A Technical Introduction to Axonius Exposures: Prioritize Security Risks That Matter From a Single Place

Shimon Tzahi
Principal Product Manager, Axonius

Coby Soffer
Engineering Team Leader, Axonius

Frederico Hakamine
Technology Evangelist, Axonius

This blog gives a technical intro to Axonius Exposures. Check out our launch post for an executive summary.
Today, we're excited to announce Axonius Exposures, our new product for managing risk exposures (vulnerabilities and exposures) across all your assets and security solutions from a single place.
Think of Exposures as the Axonius platform applied to a core challenge all vulnerability management tools (VM, UVM, RBVM) still struggle to solve: getting you out of information silos and providing the ultimate solution for managing risk exposures (vulnerability and exposure management) based on the data that truly matters: security, asset, and business context, all in the same place.
Why should I keep reading this?
Axonius Exposures help organizations run vulnerability and exposure management programs more effectively, spending less time stitching data and more time on productive work.
Check out how easily you can see all occurrences of an issue (i.e. XZUtils) reported by all your tools and then instantly lock on the most pressing occurrences (i.e. for the Infra teams; in servers missing CrowdStrike; in your production servers; both on-prem and in the cloud).
Example: Narrowing down all the occurrences of XZUtils (CVE-2024-3094) to the most critical occurrences according to your business and asset context.
How Axonius Exposures works
The example above combines security vulnerabilities, assets, and business context across all systems to deliver instant answers. How's that possible?
Axonius Exposures uses Axonius platform components, adapter network, discovery process, asset fabric data, computation engine, and enrichment engine, to collect, aggregate, and deduplicate security findings reported by your security tools in the same place:
Diagram: Axonius data intelligence pipeline.
This information is then combined with the asset data from Axonius Cyber Assets, which undergoes the same process, bringing together the best vulnerability and asset data in one place:
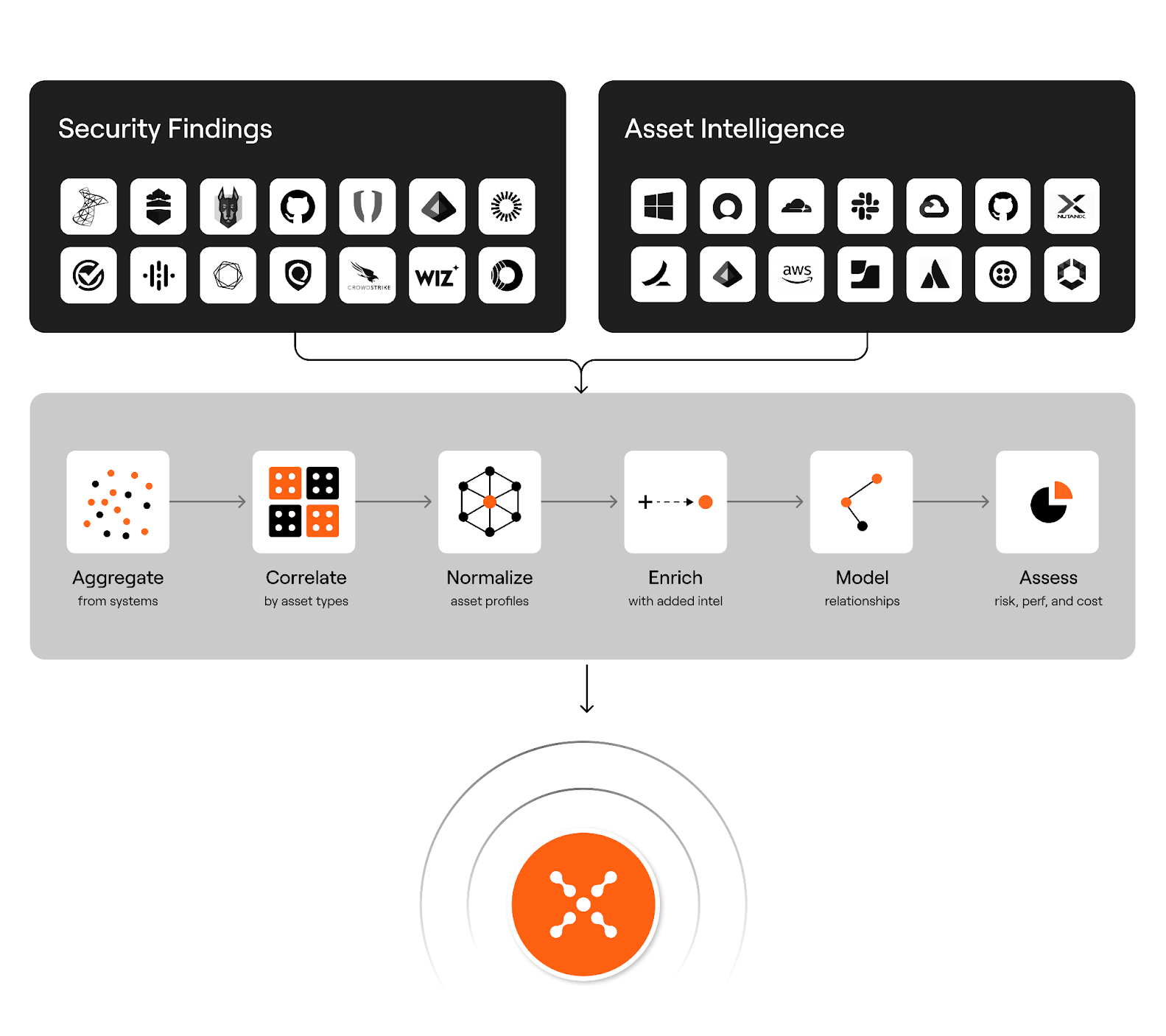
Image: With Axonius Exposures, asset intelligence and security findings go through the same data intelligence pipeline.
This combination provides a foundation that vulnerability and exposure management teams often struggle to achieve: the most relevant data, all in the same place:
Security context: CVSS and EPSS score, threat intelligence feed, Vuln Scanner recommendations…
Asset context: Is the asset online, does it have EPP, is it a domain controller, does it have public internet traffic...
Business context: Is the asset in production, is it a crown jewel in ServiceNow, is it in the PCI network, who's the business owner...
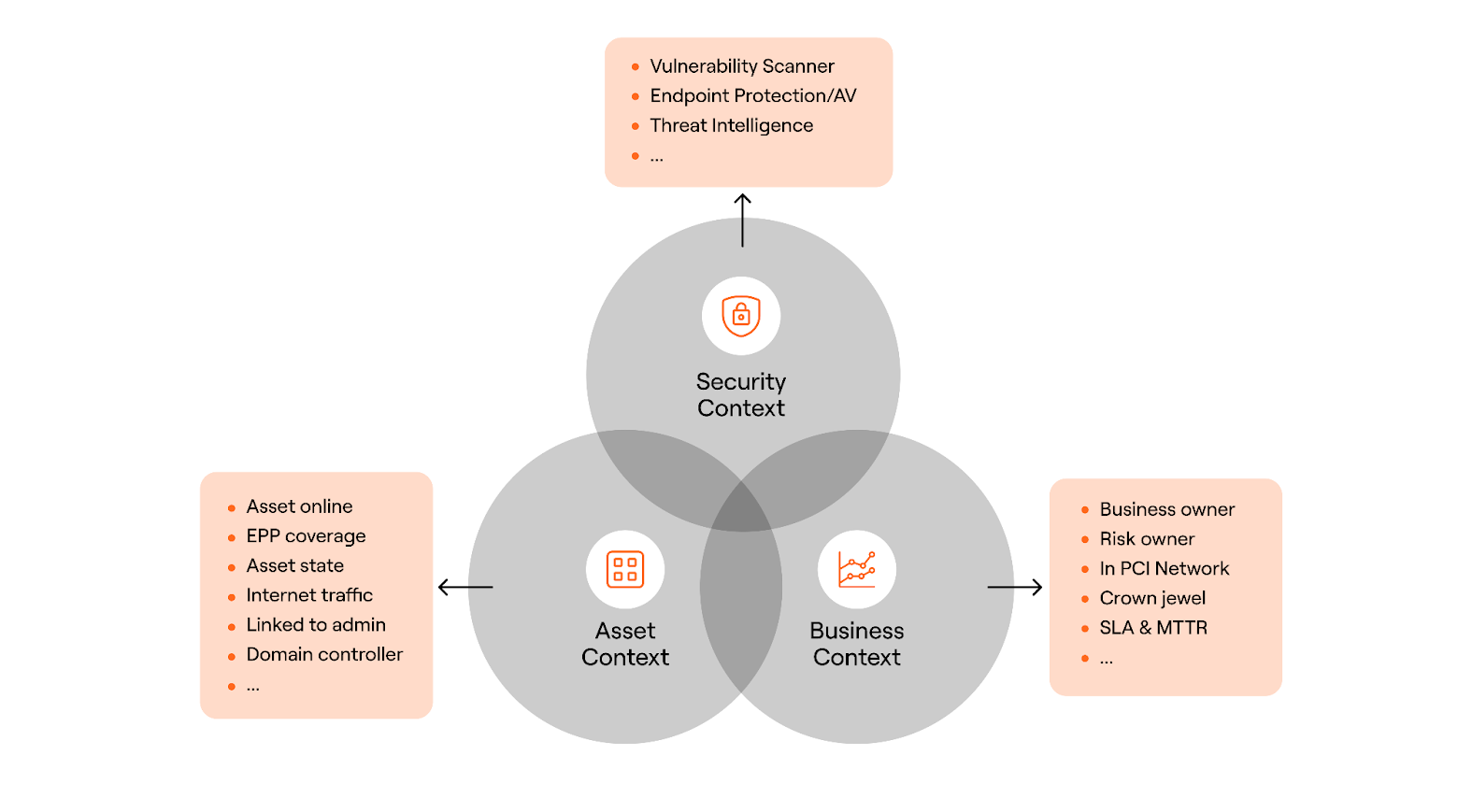
The data foundation provides better results across the entire vulnerability and exposure management program.
1. From prioritizing issues:
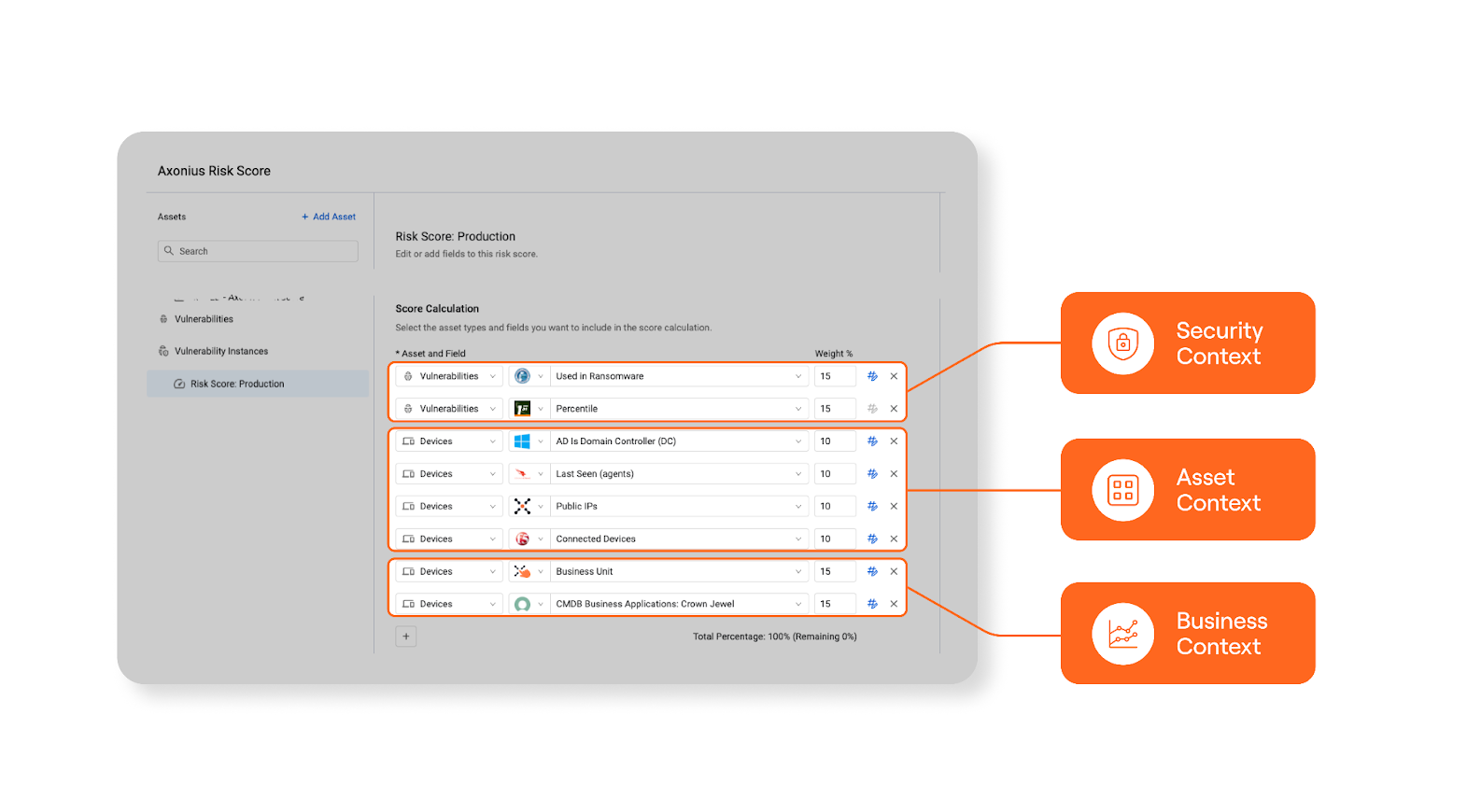
Risk score based on security, asset, and business context.
2. To providing dashboards:
Historical risk (based on security, asset, and business context) broken by priority and owner.
3. To driving ownership and accountability:
Risk overdue by owner and most pressing issues.
4. To supporting deeper investigations:
Isolating vulnerabilities of high risk, owned by the Infra: on-prem (bare metal), in servers missing Intune and with the Falcon Sensor not operational for more than a week.
5. To driving action:
Workflow logic: If a security issue is present in a workstation and MECM is available, patch directly. Otherwise, open an incident in ServiceNow.
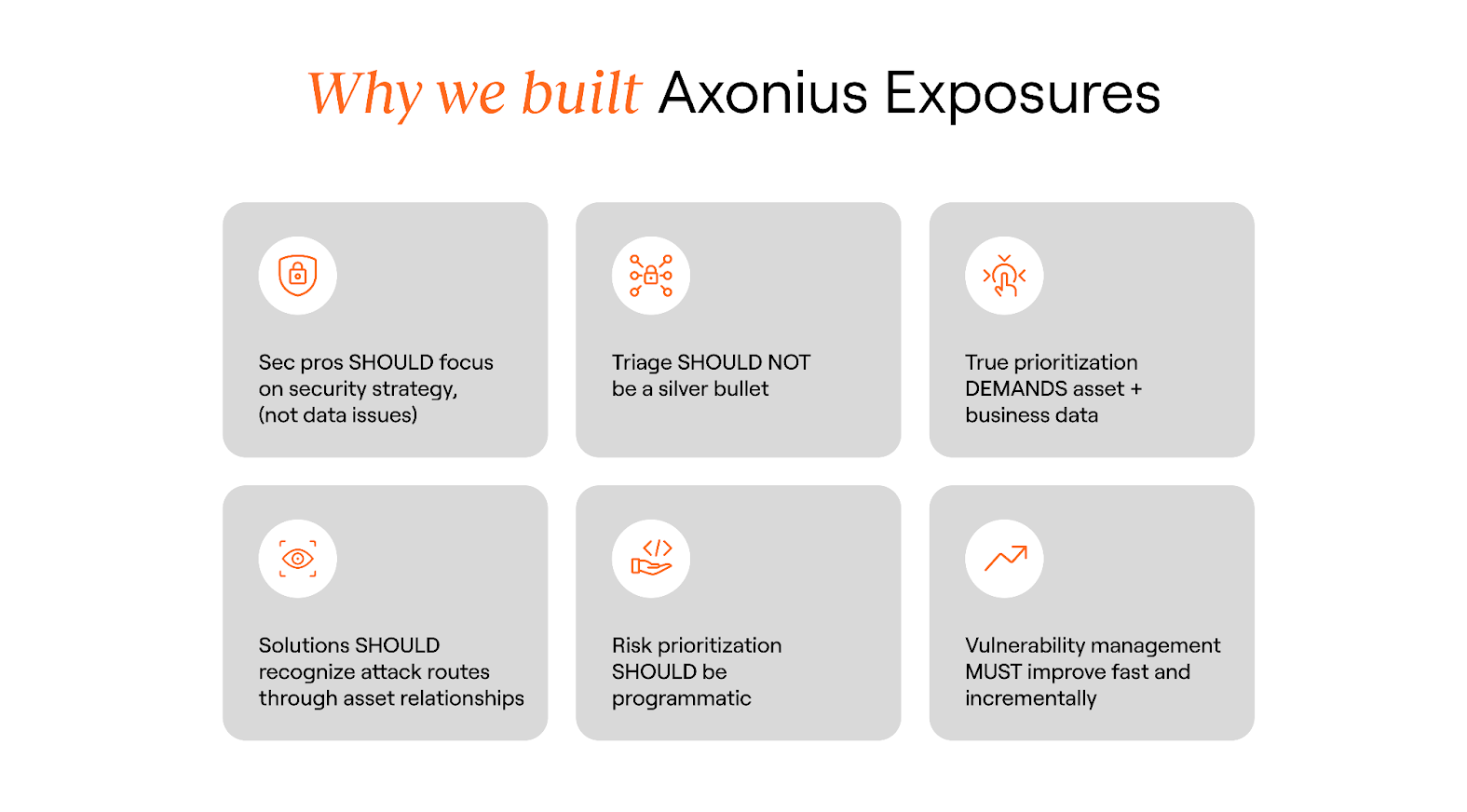
We built Axonius Exposures to give security teams a practical way to tackle the vulnerability management issues that keep them in reactive mode.
Sec pros SHOULD focus on security strategy, (not data issues): Teams should concentrate on building a strong security program, the work that requires their expertise, not on data integration.
Triage SHOULD NOT be punished by data silos: Triage is deeply affected by bad vulnerability management, paying for the inefficiencies not only with manual work, but also with political capital (trying to convince teams something is urgent without KPIs to back them).
Meaningful prioritization DEMANDS a combination of security + asset + business data: The only way to drive action from your business and remediation stakeholders is to present security issues (i.e. a critical CVE or misconfiguration…) with asset data (in your production and missing endpoint protection…) and business data (has PII, belongs to internal IT…).
Solutions SHOULD recognize attack routes through asset relationships: Network is critically important, but not the only route of attack. Asset relationships help uncover other vectors (i.e. compromised device, with user identity, and related SSO apps).
Risk prioritization SHOULD be programmatic: Risk scoring with security, business, and asset context should happen across all systems, automatically, and before any human is required. Failure on any of these requirements means overloading triage.
- Vulnerability management MUST improve fast and incrementally: Vulnerability management is changing from reactive (i.e. zero-day/celebrity CVEs driven) to a continuous (i.e. CTEM) execution. A paradigm shift is needed, but teams are underwater and cannot change all at once. We built Axonius Exposures to help security teams improve their programs fast and gradually, without introducing migration issues and scope creep.
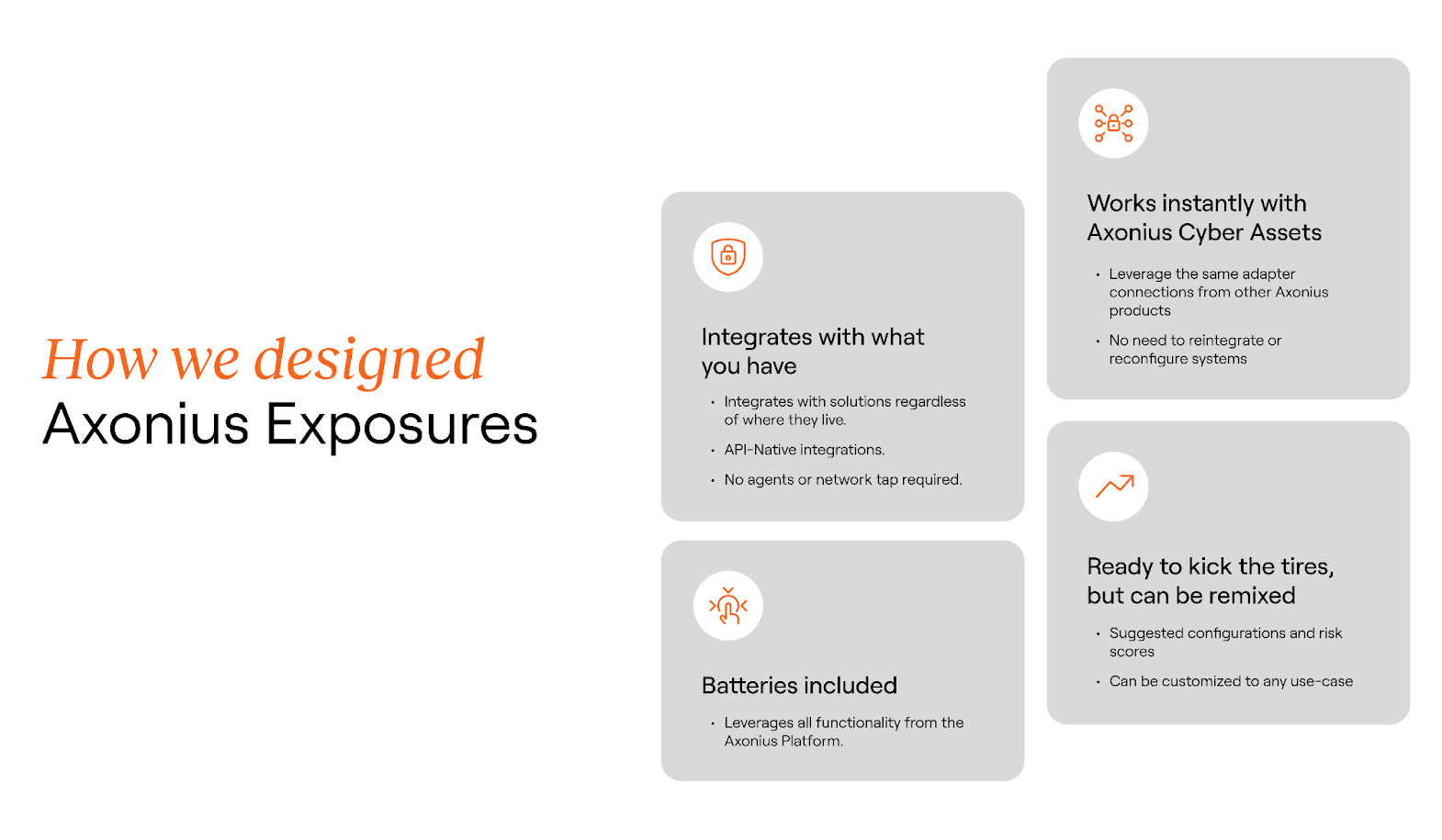
Axonius Exposures was designed with security team ergonomics top of mind and to seamlessly fit into their vulnerability management program and CTEM ecosystem:
Integrates with what you have: Axonius Exposures uses native adapters to integrate with your solutions no matter where they live. No agents or network tap required.
Works instantly with Axonius Cyber Assets: If you already use Axonius Cyber Assets, Axonius Exposures can be turned on instantly, without the need to reintegrate adapters.
Batteries included: Axonius Exposures leverages all the functionality from the Axonius Platform: from query language, to dashboard customizations, to workflows, enforcement actions, and much more.
Ready to kick the tires, but can be remixed: Axonius Exposures provides suggested risk scores out of the box that you can customize to your needs.
We validated Axonius Exposures by dogfooding it in our own exposure management program and by working over 30 of the largest organizations and security programs across multiple industries.
Get started with Axonius Exposures
To get started and stay up to date with Axonius Exposures:
Attend our webinar: “7 Best Practices for Vulnerability Management in a World of Noise.” This webinar explores current vulnerability management challenges and how Axonius addresses them.
Categories
- Threats & Vulnerabilities

Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
