Launch Week Day 3: Identities in Action

Julissa Caraballo
Principal Product Marketing Manager, Axonius

Launch Week Day 3 – Redefining Identity Governance for the Modern Landscape
For years, identity governance has struggled to keep up with the pace of change. Built for static environments and centralized infrastructure, traditional IGA tools rely heavily on brittle group logic, manual provisioning, and inflexible role hierarchies. In today’s hybrid, SaaS-heavy IT environments, these systems have become more of a bottleneck than a safeguard.
The result is a governance experience that’s often disconnected from operational reality – bloated access roles, inconsistent visibility, certification campaigns that burn out teams, and governance programs that are more reactive than preventative.
We launched Axonius Identities to bring a modern approach to identity lifecycle and access governance – one rooted in data, automation, and continuous alignment. And the response has been clear: the market is ready for something different.Today’s launch showcases new capabilities that continue to push the envelope: Entitlements Consolidation, Automatic Rule Revocation, Entitlement Assignments, and AI-Powered Profile Recommendations.
Entitlements Consolidation
Axonius Identities now helps you consolidate entitlements that grant the same underlying access – even when they’re defined differently across apps, groups, or systems. By visualizing clusters of functionally equivalent permissions using permission semantics, application metadata, and usage patterns, Axonius makes it easy to spot redundancy and normalize access into unified entitlement definitions. The result is cleaner governance, faster access reviews, and consistent policy enforcement across fragmented environments.
How it Works
Axonius continuously analyzes identity and access data across connected systems, going beyond surface-level permission names to understand the actual effect of each entitlement. Whether access is granted through a group in Azure AD, a role in Salesforce, or a direct permission in a SaaS app, Axonius identifies and clusters those grants when they provide the same functional access.
Teams can explore these clusters visually, validate consolidation recommendations, and apply updates to eliminate overlap – all without writing custom logic or breaking necessary access.
Entitlements in Action
Right-sizing overgrown access: Collapse redundant groups, roles, and direct grants into a single, appropriate entitlement.
Simplifying access reviews: Reduce noise by treating similar access as one logical item.
Refactoring legacy roles: Normalize app-specific permissions (e.g., GitHub, Salesforce, Workday) to align with broader policies.
Designing anchor policies: Eliminate over-entitlement by identifying and consolidating unnecessary overlaps.
By turning fragmented access into unified building blocks, Axonius enables a more scalable, policy-driven model of identity governance – one rooted in truth, not tribal knowledge.
To learn more about Entitlements, see the Docs about the underlying data model.
Automatic Rule Revocation
Axonius Identities now includes new guardrails and controls that make real-time access revocation safer, more precise, and fully auditable – dynamically removing entitlements the moment a human or service account no longer meets defined policy conditions.
How it Works
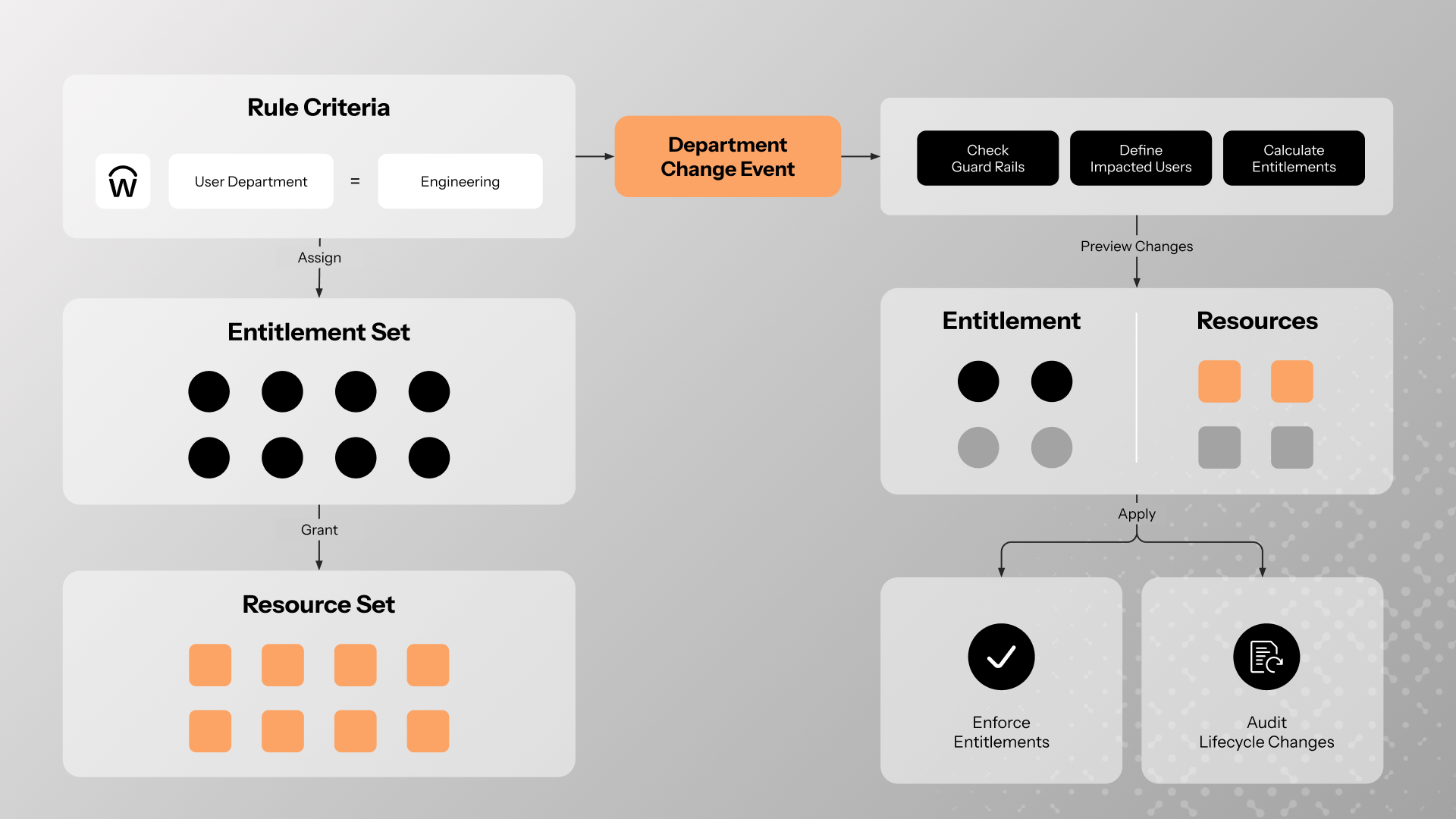
Dynamic rules can be built using identity attributes (like department, location, or employment status), contextual signals (like app activity or asset posture), and time-based triggers (like contract end dates or project milestones). Axonius continuously evaluates these inputs in real time, and when any signals change, we recalculate access and directly revoke the respective entitlements across connected systems.
In this model, Axonius becomes the active enforcer of governance decisions across your environment. That power demands precision and confidence. That’s why we now include built-in guardrails to ensure that enforcement is deliberate, scoped, and accountable:
Preview Mode to simulate rule impact before activation
Exception Workflows for safe, auditable overrides
Scoped Enforcement to target specific systems, roles, or users
Rule Revocation in Action
Immediate cleanup after org changes: No more lingering access when roles change or users depart
Operationalizing least privilege access: Enforce policies continuously without waiting for periodic reviews
Securing temporary access: Automatically revoke entitlements when project or contract timelines expire
Cross-system governance coordination: Ensure policies are applied uniformly across identity providers, SaaS apps, and infrastructure systems
Why Rules are a Paradigm Shift
Unlike traditional identity lifecycle management solutions, which are limited to the policy boundaries it understands, Axonius acts as a true enforcer across your entire environment. Because we understand the policy and permission model of every connected system, Axonius can detect violations and orchestrate revocation wherever the access lives – bringing total lifecycle orchestration to the full identity fabric.
Learn more about Automatic Rule Revocation in the Docs.
Direct Entitlement Assignment
Even in a world of more automated governance, some situations demand a more hands-on approach. Axonius Identities allows administrators to manually assign entitlements directly from the UI, without disrupting the broader policy-based framework.
How it Works
From the Axonius Identities console, administrators can:
View all human and non-human identities and their respective entitlements
Manually assign, modify, or revoke access for any given identity to any connected system
Provide contextual justification for auditability
Direct entitlement assignments are fully tracked, auditable, and can be integrated into downstream certifications or access review workflows. This hybrid approach ensures flexibility without compromising policy enforcement or system integrity.
Entitlement Assignment in Action
Granting temporary access for project-based needs, incident escalations, or new joiners waiting on automation
Handling exceptions for sensitive roles or users outside standard policy logic
Investigating and correcting anomalies uncovered during access reviews or threat hunts
Responding in real time when urgent access changes are needed before a rule update can be deployed
This flavor of manual assignment doesn’t replace automation, it complements it. Axonius gives you the flexibility to step in when needed, without losing consistency, context, or control.
Learn more about Entitlement Assignment in the Docs.
AI-Powered Profile Recommendations
Applying AI to identity governance only works if the underlying data is complete, correlated, and accurate. That’s why Axonius built a purpose-built identity data pipeline that ingests, normalizes, and maps identity artifacts across every system – including identity providers, SaaS apps, cloud platforms, and on-prem infrastructure.
By resolving fragmented records and calculating effective permissions across roles, groups, and entitlements, Axonius creates a unified identity model – the ideal substrate for AI to deliver meaningful insights.
Now, we’re leveraging that foundation to power AI-driven recommendations that help reduce access sprawl, optimize policy enforcement, and accelerate governance decisions.
How it Works
At the core of this system is the Axonius Profile – a dynamic, correlated unit that represents both an identity and its full entitlement context across systems. Profiles serve as the basis for defining and enforcing access policies via Rules.
To power governance at scale, Axonius uses AWS Bedrock foundation models alongside proprietary AI logic to analyze the unified identity graph, enriched with full context around accounts, entitlements, group memberships, usage behavior, and system relationships.
Because Profiles reflect calculated effective permissions, not just raw assignments, AI can reason about access patterns in context, and generate precise, scalable governance recommendations grounded in operational reality.
Profiles in Action
Rule Suggestion & Role Mining: Identify recurring access patterns across users and recommend rule logic to support least privilege enforcement.
Entitlement Clustering: Detect and group functionally equivalent entitlements across disparate systems for cleaner policy modeling.
Behavioral Insights: Surface dormant access, privilege anomalies, and outlier behavior based on actual usage patterns to inform policy cleanup or revocation.
These recommendations are surfaced directly in the Axonius UI, allowing administrators to validate suggestions or integrate them into broader lifecycle and certification workflows.
Behind the scenes, AWS Bedrock provides the scalable, secure foundation for model inference, while Axonius layers on its domain-specific logic, access modeling, and real-time system integrations to deliver identity-specific precision.
Learn more about Profiles in the Docs.
Wrap Up: Take Action with Axonius Identities
Identity governance has long been bogged down by fragmentation, manual effort, and tools that can’t adapt to today’s dynamic environments. With these new capabilities, Axonius Identities pushes governance into the actionability era, so you can:
Normalize fragmented access across systems into unified, policy-ready entitlements
Enforce dynamic policies in real time, with built-in guardrails for safe, scoped revocation
Support hands-on control for edge cases without compromising governance integrity
Use AI to mine roles, suggest rules, and optimize policies
With a unified identity model and policy engine at its core, Axonius is redefining what’s possible in modern identity governance.
More from Launch Week
See all the action for Launch Week here.
- Platform Actionability: make actionability a reality with workflows, ticket binding, and 500+ actions
Exposures in Action: turn findings into automatic fixes at scale.
Actionable UX Enhancements: a fresh look and feel for the Axonius console and API.
If you’re new to Axonius, book a demo to see Identities in action for yourself

Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
