There is no actionability without asset intelligence: The Axonius Asset Cloud showcase

Earlier this year at the Axonius Adapt25 customer conference, our CEO Dean Sysman declared that CAASM, the category that Axonius pioneered, is dead because it worked. We’ve entered the Actionability Era, where security and IT alike must fully understand their technology environment to make informed decisions based on trusted asset intelligence.
This week at CTRL/ACT, we're showcasing how we are extending the Axonius Asset Cloud for the Actionability Era across four key themes:
Enriched asset intelligence - Building on our data pipeline to understand every asset in its full threat, security, and business context
Actionable actionability - Turning insight into action across every team, domain, and use case
End-to-end program management - Connecting the dots so security and IT leaders can align strategy with execution
Enhanced platform experiences - Enabling maximum productivity for all users of the platform through clarity, consistency, and collaboration across every workflow
Actionability is a continuous lifecycle where teams must gather the right signals, make sense of those signals, and turn those signals into action. Let’s face it, that’s easier said than done. Any security or IT team will agree that even the most meticulously managed environment has its imperfections. As businesses grow, problems grow more acute: data becomes more fragmented or unreliable, and this lifecycle breaks.
A strong foundation built on asset intelligence, however, uniquely enables full lifecycle coverage for security and IT. All of your cyber initiatives, from incident response and asset management to vulnerability management, identity governance, and cloud security, are interconnected. Shared, trusted data gives you the operational leverage you need to effectively manage these programs.
Cue Axonius. We built the Axonius Asset Cloud to solve the data challenge through asset intelligence, at scale.
We know that the information teams require for action is scattered across numerous systems that cover endpoints, apps, users, infrastructure, vulnerabilities, and more. We continue to expand both the depth and breadth of coverage across these systems, extending beyond data aggregation to include correlation (identifying relationships across assets), normalization, and enrichment.
As a result, organizations are able to confidently manage programs like incident response, vulnerability management, identity governance, SaaS management, and more.
Here’s a breakdown of the updates to the Axonius Asset Cloud that we are announcing this week.
Enriched asset intelligence
Asset intelligence is the foundation for everything that we build. The key to unlocking actionability starts with having the right context about your assets. When every asset is understood in its full security, threat, and business context, teams can act with full confidence.
Asset Inventory Classifications
Automatically label assets based on identifiers
We continue to build on the depth of asset data across our asset intelligence pipeline. We’ve added the ability to classify assets by identifiers like operating system, deployment type (virtual, containerized, etc), ownership, and more.
With this level of identifier, teams can run automated enforcement actions to appropriately tag assets. For example, all endpoints that have an EDR should always be tagged as “corporate-owned.”
You may have built Enforcement Actions to do this based on asset attributes, and now we do the heavy lifting for you.
Vulnerability Owner Identification
Accelerate remediation workflows through ownership and accountability
A major factor in timely remediation is clear ownership. Exposures and vulnerabilities need a clearly defined owner to drive remediation action. Through mappings across vulnerabilities and assets, we will soon help you automatically identify team owners to help accelerate remediation workflows.
Non-Human Identity Management
Quickly identify non-human identities (NHIs) through account behavior patterns
NHIs such as service accounts, bots, machine credentials, and API tokens represent a rapidly growing category of “invisible” assets that often sit outside traditional IAM and asset management scope.
However, distinguishing between human vs non-human identities can be a challenge when evaluating profile attributes alone. With these updates, we look at behavioral patterns to spot identities that behave like machines: accounts that initiate scripted API calls, accounts that do not initiate interactive logins, accounts that only log in on a set schedule, etc.

Actionable actionability
Actionability shows up in the platform in many ways so that teams know what to do next, and why. Whether it’s a policy configuration update, endpoint ownership reassignment, or a service ticket remediation workflow, Axonius turns insight into action across every team, domain, and use case.
Contextual Risk Scoring
Deeper insights and customization of risk score calculation
We launched Axonius Exposures earlier this year to help security teams act strategically in minimizing risk, rather than chasing down vulnerability after vulnerability. Our latest updates include a risk score breakdown, clearly explaining how a specific score was calculated based on asset, security, or business context.
We also support queries as fields within the score, enabling you to leverage the results of a query as a condition for how the risk score gets calculated. And, soon, we will also include the ability to set risk thresholds, allowing you to set your own criticality levels for a better understanding of the business context of the score.
Software Registry and Approvals
Automated workflows to identify and manage unapproved software vendors
Software management often comes with high-volume sprawl across device types. Axonius has always tracked installed software across each connected device, and now, we will maintain an expanded software registry that will include details like approval status, EOL data, and license information - for each version of software installed across devices.
Soon, we’ll add the ability to sync approved and unapproved software from external systems like a CMDB or Zip, and enable customers to use the Action Center to remove a piece of software, send a notification, or open a ticket, helping to combat shadow IT.
Access Review Campaigns
Get contextualized recommendations about application entitlements
Identity and access management continues to be top of mind as its applicability spans use cases across security and IT. Now, customers can use Axonius to manage end-to-end access, coordinating certification processes across application assignments.
We’ve also built deep asset intelligence into the certification process, analyzing existing entitlements and permission sets to make smart recommendations for consolidation and revocation.
End-to-End Program Management
While security and IT support different areas of the business, both teams benefit from shared asset intelligence data to drive results and show impact through metrics.
Agent Coverage
Define endpoint agent scope and track coverage in a dedicated Workspace
Identifying agent coverage gaps is one of our marquee use cases. We’ve taken the common patterns identified in this use case and have packaged those up as a dedicated Agent Coverage Workspace, giving customers one place to track coverage, define policies, and take action on coverage issues.
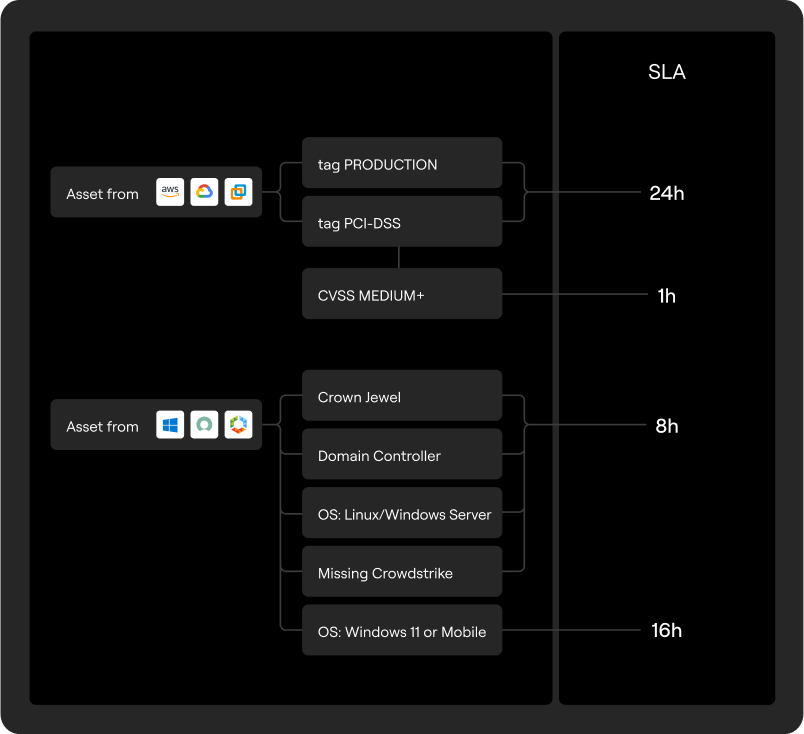
SLA Management
Define remediation SLAs based on asset criticality and business context
The ability to measure SLAs for CVE response, patch updates, or any other exposure is a key performance indicator for security teams. Coming soon, we’ll introduce a way to set and track SLAs based on business context. For example, if an impacted asset identified with a critical CVE is also tagged as a crown jewel, the SLA is bumped from 8 hours down to 1 hour.
Patch Tuesday
Track Windows patch status and issues through out-of-the-box dashboards
If you work in security or IT, you’re very familiar with Microsoft’s Patch Tuesday release cadence for Windows updates. You also know that updating these assets is a coordinated effort across teams.
To support this effort, we will offer out-of-the-box dashboards and a dedicated Workspace that provide comprehensive visibility into the patching and updates posture across your entire Windows footprint. Patch Tuesday is another great addition to our Workspaces feature set.
Enhanced Platform Experiences
Let’s finish up by covering updates to our platform. As we continue to expand our solution coverage, we never lose sight of the people using the platform day-to-day. Whether you’re a CISO reviewing KPIs, or a security operations engineer triaging attack surface exposure paths, Axonius focuses on clarity, consistency, and collaboration across every workflow.
Workspaces
Dedicated use-case-driven views and actions across the platform
Security and IT use Axonius for many different use cases across asset management, vulnerability management, SaaS security posture management, and more. Whether you’re a power user or new to Axonius, we want you to be able to get into the platform, easily select your use case, and be presented with a console experience tailored to your task for the day.
Workspaces offer an intuitive way to stay focused and bring more of your team into the Axonius experience.
Asset Profiles
Each asset type in Axonius has its own unique attributes. There’s no one-size-fits-all view. To address that, we’ve always enabled customers to personalize views by asset types. Now, we will do the heavy lifting for you through tailored asset views, starting with SaaS applications. We will provide a central location to unify an app’s profile, security and cost insights, user access, add-ons and extensions, and more.
This view enables immediate action in one place, assigning ownership, revoking access, and more, with the same level of personalization extended to even more asset types in the upcoming months.
Team mobilization
More automation, enforcement, and coordination across teams
We continue to offer more streamlined ways to mobilize teams to take action through automations and enforcements. Earlier this year, we announced the availability of Workflows, and we have continued to make enhancements to this platform service, including support for webhook events.
This means you can configure workflows to trigger based on a webhook, and Axonius will parse incoming fields to simplify the flow login. Additionally, our Cases feature set includes enhancements like follow-up actions that will trigger when an asset state changes, helping to further coordinate teams and open tickets.
Looking ahead
The enhancements we’ve shared here reflect our belief that the future of cybersecurity belongs to teams who can turn truth into action. The key is trusted asset intelligence data that helps you work more efficiently and confidently than ever before.
Our goal is to strengthen the connection between security and IT teams, helping them drive business momentum through continuous risk mitigation and greater productivity.
If you’d like to learn more about these announcements, tune into CTRL/ACT this week. We’ll share more strategies that successful security and IT teams use to shift from reactive to proactive operations. Join us here.
To learn more about how Axonius can help you, schedule a meeting with our security specialists.
Categories
- Asset Management

Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
