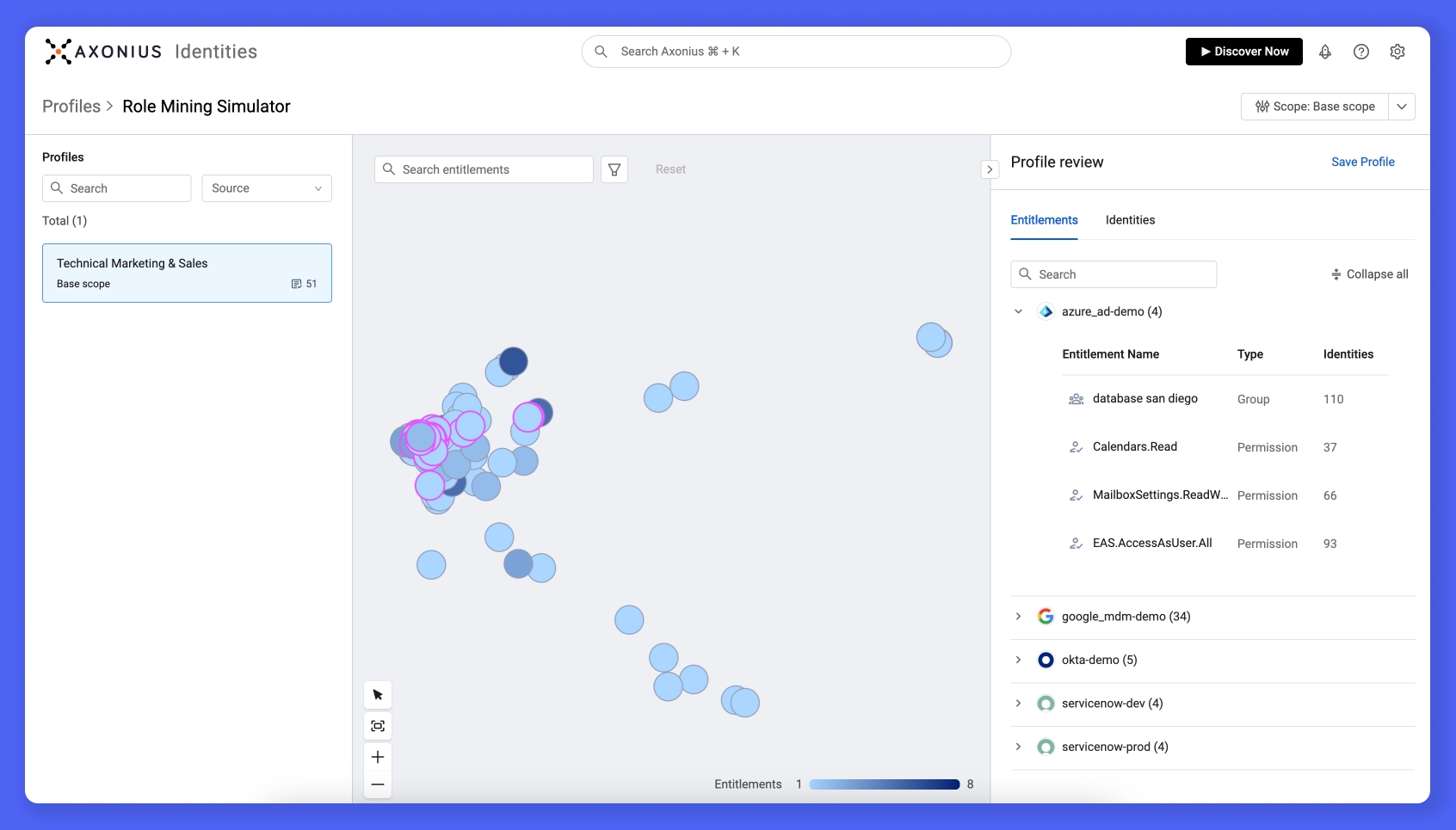
Visualizing an AI recommended entitlement Profile
Axonius maintains a complete, normalized inventory of entitlements across every connected system – group memberships, role assignments, application access, and resource permissions. Profiles are collections of these entitlements, representing what access should look like for a particular type of identity.
Profiles can be built manually, allowing teams to define precise entitlement sets based on internal policies or known access requirements. To accelerate the process, Axonius uses AI/ML to analyze entitlement patterns across users and recommend Profiles that reflect common, consistent access groupings.
Once a Profile is defined, it becomes the reference point for enforcement, ensuring access remains consistent, clean, and policy-aligned across the identity fabric.
Applying Rules
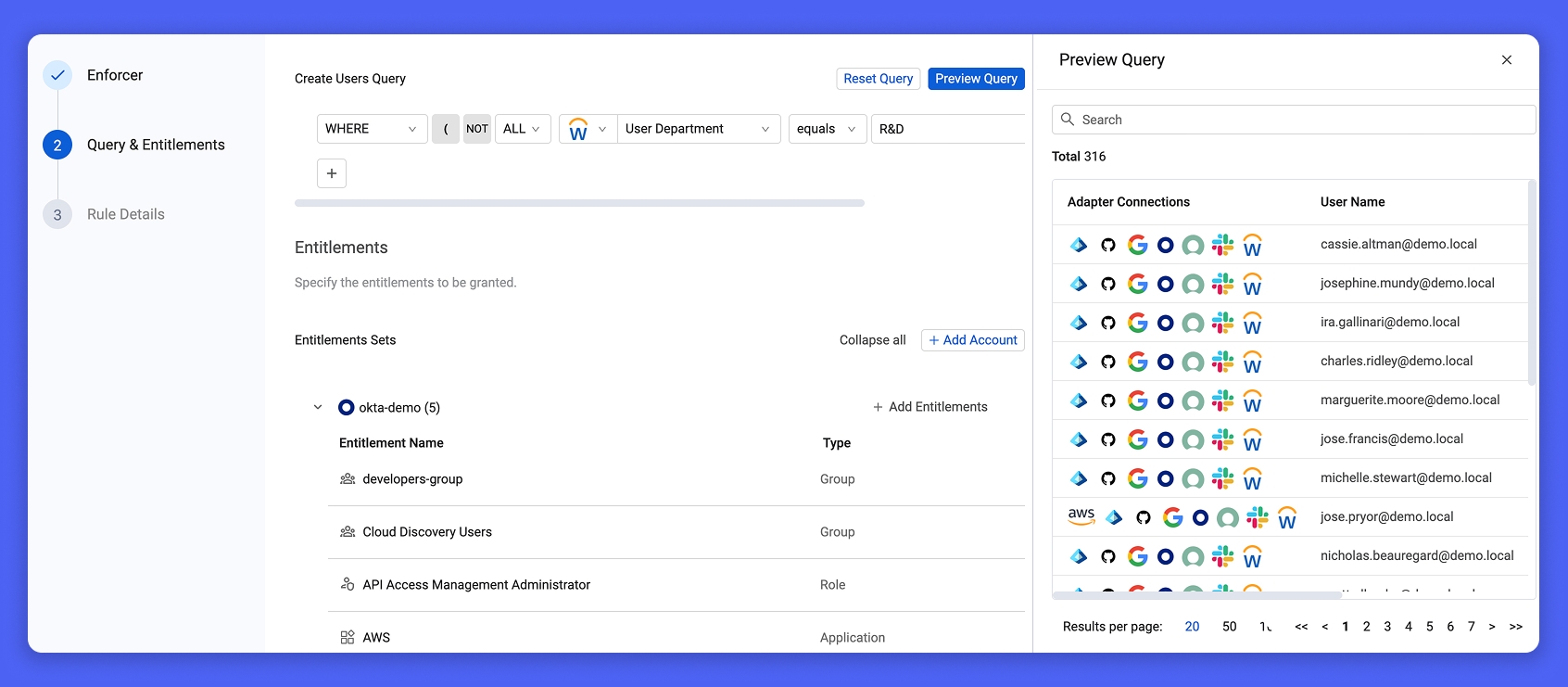
Specifying an entitlement set for a given Profile to be automatically enforced on any JML scenario
The Rule Engine is the orchestration engine behind the Access Rules model – automatically enforcing the right Profile when identity context changes. Whether someone is onboarded, changes roles, moves teams, or leaves the organization, Rules ensure entitlements are updated instantly and accurately across all connected systems.
To apply a Rule, users simply select the relevant Profile and define the matching logic using an Axonius query, – based on identity attributes like department, location, title, or employment type. Rules continuously monitor for changes from authoritative sources like HR platforms, identity providers, and cloud infrastructure. When a match occurs, the Rule applies the associated Profile, updating or removing access as needed.
Unlike tools limited to a single identity provider or app ecosystem, Axonius is uniquely positioned to orchestrate changes across your entire environment – from SaaS apps and directories to infrastructure and cloud platforms.
Rules turn Profiles from static policies into dynamic enforcement. Instead of relying on manual tickets or brittle automations, organizations can declare access once and let Axonius handle the rest.
Redefining access from the top down
Identity lifecycle management doesn’t belong to any one system – it’s a global challenge. Joiner, mover, and leaver scenarios may originate in HR platforms or cloud infrastructure, but the access they affect spans dozens of disconnected systems. Managing that complexity manually only leads to drift, delays, and exposure.
Axonius redefines lifecycle management by combining the power of total aggregation with the scale of total orchestration. With Access Rules, you don’t just declare what access should look like – you make sure it stays that way.
To learn more about Axonius Identities, schedule a demo with our team today.
Categories
- Identity

Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
