The 2026 Axonius Actionability Report: 5 decision-grade insights in asset intelligence

Ivan Dwyer
Product Marketing, Axonius

Actionability means different things to different people. For some, it's faster remediation. For others, it's fewer handoffs, cleaner prioritization, or proof that the fix actually worked. What everyone agrees on: visibility alone isn't the finish line.
We partnered with the Ponemon Institute to study how security teams turn asset and exposure data into meaningful action. The research surfaced patterns that separate organizations making progress from those spinning their wheels. Here's what stood out and where we see the opportunity.
The findings cluster around five pillars: Collection, Coverage, Context, Containment, and Cooperation. Each tells its own story, but they share a common thread and a common affection for wordplay. It might be the last thing separating us from the machines. Come see for yourself.
Read the full report for more in-depth research and insights: Get the 2026 Axonius Actionability Report.
Collection: Building the control plane mid-flight
By now, we’ve all been conditioned to the sentiment popularized by AWS – building the plane mid-flight. Of course, data work is never done, but with security data, the caution is relying on stale, conflicting, or even missing data for critical security decisions.
Our research found that only 45% of organizations have consolidated asset and exposure data into a single view. But it’s the flip side to that group that’s more illuminating: building brittle visibility infrastructure while simultaneously trying to use it for critical security decision making.
When 55% of the people we surveyed use some form of spreadsheets or home-grown scripts to track assets and exposures, we know there’s an opportunity to get more current and more accurate.
Our take is to align on a universal source of truth that every cyber program, team, and system depends on. This level of visibility must elevate above any one system or domain. You have a lot of tools that provide the right compensating controls for the right reasons – endpoint protection, network security, cloud security, identity & access management – the list goes on.
Keep that up, just wrap your entire stack in a unified visibility layer that can handle all of the discovery, correlation, and normalization in one place. Trying to reconcile assets and exposures through silos, spreadsheets, and scripts won’t get you to your destination safely.
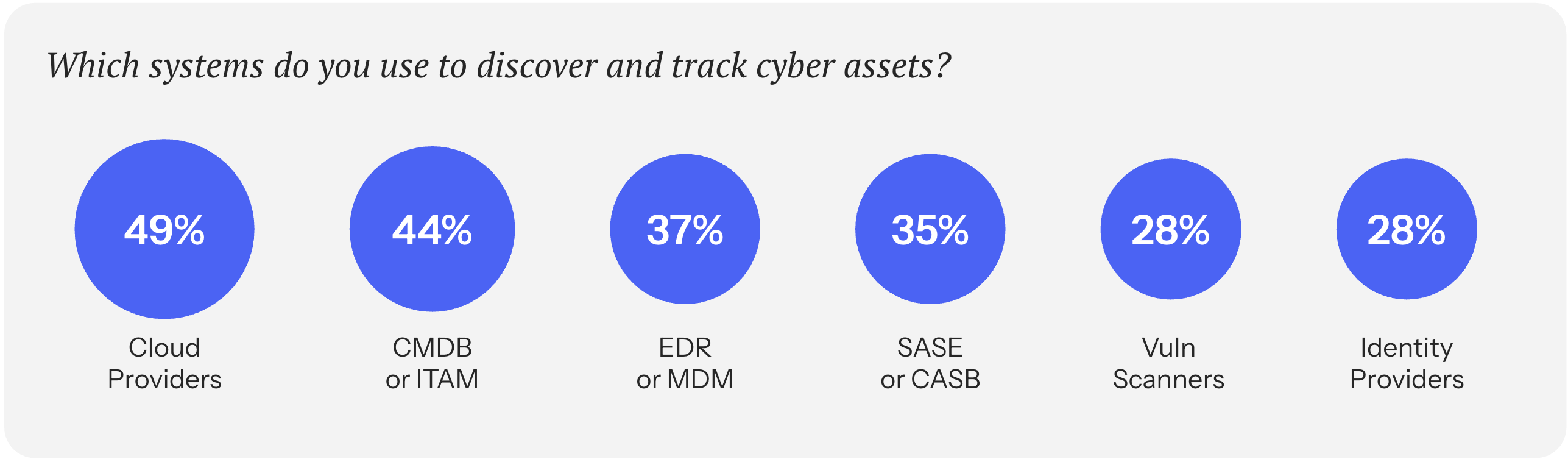
Axonius makes collection automatic and continuous. We connect with over 1,400 data sources across your stack – cloud, endpoint, identity, SaaS, infrastructure, and more – to reconcile every asset and exposure into a single fabric. No scripts to maintain. No spreadsheets to merge. Just a continuously updated model of what you actually have – its state, location, and owner.
Coverage: Make an asset out of you and me
We've all heard it, probably said it too: you can't protect what you can't see. True enough. But there's a corollary that doesn't get enough airtime – your tools can't report their own absence. An EDR knows what it's protecting, but has no visibility into where it isn't installed. A vulnerability scanner reports on assets it reaches and stays silent about the rest.
Our research found that 54% of organizations cannot confidently identify assets missing required security controls. That's more than half operating on the assumption that controls are in place because they're supposed to be.
But among the 46% who can identify gaps, only 34% do it through continuous, automated detection. The rest rely on dashboards, manual reviews, or periodic campaigns – methods that are already stale by the time they're finished.
Our take is to treat the fundamentals as invariants: either they hold everywhere, or they don’t hold at all. Once again, this must happen above the stack, not within individual tools. The task is to define what must be true – every endpoint has EDR, every identity has MFA, every cloud resource has an owner – and then validate those statements against the full environment, not the systems responsible for enforcing them.
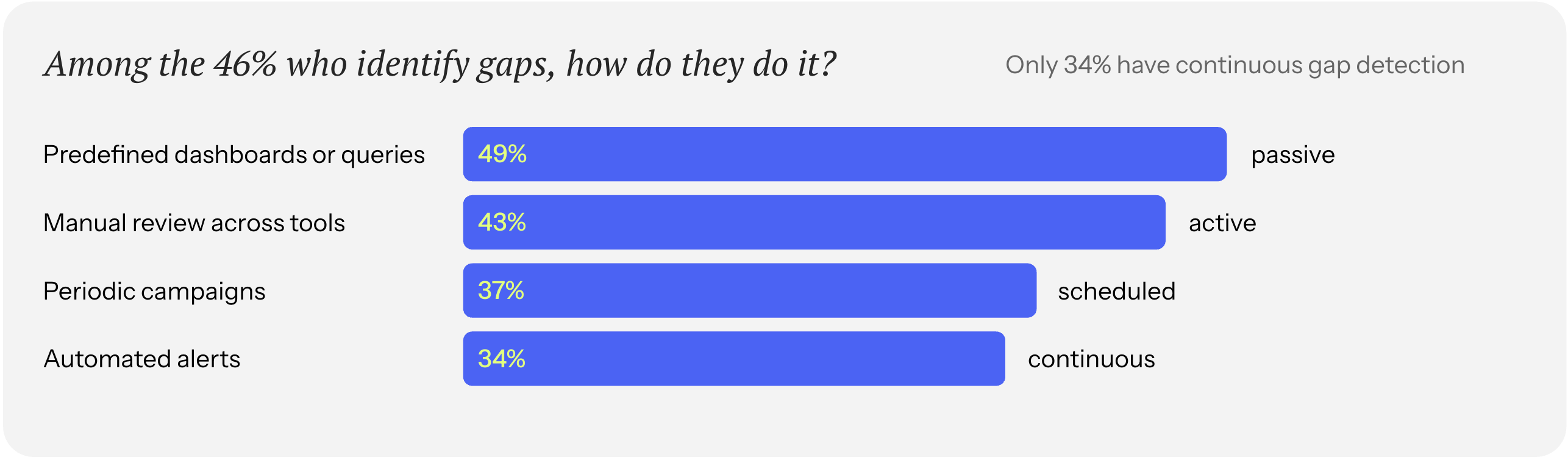
Axonius verifies coverage by correlating signals across all of your security and IT tools to surface where controls are missing, misconfigured, or drifting from expected state. When an invariant breaks, you'll know, and you'll know why.
Context: Ages like a fine glass of milk
Context is the connective tissue between visibility and action. Without it, every alert looks the same and prioritization becomes guesswork at scale. The challenge is that context rarely breaks down inside individual tools; it breaks down in the spaces between them.
Our research found that only 49% of organizations reliably apply contextual data during prioritization exercises – asset criticality, exploitability, blast radius modeling. The other half apply it inconsistently or not at all, which in practice means context shows up when conditions are favorable and disappears when they aren't.
When we asked organizations to name their biggest remediation challenges, the top three – unclear prioritization (26%), no clear ownership (24%), inconsistent data across tools (21%) – are all context problems in disguise. There's also a freshness issue: only 30% reconcile asset inventories daily or monthly, while 37% encounter inconsistencies on that same cadence. Context captured last month does not reflect today's reality.
Our take is to engineer decision-grade context so prioritization consistently results in deliberate action. The data exists – it lives in security tools, asset inventories, and business systems. What's often missing is the layer that brings it together and keeps it fresh. Fresh context, already attached, already trusted. That's what turns prioritization into a decision instead of a debate.
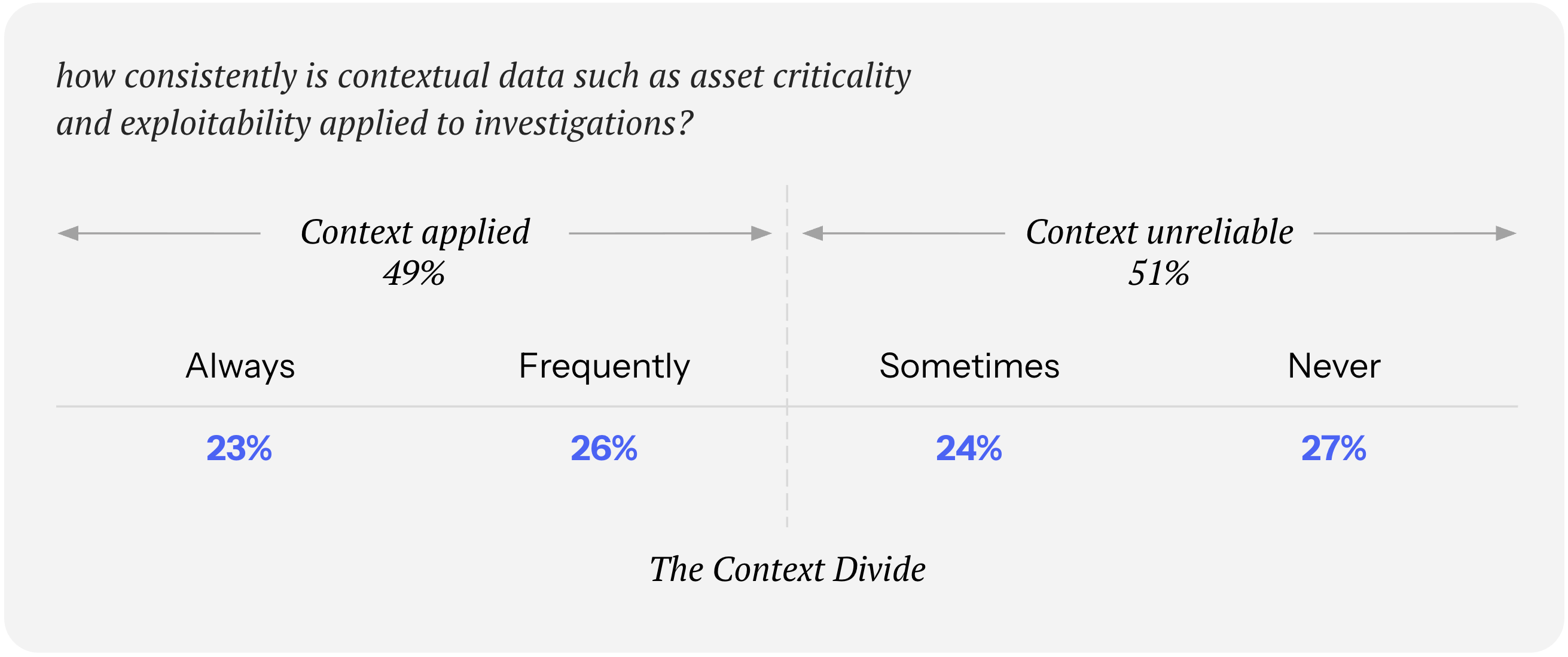
Axonius delivers unified asset, security, and business context with the hard parts of context engineering done for you. We continuously enrich every asset and exposure with ownership, business criticality, control state, and relationships. When an issue surfaces, the context is already there.
Containment: You down with MTT?
Resilience has officially graduated from buzzword to board mandate. But a question lingers – are we asking the right questions? The aim shouldn't be to chase perfection. It should be to optimize for containment first, recovery second, and proof third. Impact is what the business feels.
Our research found that 63% of organizations rank blast radius as a critical prioritization factor, yet far fewer have the mechanisms to actually model it. Only 42% maintain an inventory of crown-jewel assets, and among those, 40% describe that inventory as informal. Impact becomes a made-up construct when you don't know what's actually at stake.
There's also a measurement problem. 36% of organizations primarily measure remediation success using Mean Time to Remediate. Only 30% measure whether critical exposures got closed within a target window. Just 20% track risk reduction. MTTR rewards velocity, but over-containment and under-containment look the same on a stopwatch. A vulnerability patched in four hours feels like a win, but if it wasn't the one that mattered, the dashboard celebrated motion without confirming progress.
Our take is to strengthen your risk model from the outside-in and inside-out. That means modeling the attack surface as a connected system where assets, identities, services, and permissions all interact.
Looking from the outside-in reveals where exposure begins: which assets are reachable, which services are exposed, which entry points matter. Looking from the inside-out reveals where impact accumulates: what an attacker could reach next, which identities amplify access, which systems would feel the blast. Resilience lives in the intersection of those two views.
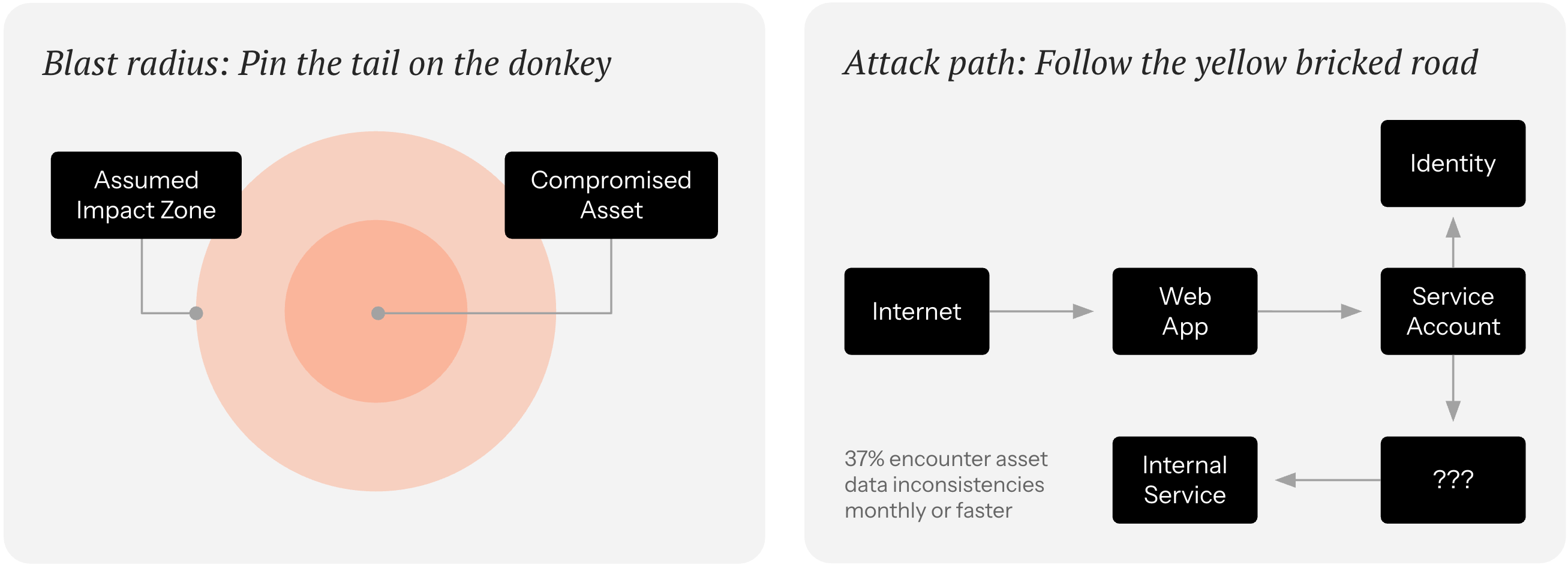
Axonius connects exposure to impact by design. We map assets, identities, and relationships across your environment so you can model blast radius, define crown jewels, and prioritize based on what actually matters to the business. Containment shouldn't start from zero when an incident happens.
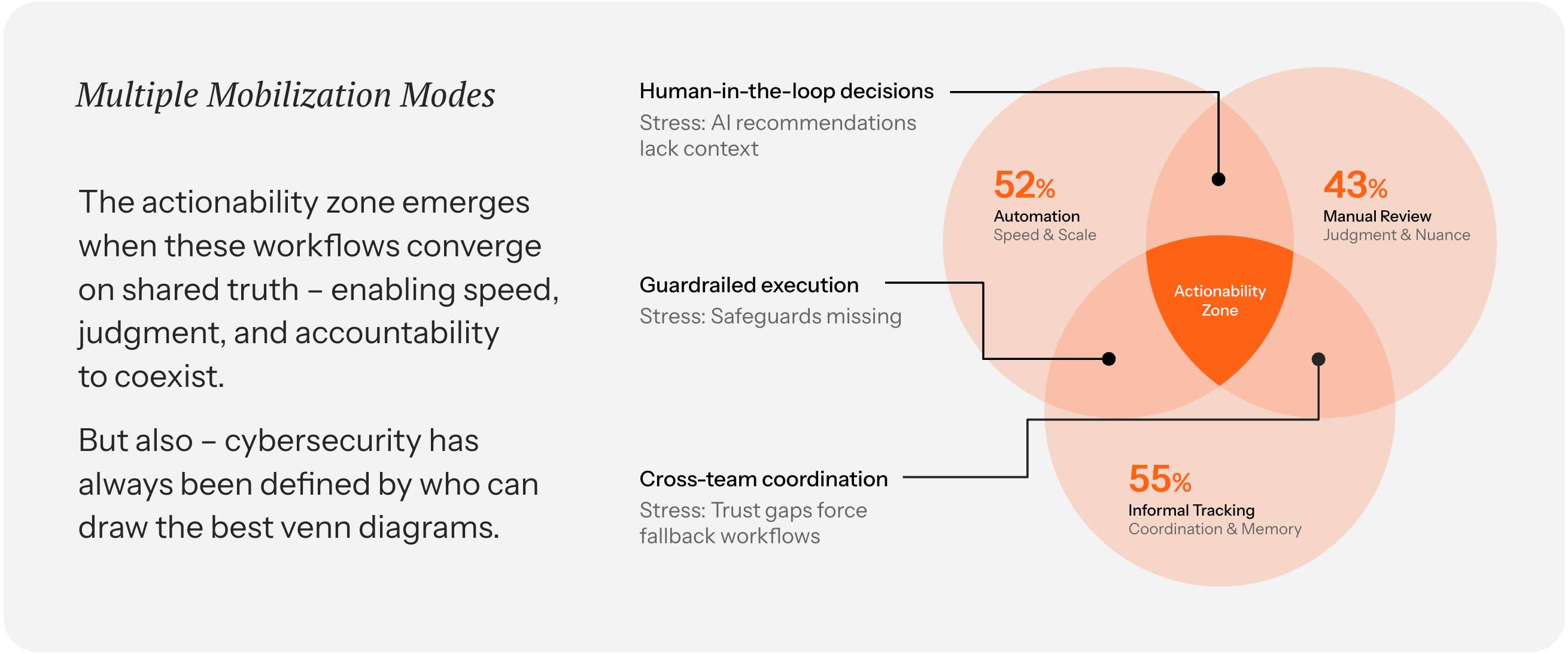
Cooperation: Three owners walk into a bar
Security work doesn't happen in a vacuum, and neither does remediation. Fixes move across teams, tools, and tickets – some automated, some requiring judgment, some needing approvals. That's not a failure. That's how complex environments actually work.
Our research found that when remediation gets assigned, work routes across four different paths: 37% flows automatically based on metadata, 24% automatically goes to IT or security teams, 20% requires manual investigation, and 19% routes to the impacted business unit. Four mechanisms, three organizational boundaries, and often no shared thread connecting them.
The real challenge is that ownership isn't one thing. Owning an asset ("whose is this?") isn't the same as owning the fix ("who patches it?"), and owning the fix isn't the same as owning the outcome ("who confirms it's resolved?"). These responsibilities often land with different people in different systems, and it's easy for accountability to blur at the exact moment clarity is needed.
Our take is to coordinate without conformity by anchoring every action to shared truth. Multiple mobilization modes and handoffs are inevitable. Embrace them, but structure the coordination and be explicit about ownership. Who has it now? What’s the expected fix? By when? When those questions have consistent answers at every stage, coordination becomes the default rather than something that requires extra effort to orchestrate.
Axonius flexes to your coordination workflows, whether automated or manual. We integrate with your ticketing, orchestration, and workflow systems so that every path references the same asset and exposure data. Different teams, different tools, same ground truth.
Closing thoughts
Every finding in this research traces back to the same theme – action depends on truth, but truth is hard to come by. It’s our belief at Axonius that decision-grade asset intelligence is the true unlock between visibility and actionability.
What’s most encouraging about this opportunity is that we don’t see it as a step-ladder maturity curve, but rather a flywheel. Decision-grade data means fewer gaps. Fewer gaps mean richer context. Richer context means faster fixes.
The first rotation is the hardest, but every one after compounds. To us, that’s actionability in action.
Read the full report for more in-depth research and insights: Get the 2026 Axonius Actionability Report.
Categories
- Axonius News

Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
