Launch Week 2026: Managing software risk starts here

Amir Lazevnik
Principal Product Manager, Axonius

Josh Donelson
Principal Product Marketing Manager, Axonius

It’s something we hear from our customers all the time: security practitioners are finding it more important than ever to manage software risk in their environments. Industry research backs this up, showing an increase in both the number of reported vulnerabilities in software packages and the number of exploited software vulnerabilities.
Software-related vulnerabilities rose 61% from 2023 to 2024 (4,202 to 6,761).
Actively exploited software-related vulnerabilities rose 96% from 2023 to 2024 (101 to 198).
Helping our customers get ahead of these trends is why we’ve continued to evolve Axonius Software Assets. We recently launched the Software Management Workspace in Axonius to help operators accelerate the build-out of the practice, along with the Software Registry, a policy management view for software within that practice.
Let’s take a look at these two critical pieces of the Software Assets product to see how they work together to help enterprises expand risk management to include software, accelerate detection and response, and keep the business safer overall.
Building a practice: The Software Management Workspace
It can feel overwhelming to connect the many aspects of installed software into a cohesive risk management strategy. Not only do you need to know what’s installed in your environment, but you also need to link that to users, devices, and use cases, and track usage over time.
The Axonius Asset Cloud, powered by the Adapter Network, is the foundation for gathering all of this data. We heard our customers loud and clear that just having all this data isn’t enough: you need to turn data into actionable information.
Enter the Software Management Workspace.
The Software Management Workspace is the result of many hours of customer interviews, along with input from our technical teams, to understand which insights are most valuable to security teams. It’s designed to be the jumping-off point teams need to get their arms around software in the environment, from discovery and inventory to risk visualization and remediation tracking.
First, solving the discovery problem:
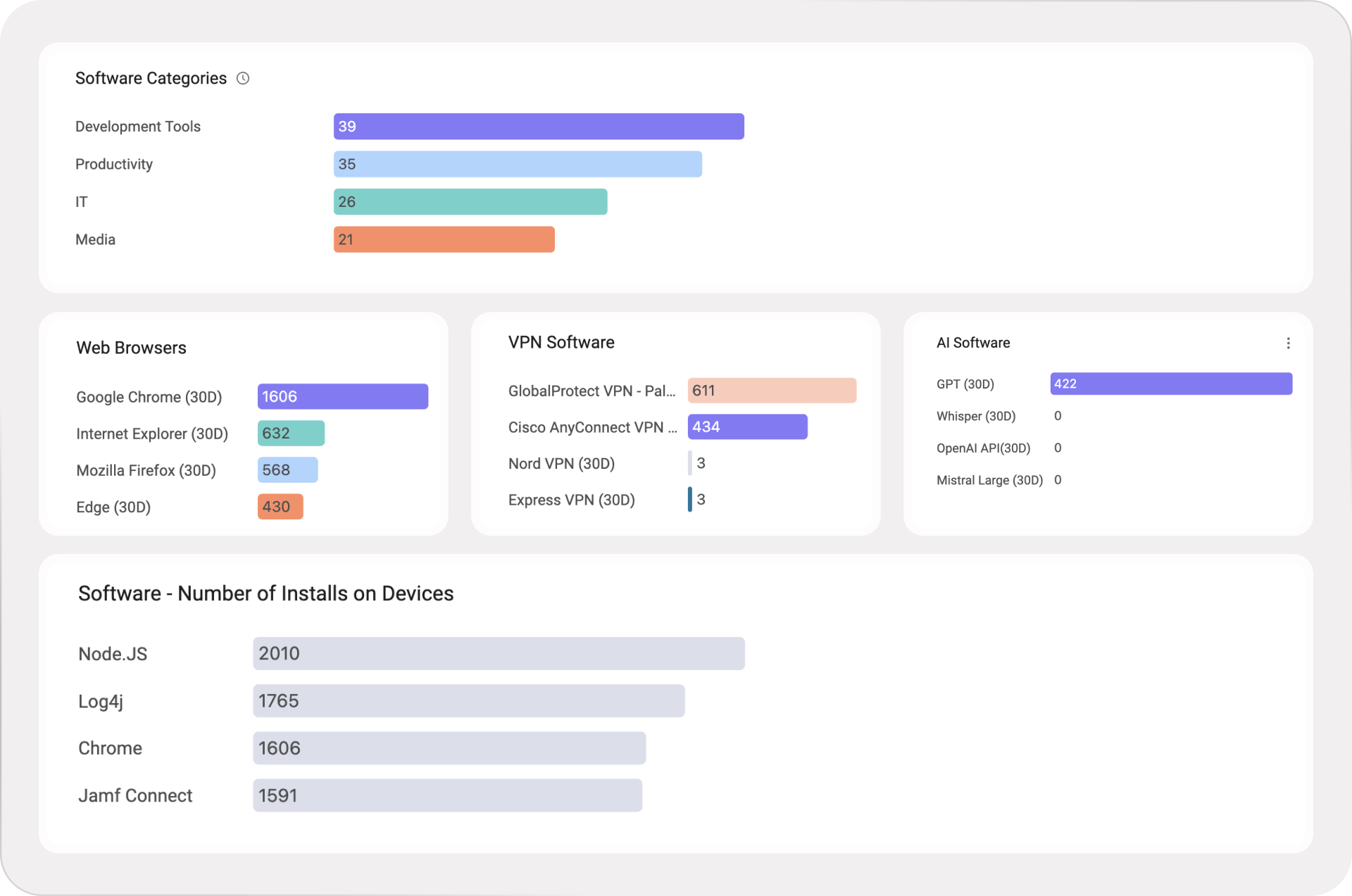
Software categories: What types of software exist in my environment, and how common is each category?
Category breakdown (web browsers, VPN software, AI software): Which specific software titles show up in each category, and how widely are they deployed?
Installs across devices: Which software titles have the highest footprint across my device estate?
Next, to start managing risk, we look for deviations from the norm, including edge cases where software is outdated or rarely deployed:
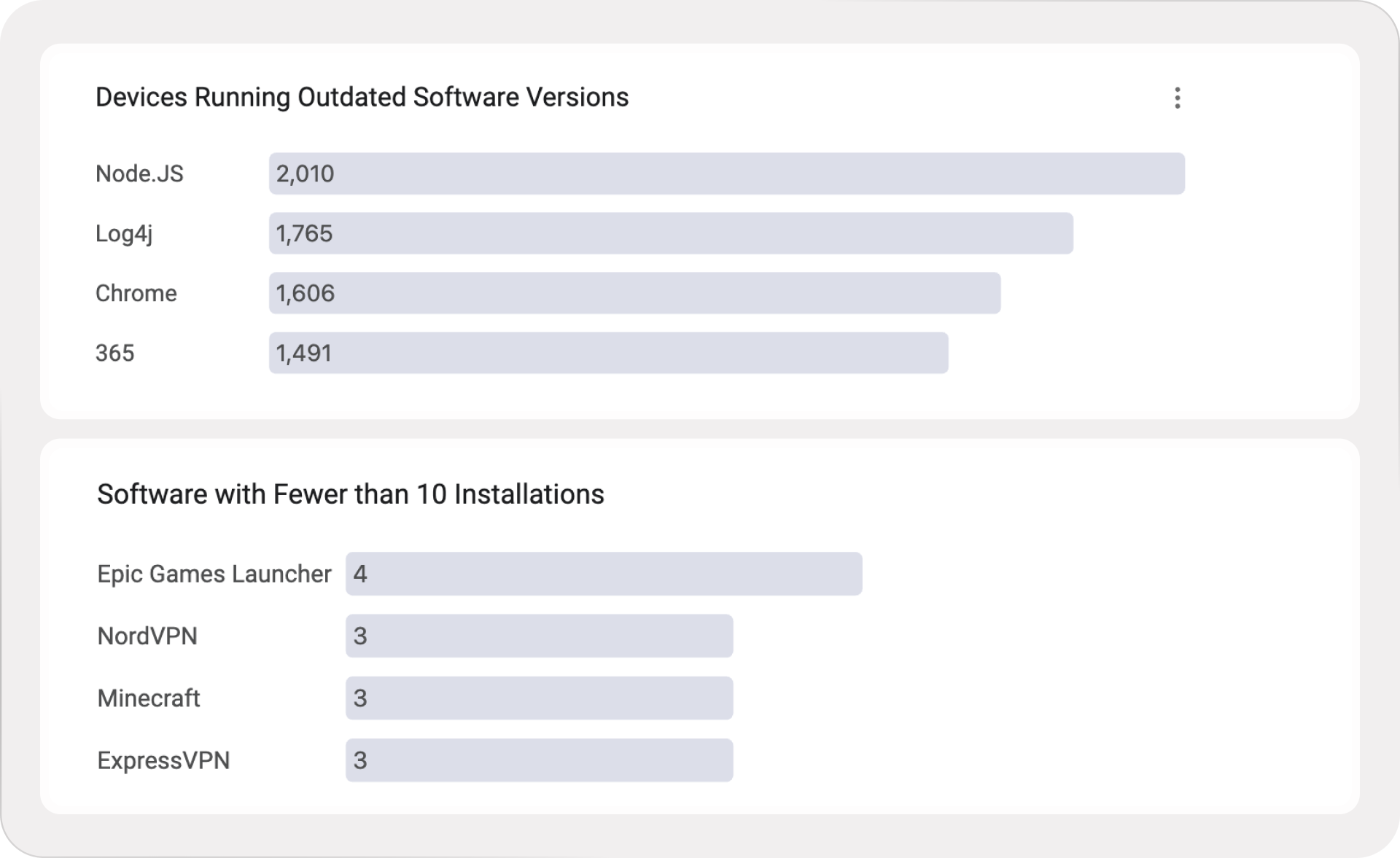
Devices running outdated software versions: Which software titles are running outdated versions, and how many devices are affected (by version)?
Software with fewer than 10 installations: Which software titles have very low deployment across the environment?
Another useful view of this aggregated discovery data is the ability to prove that certain software titles are not installed in your enterprise. Demonstrating to internal and external stakeholders that no crypto miners or game servers are running is often a compliance requirement.
One of my colleagues said the following about the Software Workspace the other day: “Don’t build anything — just look!”
And all of these out-of-the-box reports are fully extensible. Want to see software in use over the last 60 days instead of 30? Want to prioritize visibility into installed AI packages? Need to better understand the types of devices using a certain piece of software? Start with Axonius built-in reports and then build custom dashboards to drill into your specific requirements.
Operationalize your software risk policies
After digging into the Software Workspace, many readers are likely asking the next logical questions about enforcement. Showing a list of old software versions in your environment is great, but what you really need to know is whether those versions introduce risk. And detecting all installed software is great, but what matters is whether that piece of software is in compliance with corporate risk policy.
Axonius invests heavily in what we call the Software Catalog. This is the behind-the-scenes repository of software titles, End-of-Support and End-of-Life status, and versions that our data team continuously invests in. This catalog is what helps drive the correlation of various software information: for example, knowing that Node.js might have a vendor name associated with it such as OpenJS Foundation, node.js, nodejs, or Node.js Foundation.
Where the Software Catalog is built and maintained by Axonius, the Software Registry is built to be an extension of the software catalog, populated by customers in order to power policy enforcement for software risk. Notably, the Registry can include software titles that have been discovered in your environment, and it can also contain software titles not currently discovered, which allows risk managers to build detections for future risk scenarios.
Lastly, the Software Registry powers Approval Status detections of software in your environment. Approved or Unapproved tags can only be added to Software Titles or Software Versions in the Software Registry, as these tags must come from your internal risk management practices. Together, the Software Catalog (Axonius-built) and the Software Registry (customer-built) form a complete view of detected software and associated metadata to help you decide what to do once you’ve discovered what you have.
Let’s look at two specific causes of software risk in your environment, and how the Axonius Software Management Workspace with the Software Registry helps you tackle them.
Use case: “Shadow” software
Shadow software is any unknown software running in the environment. At best, it’s an annoyance. At worst, it’s an open back door for attackers.
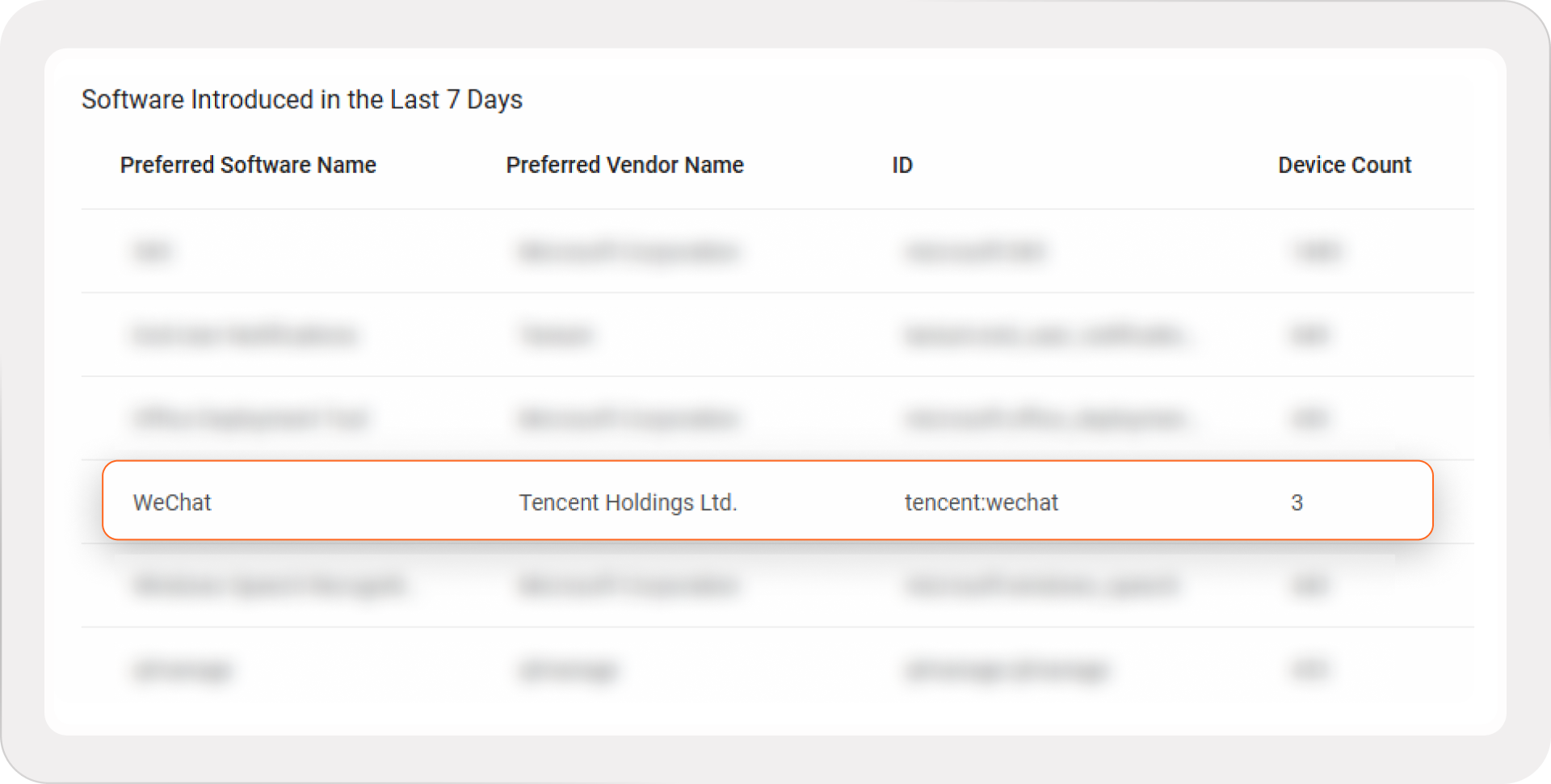
The very nature of the Axonius Asset Cloud makes it the ideal discovery method for shadow IT. Any software title that’s reported by any Adapter in your environment will be immediately available to administrators and operators. With robust Approved / Unapproved metadata in the Software Registry, it becomes easy to immediately:
1) Identify software that’s been recently added to the network.
2) Determine if it should be there or not.
Use case: Software that is out of support
Patching is one of the most important ways to reduce software-driven security risk. In fact, we built a different Workspace specific to accelerating “Patch Tuesday.”
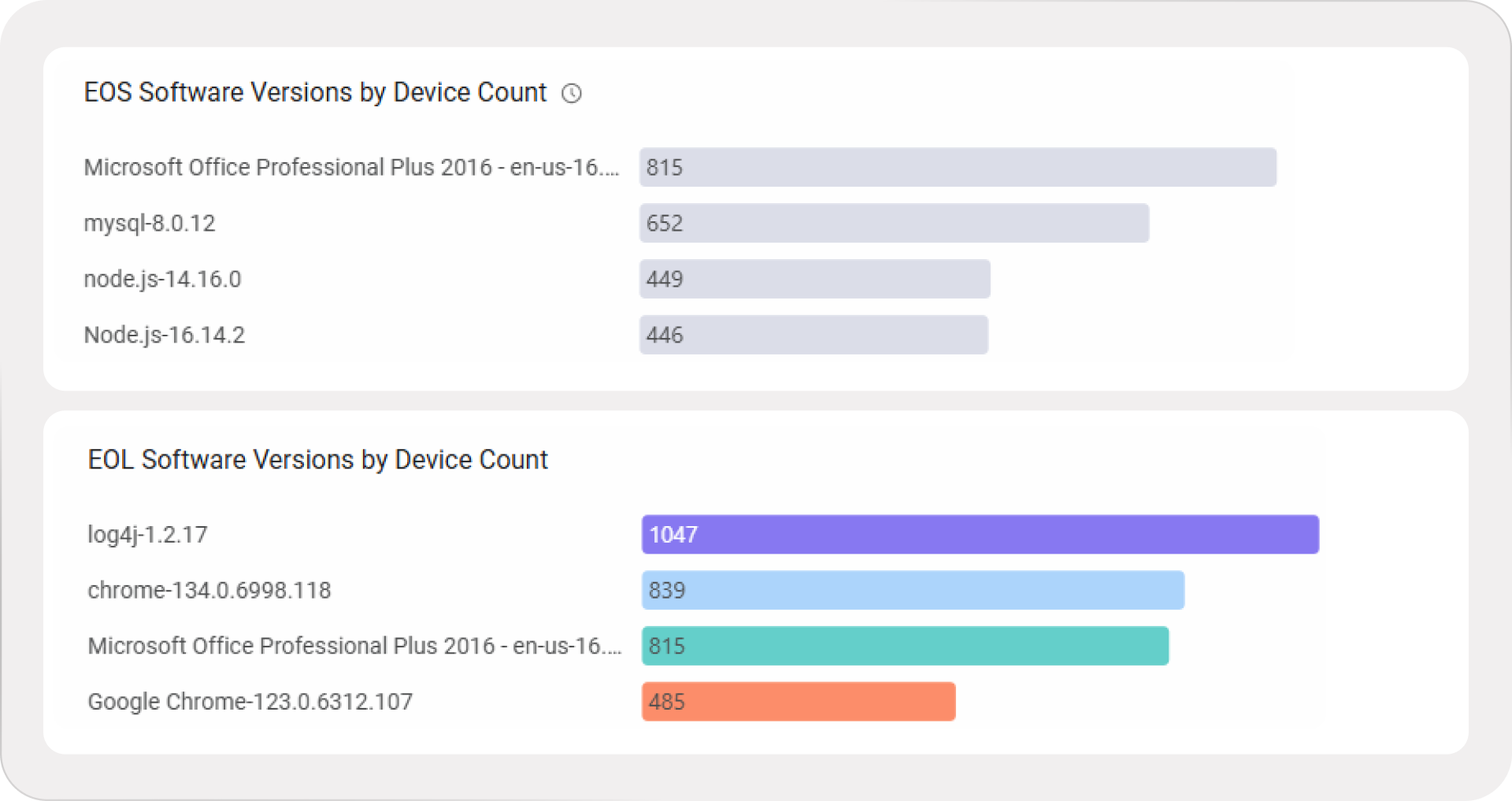
In the Software Workspace, it’s straightforward to track which software versions are installed across the enterprise. The next step is policy enforcement, including a requirement that software stays within the vendor’s support window. The challenge is having the visibility and context to know which installed versions are End-of-Support.
Axonius transforms this chaos into action. By cross-referencing all versions of installed software tiles (available out-of-the-box in the Software Management Workspace) with End-of-Support metadata in the Software Registry, teams can quickly identify risky versions, see where they’re installed, and understand who owns the affected devices and the software title.
Having this metadata at your fingertips makes it easier to justify a ticket to the software or device owner and speed up any required updates.
Actionability for software risk
We’ve seen how the Software Management Workspace helps jumpstart the practice of reducing software risk, and how the Software Registry extends Software Asset information available natively in the platform. The Axonius Enforcement Center then turns those insights into action, with three response flows based on three different levels of identified risk.
Scenario 1: Operationalizing risk via ITSM integration
For teams beginning to bridge the gap between discovery and remediation, the first step is ensuring software risk doesn't live in a silo. Using the Axonius Enforcement Center, you can automatically trigger a ticket in platforms like ServiceNow or Jira the moment software enters a risky state, such as reaching End-of-Life or being identified as a shadow application.
Because Software Assets correlates application metadata with the specific device, owner, and business unit, the ticket lands in the help desk or SecOps queue with the necessary context already populated. This eliminates the "janitorial" data gathering usually required by incident management teams, allowing them to schedule the update or removal without a manual investigation phase.
Scenario 2: Progressive user engagement and escalation
Not every risky application requires a heavy-handed response, but every risk requires accountability. Axonius allows you to build a nurture-style remediation workflow that starts with the end user.
You can configure an Enforcement Set in the Axonius Action Center to send an automated Slack or email notification directly to the employee who has the unauthorized software installed, explaining the policy violation and providing a self-service path to removal. With the Software Registry’s metadata, the message can be specific: "The version of App X on your machine is no longer supported."
Axonius Workflows also allows for tremendous flexibility downstream of any action. For example, you could add a step so that if the user ignores a set number of warnings within a defined window (say, 72 hours), Axonius automatically escalates by flagging the software for forced removal or notifying the IT manager. This reduces the burden on security practitioners while maintaining a "soft touch" for corporate culture.
Scenario 3: High-urgency automated response and orchestration
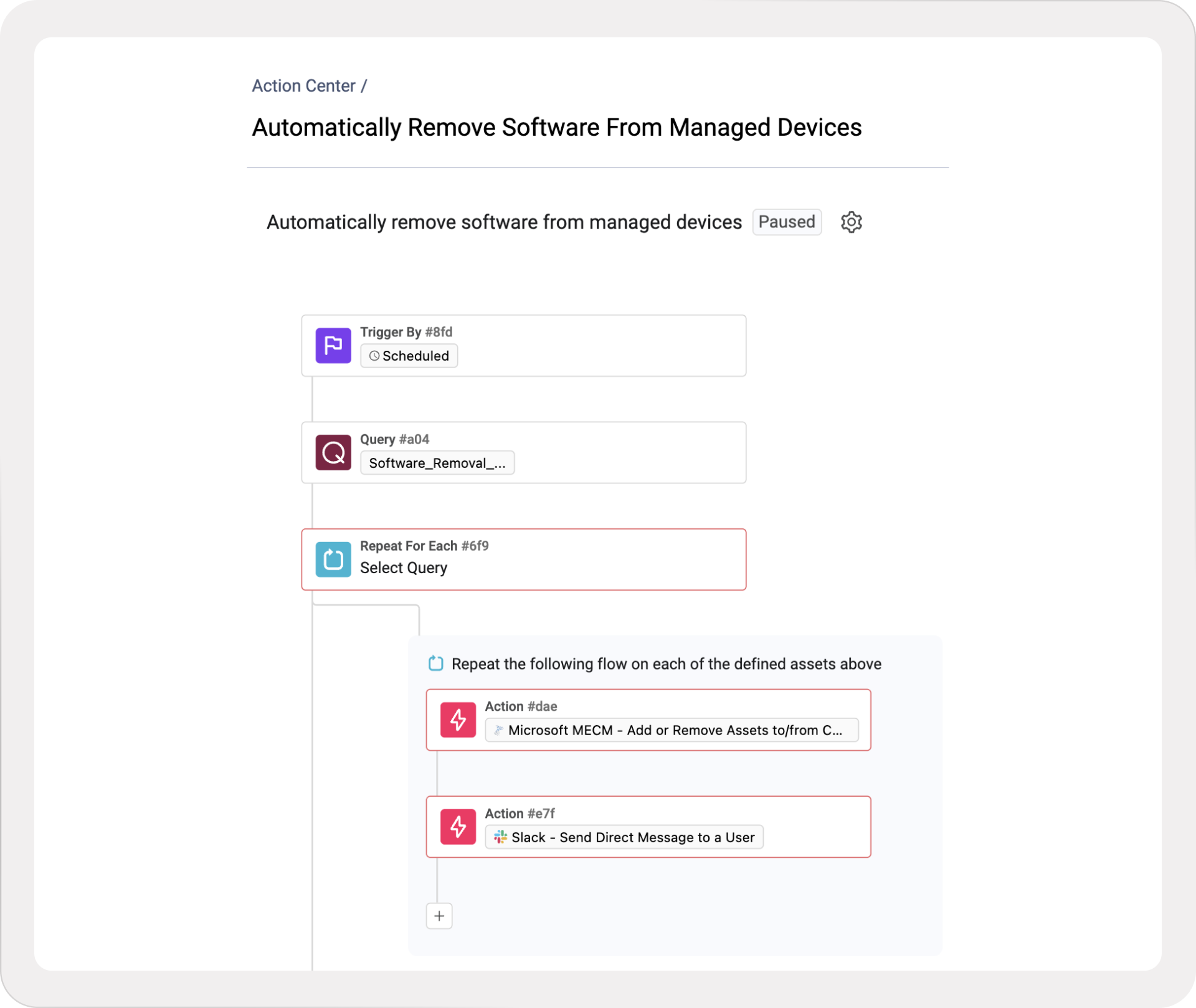
When the risk is critical, such as an application with a known exploited vulnerability or a high-severity configuration gap, the Axonius Asset Cloud supports immediate action to contain the blast radius.
In this scenario, you can build a workflow in the Axonius Action Center to command Microsoft Endpoint Configuration Manager (MECM) to uninstall the offending software from the specific machine instantly.
Simultaneously, the workflow could trigger an emergency notification to the security engineering team and log the action in the asset's history to create a defensible audit trail. Because Axonius correlates the software, device, and user identity, teams can act with precision and neutralize the critical risk in minutes rather than days, without leaving the Axonius console.
From inventory to action
Risk from installed software is one of the fastest-growing categories of risk. Traditional software asset management tools aren’t designed to manage risk, and even the basic task of inventorying what’s installed across your enterprise can be challenging.
The Software Management Workspace, the Software Catalog, and the Software Registry in the Axonius Software Assets module are purpose-built to help turn chaos into predictable software risk management.
Ready to dive deeper?
Categories
- Asset Management

Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
