Introducing the Axonius Vulnerability Management Module
Axonius

Vulnerabilities are everywhere — especially with the increase in distributed work environments and remote work. While keeping environments safe is a top priority, resource-restricted IT and security teams often struggle to understand the prevalence of vulnerabilities, identify threats, and reduce the attack surface.
The newly released Axonius Vulnerability Management Module addresses vulnerability management issues head on. It delivers automated visibility into cybersecurity vulnerabilities, and offers a holistic view of threats, allowing IT and security teams to:
- Identify vulnerabilities across entire fleets of devices
- Prioritize and remediate vulnerabilities based on their urgency and importance
See Assets From a Vulnerability Perspective
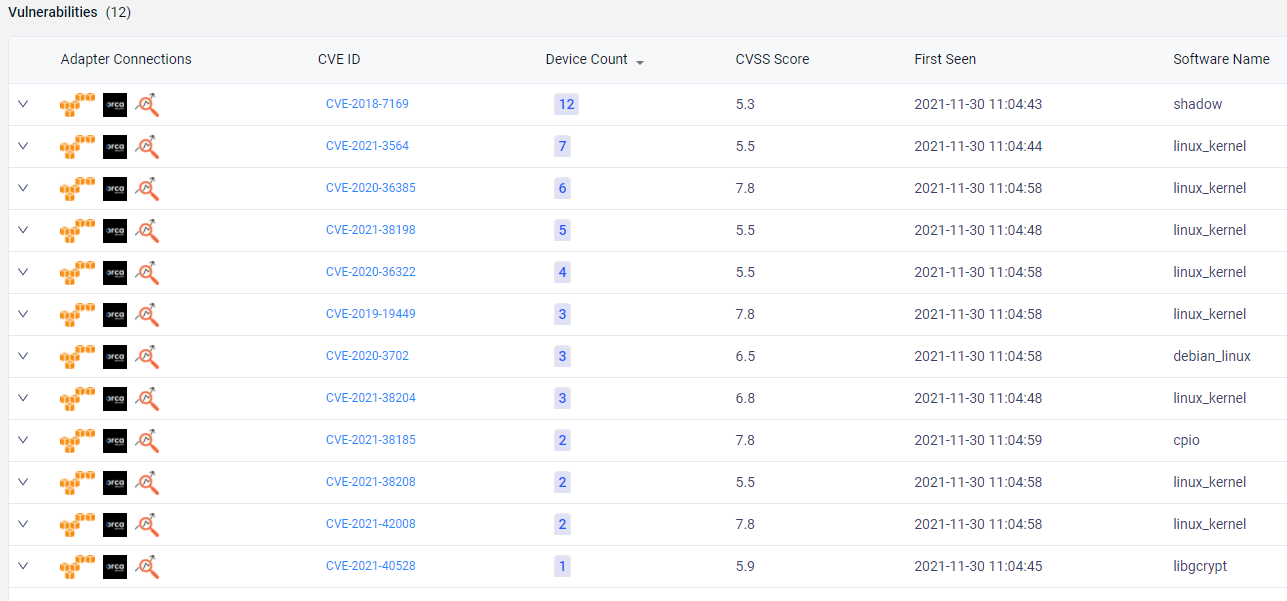
The Axonius Vulnerability Management Module delivers extensive visibility to Common Vulnerability Exposures (CVEs) on all devices in an environment. It identifies unique CVEs, as well as the number of devices that are impacted by that particular threat. It helps IT and security teams quickly learn which software, software version, and vendor is exposed and putting devices at risk.
Not sure if a particular vulnerability exists in your environment? The Axonius Module lets you see which vulnerability was identified, by which adapter, and on which devices. Not sure how long a vulnerability has existed? Find the first detection date to determine whether it’s a new threat or has been a persistent vulnerability that needs immediate remediation.
The Vulnerability Management Module looks and feels similar to the existing device and user views that Axonius users are familiar with. It boasts the same easy-to-reference tabular layout and clickable data style, letting you probe deeper on each unique vulnerability.
Manage Across a Fleet of Devices
Many IT and security professionals are challenged with managing the threat landscape for hundreds or even thousands of devices and network environments. With such a substantial attack surface, it’s no wonder they feel inundated with data and unable to manually identify, correlate, and prioritize information.
The Axonius Vulnerability Management Module solves that issue. It allows the management of vulnerabilities across an entire fleet of devices — all from a single view. Customers can clearly identify threats for all devices across the entire attack surface, and have confidence in the vulnerability inventory they’re managing.
Analyze and Prioritize Threats
Analyzing and prioritizing vulnerabilities as they arise is challenging. Some companies simply fail at this critical step because they can’t see data from the perspective of vulnerabilities, nor do they have the right context about that data to make informed decisions.
Axonius includes data enrichment from the National Vulnerabilities Database (NVD) and other third-party threat intelligence sources. Contextual data identifies circumstances around vulnerabilities that help administrators better understand and assess urgency, relevancy, significance, and importance. Context uncovers deeper insights to support decisions around prioritization, and reduces false positive alerts to reveal a more accurate view of the environment.
Incorporating context isn’t always easy, but it’s possible with Axonius. Our new Vulnerability Management Module incorporates the familiar Axonius Query Wizard but adds advanced query capability that lets users reference contextual device data. The first-level query focuses on vulnerability parameters, including CVSS score, severity, and attack vector. The second-level query expands context to devices, such as operating system, installed software, last seen date, open ports, public IPs, and network interfaces to deliver deep insights around vulnerabilities and the devices they impact. The advanced query capability answers questions like, “What critical vulnerabilities exist and do they impact the critical assets in my environment? How many vulnerabilities exist, and do they appear on devices with open ports, or that have a specific patch applied?”
With contextual device data applied to vulnerabilities, users will know if devices in their networks have known CVEs, how long the threat has been active, if the device has an outdated agent version, and if those devices have public IP addresses.

Categories
- Axonius News

See Axonius in action
Discover what’s achievable with a product demo, or talk to an Axonius representative.
