How to detect and respond to compromised NPM packages with Axonius
Axonius

The attack surface is growing: not only by the number of assets to protect, but in the variety of places where threats are introduced. One of the most critical examples for security teams is code. In particular, how packages leveraged by developers can introduce risk across multiple assets in your infrastructure.
The recent supply chain attacks to the node package manager (NPM) exemplify the new challenge to security teams: to detect and respond to threats in code, where it’s hosted, and where it's running.
In this post, we'll use Axonius to detect and respond to npm supply chain attacks from two perspectives: from where the code is hosted (repos) and from where the code runs (dev and servers).
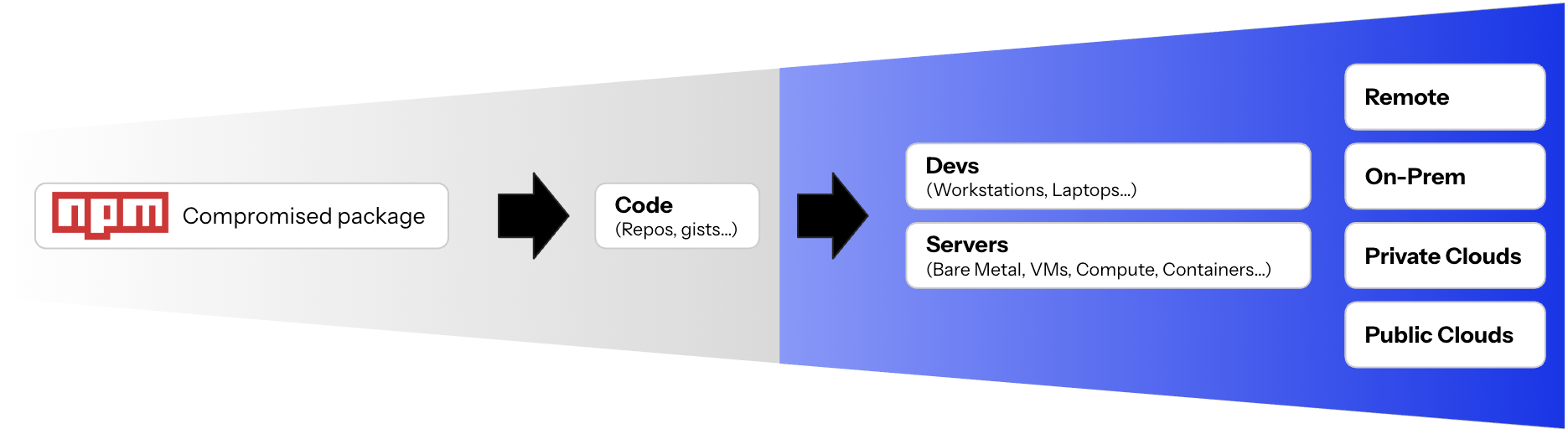
This article should help you detect and respond to compromised NPM packages no matter where your code repo and systems are hosted: remotely, on-prem, in private clouds, and across any public cloud.
For demo purposes, we will use the recent compromises of popular npm packages (like color and chalk) due to a maintainer credential theft, as well as the shai-hulud supply chain worm, as an example of where to look.
1. How to identify code repositories at risk
The Axonius queries below should help you isolate code repositories at risk and track suspicious activities that can be conducted by a compromised package after an import in your code, serving as the baseline for mitigation and remediation at the code repo level.
1.1 Identify code repositories with compromised packages
To identify code repositories affected, go to Application Resources and then search for code repositories in your git servers (GitHub, GitLab, and BitBucket) with the affected packages in their respective or CVE alerts. In this example, we're searching for code repos with packages affected by the .
("specific_data.data.software_cves.software_name" in ["ansi-regex","ansi-styles","backslash","chalk","chalk-template","color","color-convert","color-name","color-string","debug","error-ex","has-ansi","is-arrayish","simple-swizzle","slide-ansi","strip-ansi","supports-color","supports-hyperlinks","wrap-ansi"]) |
Tip: To narrow down your search only to code repositories written in JavaScript or TypeScript, you can add the Languages filter: ("contains.[adapters_data.github_adapter.programming_languages]" in ["JavaScript","TypeScript"])
1.2 Identify vulnerability instances with the affected packages
To list vulnerabilities, go to Vulnerability Instances and then search for the affected packages with their respective GitHub advisory alerts:
(("adapters_data.github_adapter.id" == ({"$exists":true,"$ne":""}))) and ("specific_data.data.software_name" in ["ansi-regex","ansi-styles","backslash","chalk","chalk-template","color","color-convert","color-name","color-string","debug","error-ex","has-ansi","is-arrayish","simple-swizzle","slide-ansi","strip-ansi","supports-color","supports-hyperlinks","wrap-ansi"]) |
Tip: Vulnerability instances provide an itemized view of each vulnerability with a risk score and owner. This view helps you better prioritize what vulnerabilities to address first and which owner is in charge of implementing the remediation.
1.3 Identify suspicious signs of data exfiltration or worm spread
Malware such as Shai Hulud may take advantage of your code repository (through changes in code, code gists, execution of CI/CD pipelines, and new repos) to distribute malware or exfiltrate sensitive data (such as API keys and secrets). Axonius allows you to identify changes in git repositories that may be used for malware spread and data exfiltration.
1.3.1 Repositories and branches created recently (i.e., within the last 30 days)
Malicious actors can use new repositories and branches to spread malware within the existing code or to leverage CI/CD pipelines (i.e., GitHub actions) to exfiltrate data. To find code repositories and branches recently created, go to Application Resources and execute the following query:
(("adapters_data.github_adapter.id" == ({"$exists":true,"$ne":""}))) and ("specific_data.data.first_fetch_time" >= date("NOW - 30d")) and ("specific_data.data.application_resource_type" in ["branch","repository"]) |
1.3.2 Public repositories
Malicious actors can create or change repositories to public to steal IP and exfiltrate data. To identify public repositories within your organization, go to Application Resources and execute the following query:
("adapters_data.github_adapter.private" == false) |
1.3.3 To public gists created recently
GitHub Gists are a simple way for developers to share code snippets, notes, or other small pieces of information. Attackers can leverage this mechanism to leak credentials, API keys, or exfiltrate data. To find out the public gists recently created by your GitHub users, go to Users and run the following query:
("adapters_data.github_adapter.pub_gists" > 0) or ("adapters_data.github_adapter.public_gists.created_at" >= date("NOW - 30d")) |
From the results within each user record, you will get the list of public gists and their respective IDs/URLs.
2. How to identify asset infrastructure at risk
In this section, we will identify computer infrastructure (developer machines, servers, VMs, containers, etc) with indicators (use of nodejs) that may increase the risk of compromise, starting from the least to the most sophisticated filters. Like with the code at risk, you should use these findings as the baseline for mitigation and remediation at the infrastructure level.
2.1 Identify developer machines at risk
To find machines running npm, nodejs, git, GitHub Desktop, or VS Code and used by a user with GitHub, go to Devices and run the following query:
('relationship.users.[656372a7b05058bd0b8886fe]' in ['AQL=(("adapters_data.github_adapter.id" == ({"$exists":true,"$ne":""})))']) and ("specific_data.data.installed_software.name" in ["Git","GitHub Desktop","Node.js","Visual Studio Code","npm"]) |
2.2 Identify cloud server infrastructure at risk (running npm and your applications)
Go to Software and the query below. In this example, we're searching for cloud infrastructure at risk running in GCP, Azure, or AWS. The device filter will search for any compute instance hosted within these providers (inclusive of EC2, Azure VM, containers, and much more). When using this query, change the filter to the cloud providers of your preference.
{"software":"(\"specific_data.data.installed_software.name\" in [\"Node.JS\",\"Node.js\",\"npm\"])","devices":"((\"adapters_data.aws_adapter.id\" == ({\"$exists\":true,\"$ne\":\"\"}))) or ((\"adapters_data.gce_adapter.id\" == ({\"$exists\":true,\"$ne\":\"\"}))) or ((\"adapters_data.azure_adapter.id\" == ({\"$exists\":true,\"$ne\":\"\"})))"} |
2.3 Identify on-prem and private cloud server infrastructure at risk (running npm and your applications)
Go to Software and the query below. In this example, we're searching for compute instances at risk associated with hypervisors (Proxmox, VMWare), server management software (AD), and CI/CD software (Chef) running on-premises or in your private clouds. The device query filter will search for any compute instance identified by these systems (inclusive of VMs, bare metal servers, containers, and much more). When using this query, change the filter to the providers of your preference.
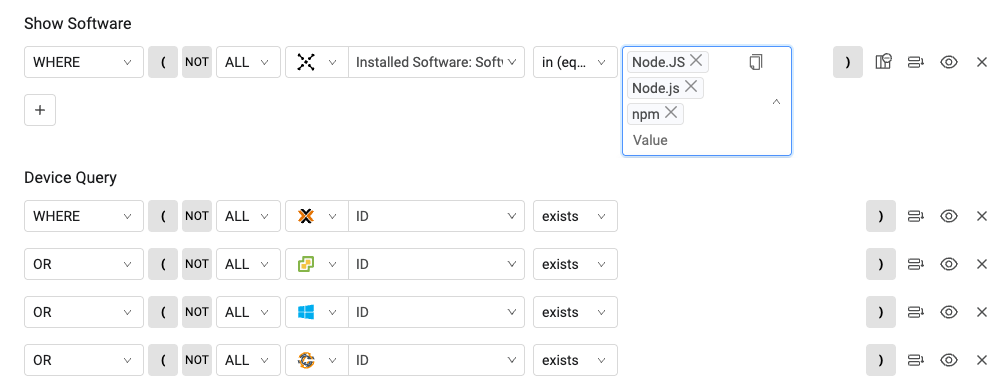
{"software":"(\"specific_data.data.installed_software.name\" in [\"Node.JS\",\"Node.js\",\"npm\"])","devices":"((\"adapters_data.proxmox_adapter.id\" == ({\"$exists\":true,\"$ne\":\"\"}))) or ((\"adapters_data.esx_adapter.id\" == ({\"$exists\":true,\"$ne\":\"\"}))) or ((\"adapters_data.active_directory_adapter.id\" == ({\"$exists\":true,\"$ne\":\"\"}))) or ((\"adapters_data.chef_adapter.id\" == ({\"$exists\":true,\"$ne\":\"\"})))"} |
3. Mitigation and remediation advice
The blog posts for both npm supply chain compromises (, ) listed above provide similar remediation guidance:
At the code repo: - Check the package versions you are using - Make sure you use a package lock file with pinned package versions. - Monitor logs for unusual npm publish or package modification events. | At the asset infrastructure: - Clean your npm cache - Reinstall all packages - Audit environments (CI/CD agents, developer laptops) that installed the affected versions for unauthorized publishes or credential theft. - Rotate npm tokens and other exposed secrets if these packages were present on machines with publishing credentials. - Monitor logs for unusual npm publish or package modification events. |
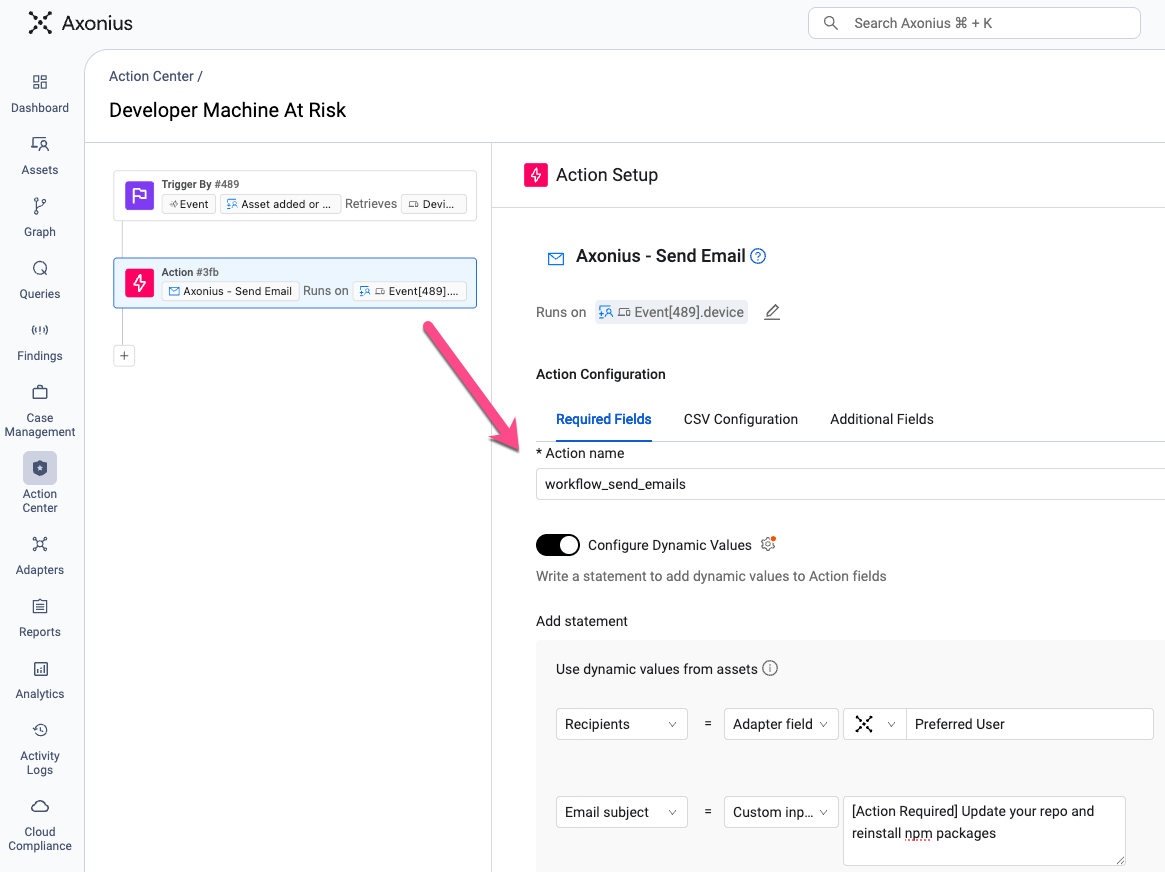
To accelerate alerts and remediation with Axonius, use the queries from 1. How to identify code repositories at risk and 2. How to identify asset infrastructure at risk to trigger automatic investigation, remediation, and action. For example, whenever a new developer machines at risk is identified, you can automatically alert the developer to take corrective measures or trigger a remote process to ensure they are working with a safe code base.
Learn more
External resources:
Questions on scope and impact of npm malware advisories (2025-09-09)
Socked.dev: Ongoing Supply Chain Attack Targets CrowdStrike npm Packages
Axonius resources:
If you're not an Axonius customer and want to know more about how we can help you, schedule a meeting with a security specialist.
Categories
- Threats & Vulnerabilities
- Software

Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
