What is CTEM? The future of proactive cybersecurity
Axonius

In cybersecurity, the pressure is relentless. Alerts, tickets, vulnerabilities: they pile up faster than your team can triage. One minute you’re patching last week’s issues; the next, a new SaaS app or shadow IT service has popped up on your attack surface.
Most teams, maybe even your own, are stuck in the same loop: chase, patch, repeat. For years, reactive was enough. But in today’s sprawling, cloud-first, hybrid world, it’s not cutting it anymore.
That’s why more teams are shifting to Continuous Threat Exposure Management (CTEM). Recognized by Gartner, CTEM offers a structured, proactive way to scope, discover, prioritize, validate, and mobilize against exposures. Instead of firefighting, CTEM gives your team a repeatable operating model to reduce risk continuously and strategically.
If you’re wondering, “Where do I start?”, this blog covers the essential information and foundational steps your team should know first.
Want the full playbook? Download CTEM for Dummies (Axonius Special Edition) for practical tips, do’s and don’ts, and quick wins to kickstart your program.
The 5 steps of CTEM
CTEM provides a five-step actionable framework for mitigating exposures across your environment. Its goal: help you uncover vulnerabilities, determine priorities, and act decisively to reduce risk.
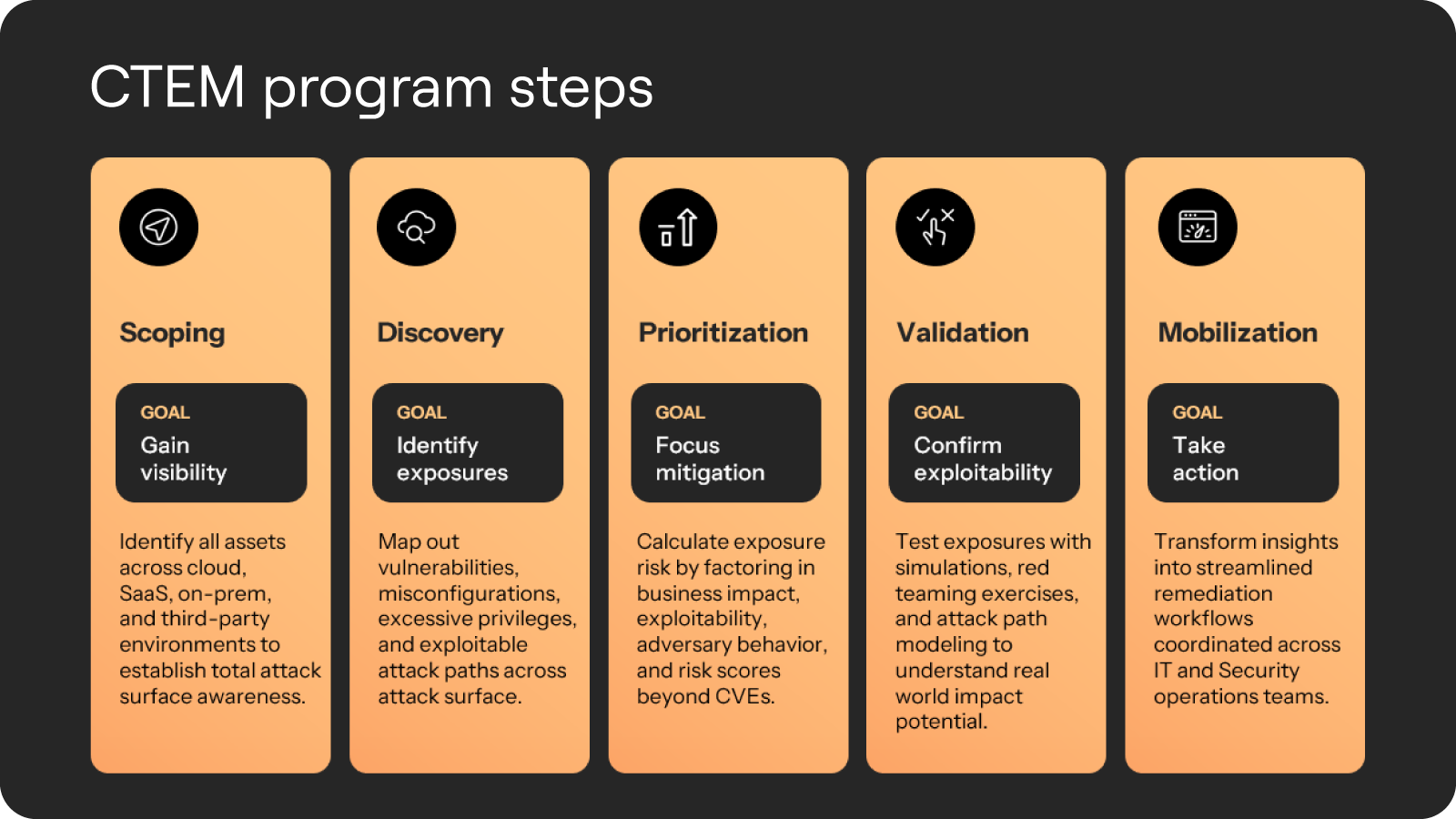
CTEM is built on this repeatable cycle:
1. Scoping: Map the full attack surface across on-premises, cloud, and hybrid environments. Identify all assets to ensure that no blind spots remain.
2. Discovery: Pinpoint vulnerabilities across systems and tools. Uncover hidden risks that might evade traditional monitoring.
3. Prioritization: Ranking vulnerabilities by impact and likelihood is the cornerstone of CTEM. Ensure your team directs their efforts where they will have the greatest effect.
4. Validation: Test and verify that fixes address identified risks. Create feedback loops to continuously refine your security posture.
5. Mobilization: Respond faster by automating workflows and aligning teams to tackle critical threats with precision.
And then? Repeat. Because your environment and the threat landscape never stop changing.
Signs you needed CTEM yesterday
You don’t roll out CTEM just to check a box. You do it because it makes your program stronger and takes real pressure off your team.
If any of this sounds like your day-to-day, CTEM should be on your radar:
Your “asset inventory” is a spreadsheet that’s always out of date.
You’re drowning in alerts with no clear place to start.
Prioritization means fixing whatever issue yells loudest.
Your tools don’t talk to each other.
Shadow IT feels like a constant suspicion you can’t confirm.
Cloud security feels like the Wild West.
Remediation takes forever, if it happens at all.
You’re stuck in firefighting mode instead of prevention.
If even one of these feels familiar, CTEM can help you break the cycle. CTEM for Dummies dives deeper into how to build a strong start.
Golden rules for CTEM adoption
Shifting to CTEM doesn’t happen overnight. Use these tips and think of it as a maturity curve your team climbs step by step:
Start with visibility, not velocity. Make your asset and exposure inventory complete, accurate, and continuously updated across cloud, SaaS, and on-prem. If the inputs are shaky, everything downstream will be too.
Work in short, repeatable cycles. Run the CTEM loop frequently (daily, where possible). Fast feedback beats big-bang rollouts and helps you spot what’s working, and what isn’t, early.
Prioritize by business risk, not scanner noise. Weigh exploitability and business impact alongside CVSS. Crown jewels and exposed paths beat “celebrity CVEs” every time.
Make ownership unmistakable. Define who owns which exposure types, the SLA, and what “done” means (including validation). Write it down and link it in every ticket template.
Scale by proof, not promise. Land visible wins in a focused scope, then expand to more apps, teams, and surfaces once the model is working.
How to address common challenges when implementing CTEM
Fragmented systems
When your tools for vulnerability management, threat intelligence, and incident response are siloed, data gets fragmented. That slows down identification, prioritization, and response.
Solution: Break down silos by consolidating workflows into a unified framework and integrating data into a centralized view your team can actually use.
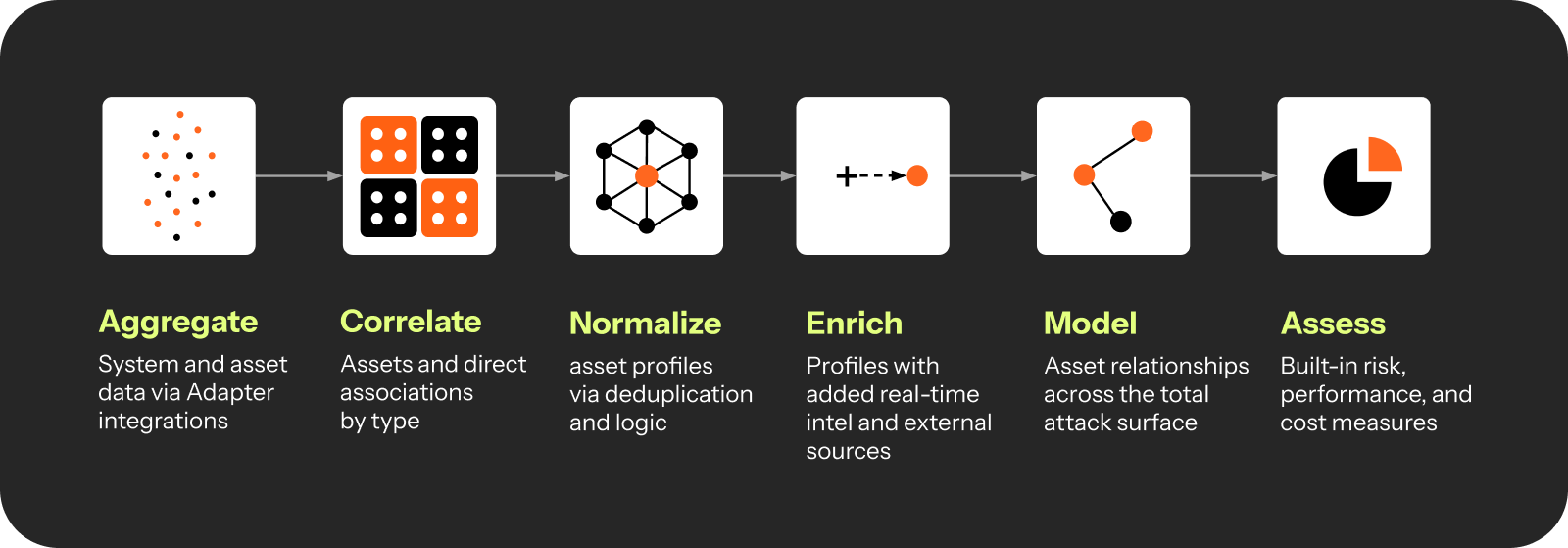
The Axonius Asset Cloud delivers this by aggregating and correlating data from more than 1,200 integrations across 40+ asset types, giving your team a single source of truth for every asset, identity, and exposure.
Blind spots in visibility
You can’t protect what you don’t know exists. Incomplete or outdated asset inventories create dangerous gaps and a false sense of security.
Solution: Build real-time asset visibility by aggregating devices, workloads, SaaS apps, and identities into a single source of truth.
With Axonius continuous discovery and our adapter framework, asset data is deduplicated, normalized, and enriched, ensuring that no gaps or inconsistencies undermine your visibility.
Inconsistent data and noise-driven prioritization
Even when data exists, different formats and siloed reports make it hard to align on priorities. This often pushes teams to chase “celebrity CVEs” or the loudest alerts instead of the risks that matter most.
Solution: Normalize data formats and create a shared context across teams so prioritization happens at the company, site, app, or service level, not just in silos. Axonius unifies asset, security, and business context into a single model.
Our risk score engine combines CVEs, threat intel, exploitability, and business impact, helping your team focus on exposures that truly matter. Dashboards built on this unified context make it easier to explain prioritization decisions.
.png)
Get the guide: CTEM for Dummies (Axonius Special Edition)
CTEM is more than just visibility. It’s about momentum. Every time your team runs the framework, you reduce exposures, eliminate noise, and get a little more breathing room.
Consider this blog your launch pad. For the full guide to building a more proactive approach to cyber risk, download CTEM for Dummies.

Categories
- Asset Management

Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
