Introducing Axonius Exposures: Prioritize Security Risks That Matter From a Single Place

Avidor Bartov
Co-Founder and Chief Architect, Axonius

Shimon Tzahi
Principal Product Manager, Axonius

This blog gives an executive summary of Axonius Exposures. Check out our technical intro.
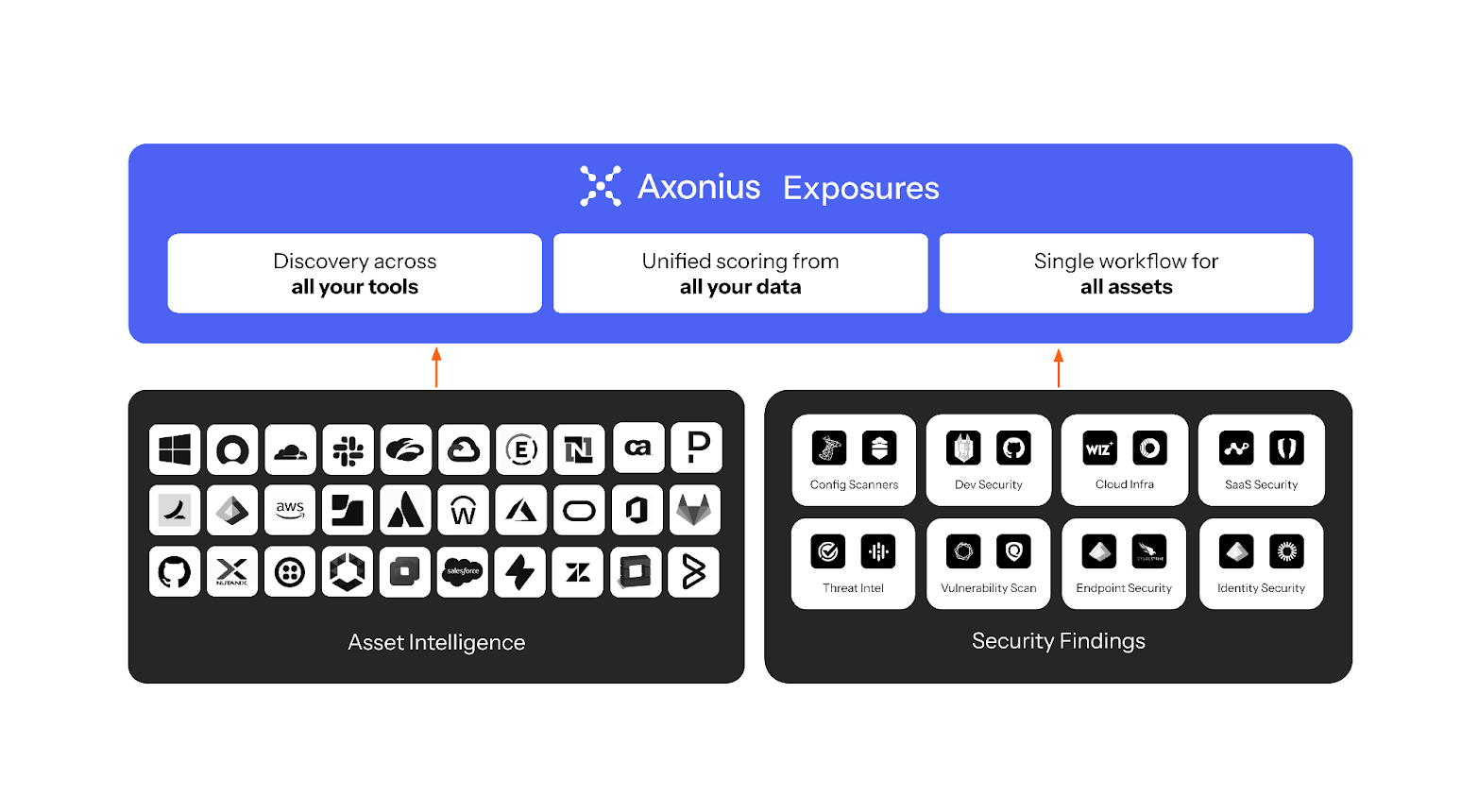
Today, we're excited to announce Axonius Exposures: our new product for discovering, prioritizing, and remediating vulnerabilities and exposures across all your assets and security solutions from a single place.
Security teams are inundated by an overwhelming number of vulnerabilities and exposures reported across disparate tools and silos. Each silo operates with a limited view of the data, requiring teams to manually piece together the big picture: collecting vulnerabilities across all systems, layering in asset state and business context, identifying top priorities, and driving remediation through automation or cross-team coordination.
Axonius aims to address these challenges with a single place to see and take action, combining our market-leading strengths in cyber asset intelligence with vulnerability and exposure management.
Tackling the root of the problem: data
To have a unified workflow, organizations need exposures with security, asset, and business context in the same place.
Axonius solves this problem at the source. Axonius Exposures applies our established pipeline and architecture for asset intelligence directly to security findings. We centralize all security findings from your various tools into a single platform. Then, we combine that with the asset and business context already present in Axonius to automatically deliver data of the highest quality about your risk:
Vulnerabilities and exposures across your entire infrastructure and security tools, prioritized and distributed to the right risk owners.
With this unified data foundation, organizations can confidently tackle all major requirements of vulnerability management and exposure management from a single workflow.
Driving meaningful prioritization
To prioritize effectively, organizations need to calculate exposure risk by combining technical security information with asset and business context.
Axonius Exposures provides a universal risk scoring system with multiple factors, including:
The level of exposure
The potential business impact
The exploitability of the identified vulnerabilities
By considering these factors, Axonius ensures that teams can prioritize their efforts on the most critical issues relevant to their business and security posture, promoting a more efficient and effective security strategy.
Leveraging asset intelligence to find exposure gaps
By connecting exposures data to asset intelligence, Axonius uncovers relationships between vulnerable software and the devices, identities, and infrastructure they affect, helping teams understand risk in multiple dimensions. This includes:
Exposures on business-critical assets
Exposures on systems missing critical controls
Exposures on systems handling production traffic
Axonius Exposures also identifies vulnerable assets reachable through your load balancers, firewalls, and subnet configurations. Our configuration-based approach finds public routes of attack before any network traffic.
Driving ownership, collaboration, and action
Axonius Exposures centralizes the entire remediation process, from planning to tracking to auditing, in one platform, with options for driving remediation automatically and in collaboration.
Through Workflows, you can define when remediation should happen automatically versus manually. For example, if a security issue is present in a workstation and a solution for a remote patch is available, fix it directly. Otherwise, open an incident in the ticket system:
When solutions require manual work, Axonius Exposures keeps track of work across your teams to ensure security SLAs are met and no issue is left behind:
Getting started with Axonius Exposures
Axonius Exposures is Generally Available Today. To see Axonius Exposures in action, book a personalized demo with us!
If you’re attending RSA 2025, stop by our booth, South Hall, Booth 626, to see our product in action. (Details here)
Categories
- Threats & Vulnerabilities

Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
