How Axonius Helps Identify the New Curl Vulnerabilities CVE-2023-38545 and CVE-2023-38546
Axonius
Last week, in a Github advisory, the maintainers of curl, a popular open-source tool that supports numerous network protocols like HTTP and SSL, announced they would be releasing fixes for two vulnerabilities – one of high severity, CVE-2023-38545, and one of low severity, CVE-2023-38546. Both vulnerabilities affect versions 7.69.0 up to and including 8.3.0 and will be fixed with the release of curl 8.4.0.
In this post, we’ll show you how you can use the Axonius Platform to identify instances of vulnerable versions of curl and understand potential exposure before a vulnerability scan runs.
What Are the Curl Vulnerabilities CVE-2023-38545 and CVE-2023-38546?
CVE-2023-38545 SOCKS5 heap buffer overflow is a high-severity vulnerability affecting curl and libcurl. The buffer overflow could take place during a slow SOCKS5 proxy handshake, which could lead to the corruption of data or the execution of arbitrary code if not patched.
CVE-2023-38546 cookie injection is a low-severity vulnerability affecting only libcurl.
How Can Customers Use Axonius to Identify Systems Impacted by CVE-2023-40477 and CVE-2023-38831?
{% video_player "embed_player" overrideable=False, type='hsvideo2', hide_playlist=True, viral_sharing=False, embed_button=False, autoplay=False, hidden_controls=False, loop=False, muted=False, full_width=False, width='1618', height='908', player_id='139898592021', style='' %}
In the video we show how customers use Axonius to identify instances of vulnerable versions of curl in their environments, lowering their time-to-respond. We’ll also show you how to track vulnerability remediation efforts with dashboards and alert on future vulnerabilities in the Axonius Findings Center.
Using Axonius Dashboards and Field Segmentation Charts
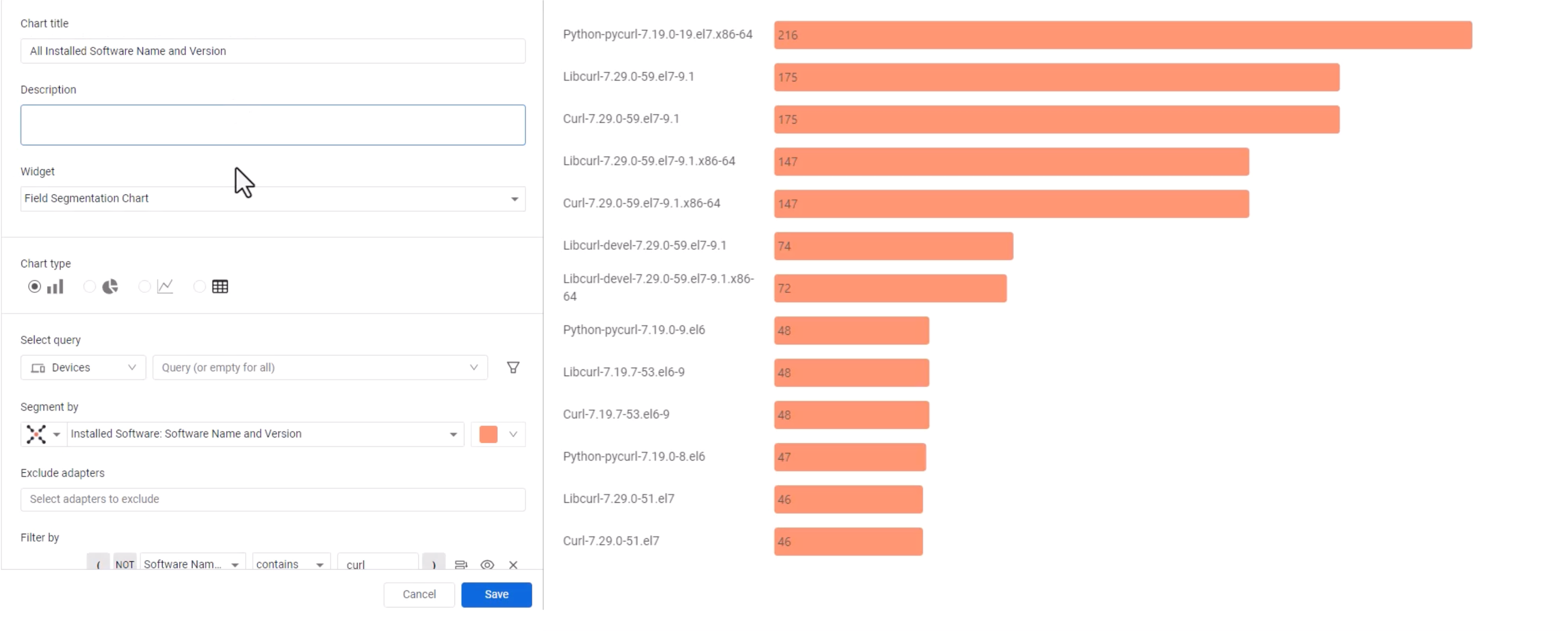
To analyze your potential exposure, customers can use Axonius Dashboards and Field Segmentation chart. The Field Segmentation chart is a single query metric, consisting of a single query and a chosen query field. To identify instances of CVE-2023-38545, we’re going to look for all installed software and versions with a filter on “curl.” The filter option is the equivalent of “contains” in the query wizard.
Once you run the query, you’ll get a chart outlining all installed software within your organizations that contains versions of curl. This will give you a better understanding of the total footprint of the vulnerabilities.
Using Axonius Software Management Module to Identify CVE-2023-38545 and CVE-2023-38546
For a more accurate understanding of your exposure to CVE-2023-38545 and CVE-2023-38546, we can use Axonius Software Management. Axonius Software Management, an add-on within Axonius Cybersecurity Asset Management, helps IT and security teams gain extensive software visibility by delivering a comprehensive inventory of all installed software applications.
In this instance in particular, we can use the module to identify assets with curl affected versions from 7.69 to 8.3.0 and libcurl affected versions from 7.9.1 to 8.3.0. Axonius Software Management correlates software titles to provide a firm asset count and identify potential exposure based on software data. For these queries, we will use the “starts” operator and save our results.
-1.png)
Using the Axonius Vulnerability Management Module to Look for CVE-2023-38545 and CVE-2023-38546
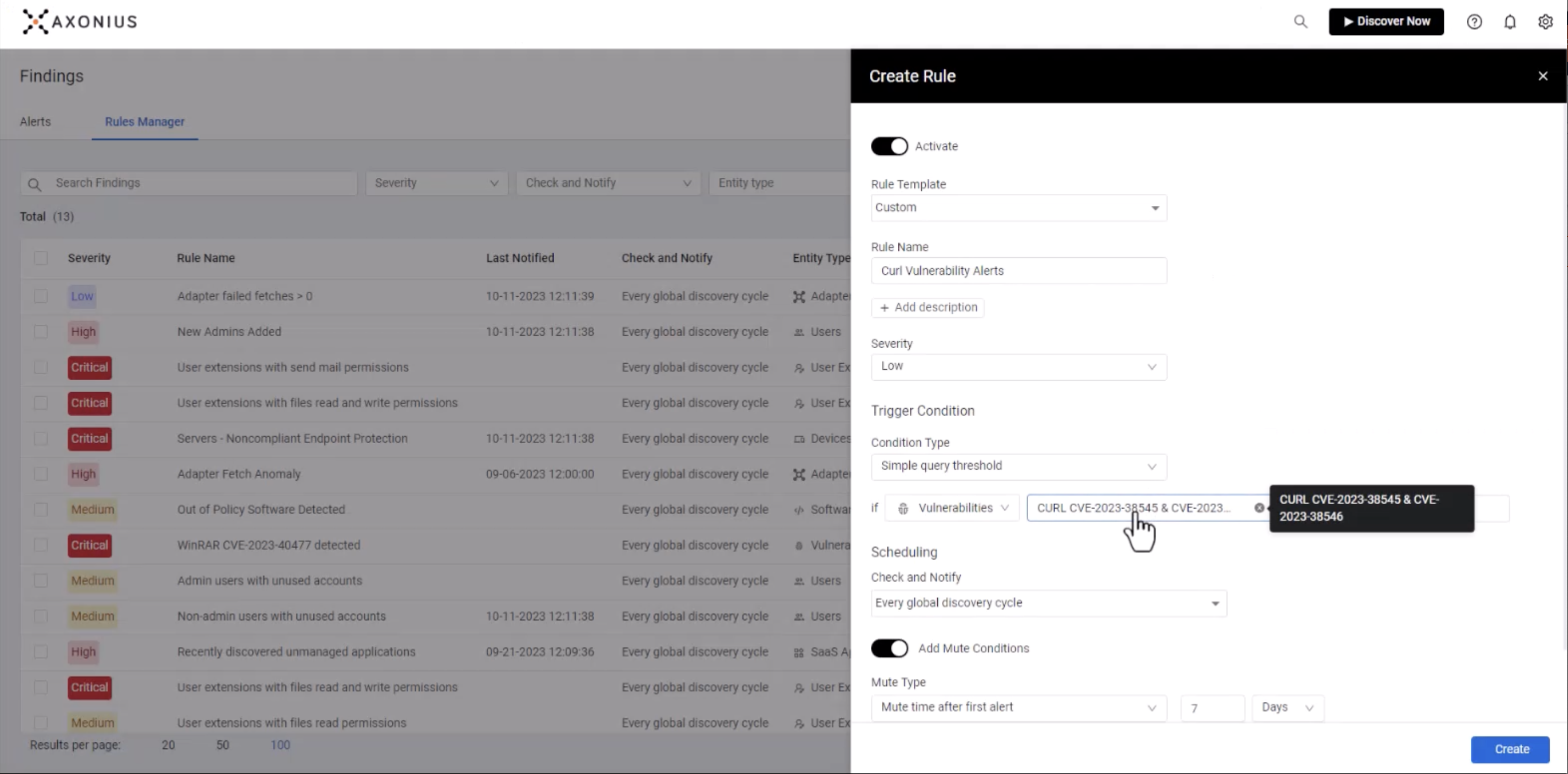
Finally, we can create a custom query with the Axonius Vulnerability Management Module to identify vulnerable versions of curl across devices.
.png)
Using the module, we not only identify unique CVEs and the number of devices that are impacted by that particular threat, but we can get a better understanding of our overall risk exposure.
Once we understand that, we can then set up alerts and leverage the Axonius Enforcement Center to enable “Notify” actions that can help inform your remediation team anytime new instances of affected versions of curl are identified.
For more documentation on using Axonius to find systems impacted by CVEs, visit docs.axonius.com
Categories
- Threats & Vulnerabilities

See Axonius in action
Discover what’s achievable with a product demo, or talk to an Axonius representative.
