Axonius recently hosted The Great Debate, a 10-part webinar series debating the merits and pitfalls of some of the hottest topics in cybersecurity today. This blog post recaps the key takeaways from the seventh episode, where our guest speakers argued the pros and cons of prioritizing cloud security posture management.
Read on to find out whether maintaining a robust cloud security posture should be the No.1 cybersecurity initiative for IT and security professionals in 2021.
What is Cloud Security Posture?
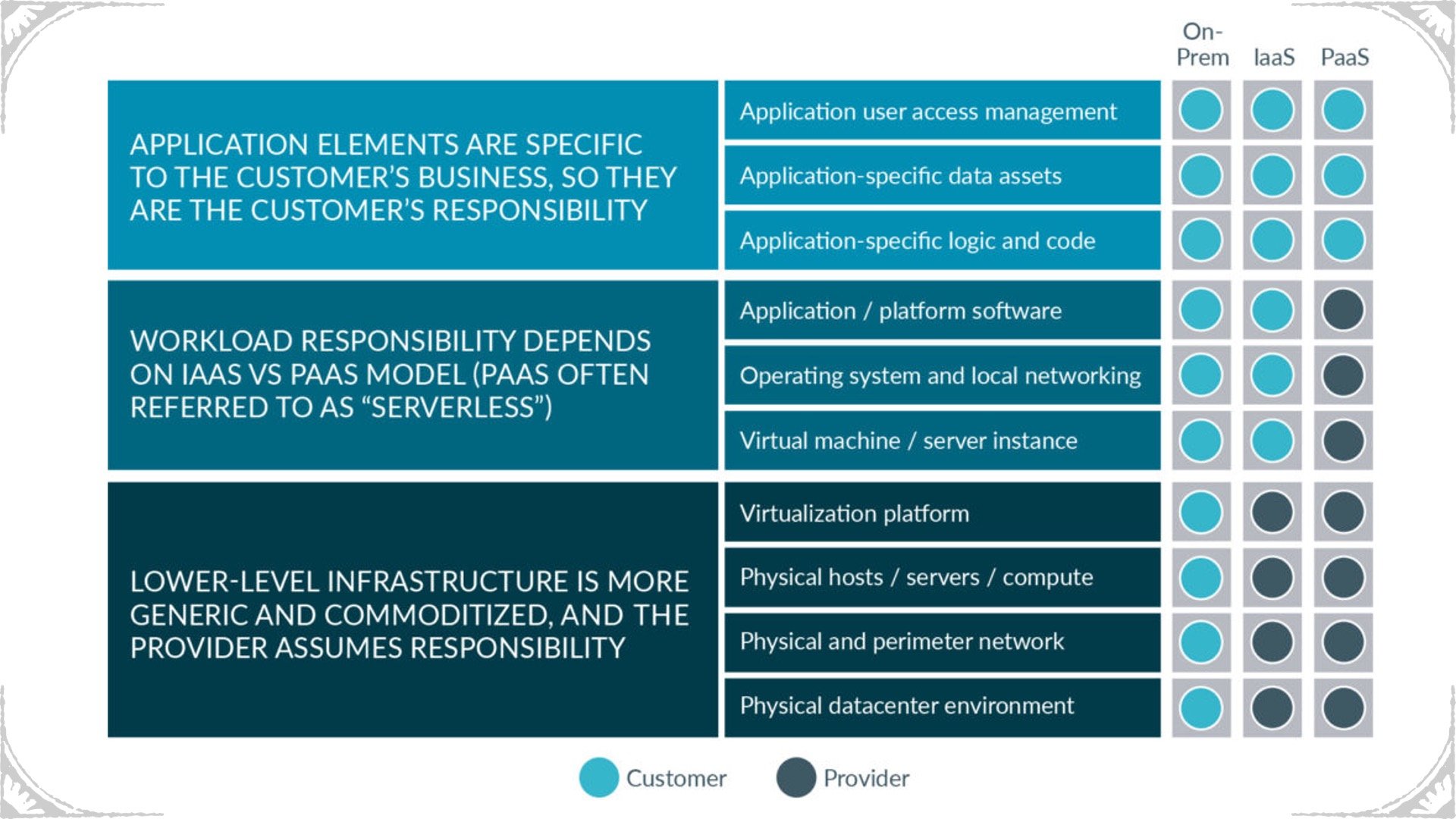
Source: Cloud Security Alliance, Shared Responsibility Model Explained
The majority of organizations have quickly adopted cloud services and moved workloads to providers, such as Amazon Web Services, Microsoft Azure, Google Cloud Platform, and others. The shared responsibility model of cloud security designates that cloud service providers are responsible for protecting the infrastructure that runs all the services offered in the cloud. Meanwhile, the customer is responsible for monitoring risky configurations, anomalous user activities, suspicious network traffic, and host vulnerabilities.
Top Threats to Cloud Computing

Cloud service providers rarely suffer security failures that directly affect all of their customers. However, securing cloud services can be complex, and users often don’t know how to use them securely.
According to the Cloud Security Alliance, some of the top cloud computing threats include:
- Misconfiguration and inadequate change control - When services aren't configured properly, that can lead to data loss, data deletion, or modification.
- Inadequate access management - Cloud services need to be adequately protected with multi-factor authentication and the use of strict identity and access controls, to limit the use of root and admin accounts.
- Account takeover - Attackers are able to take over accounts through phishing attacks or direct compromise of cloud services themselves.
- Insecure interfaces and APIs - API vulnerabilities can give attackers another path to stealing credentials. Organizations need to employ frequent API testing and protect API keys and avoid API reuse.
- Insider threats - Current and former employees, as well as contractors and business partners, can pose risk — even if they don't have malicious intentions. When user behavior and activity isn't monitored, it can lead to more misconfigured cloud servers, sensitive data being publicly accessible, and more.
Why Managing Cloud Security Posture Should Be a Top Cybersecurity Priority Today

Ashish Rajan, producer and host at Cloud Security Podcast, argued that organizations that think maintaining cloud security posture is not important are building their cloud initiatives on a weak foundation. Rajan compared it to building a house with no windows.
He argued that if cloud service providers are giving organizations the tools and capabilities to maintain a strong foundation to build an empire on their data centers, why not use them?
With more organizations moving to the cloud, Rajan believes maintaining a robust cloud security posture is key to protecting their mission-critical information assets, applications, and systems.
Why Managing Cloud Security Posture Should Not Be a Top Cybersecurity Priority Today

David Cass, vice president - cyber and IT risk at the Federal Reserve Bank of New York, argued that although cloud security posture management is important, it’s by no means the number one priority in cloud right now. That’s because when organizations have cybersecurity issues, 80 percent of the time it goes back to getting the basics right.
Cass highlighted five priorities for organizations moving to the cloud. The number one priority is to really understand your business and why you're adopting the cloud, and if it calls for changes in business or technology processes. The second priority is to assess your security and dev teams’ skills and invest in proper training for them when it comes to cloud preparation.
Third, develop a cloud security strategy by mapping existing controls to what's natively available from the cloud service provider. Fourth, identify workloads that are safe to move to the cloud, so you can actually see how those processes are impacted — whether it's change management, patch management, or business processes.
Finally, look at the additional tooling required. Are there gaps that you identified where you're going to need cloud security posture management to help overlay and close some of those gaps?




