Launch Week 2026: Exposures momentum

Shimon Tzahi
Principal Product Manager, Axonius

João Victor Motta
Engineering Team Leader, Axonius

Ori Azgad
Director of Product Management, Axonius

If you’re in the security trenches, you know that "CVE severity" is just one piece of what makes a risk critical. Real risk comes from the combination of technical issues (CVEs, secrets, identity sprawl), business criticality (crown jewel, holds PII), and asset context (missing endpoint protection, publicly exposed to internet traffic).
In less than a year, Axonius Exposures, our solution for unified risk management, has become our fastest-growing product in the history of Axonius. We’ve been recognized as a CTEM Leader and Cloud Security Innovator by Latio, got a shout-out from the amazing folks at SACR and John Hammond, but we’re most proud of the customer feedback:
“We now focus on 5% to 10% of what we told remediators to worry about in the past.”
We’re helping teams prove that exposure management isn’t just about finding more security issues: it’s about mastering the visibility, prioritization, and action to better protect your organization.
This week, we’re launching three features to scale that mission.
1. Mapping external exposures (no matter where your network lives)
To prioritize exposures, you have to know which security findings are in the direct line of sight for an attacker. While this is achievable in isolated contexts (like the cloud), modern infrastructure is a fragmented mess of vendors and equipment spanning on-prem data centers, site-to-site VPNs, and multi-cloud environments.
Today, we’re announcing the External Exposures Dashboard to give you a view of reachability across all these planes, from ground to cloud.
From the dashboard, you get the big picture of which assets and vulnerabilities are actually exposed via the network before you ever dive into a specific finding.
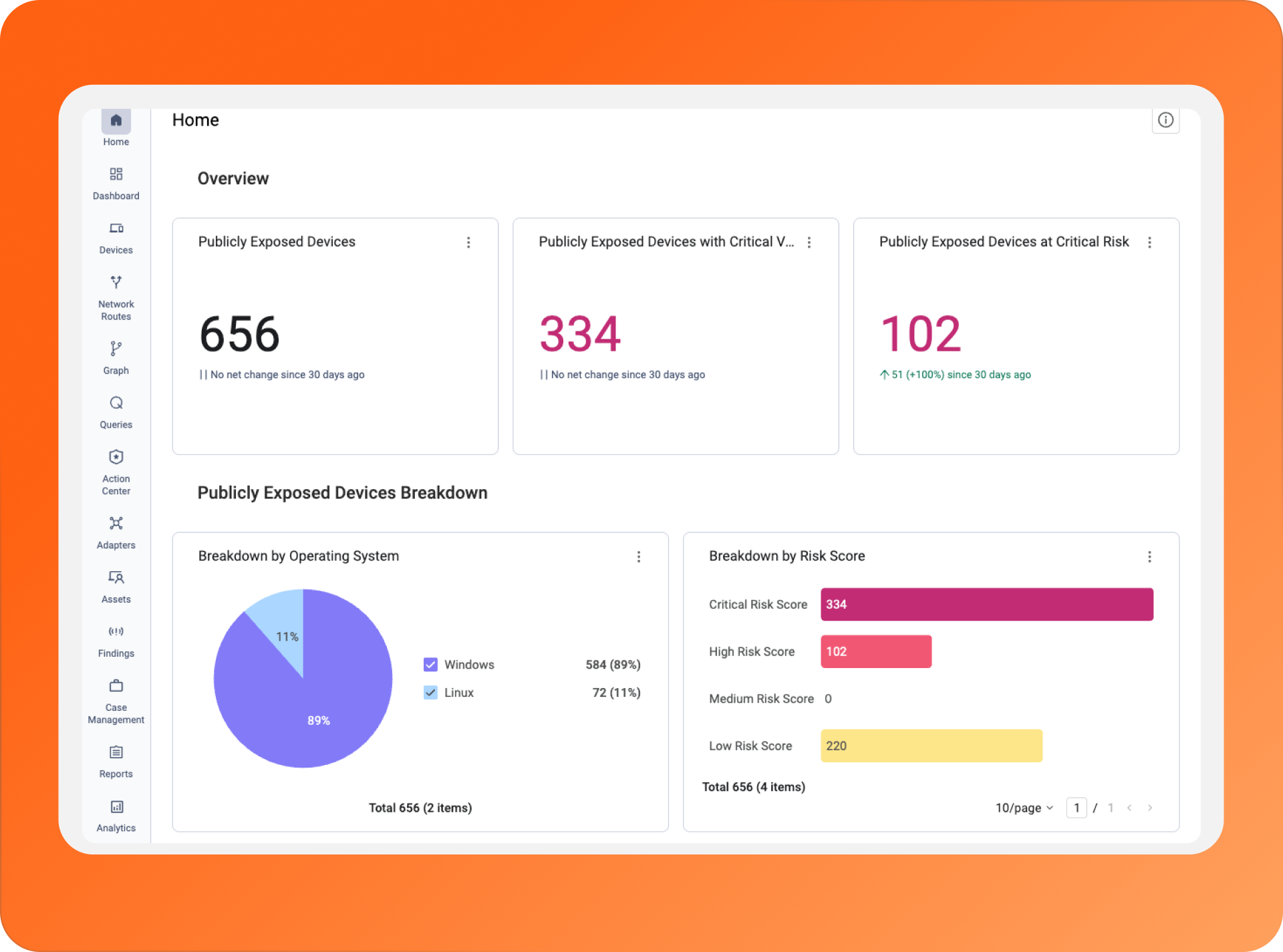
From there, you can access the full list of network routes linked to devices, vulnerabilities, and relationships to get the "so what":
- Validated network routes: See the path an attacker would take to reach the exposure.
Asset context: Verify if the exposed asset has active controls, like endpoint protection, or if prevention policies are actually enforced.
Relationship graph: See the relationship between the affected asset and critical items in your infrastructure (where lateral movement/impact can spread).
By combining External Exposures with the Axonius platform (1,200+ integrations/40+ asset types), you extend the visibility across multiple environments and planes.
2. Normalizing the “Network Babel”
To map reachability, you have to read the policies of your network equipment. While vendors offer APIs, none of them share the same policy language. A policy in Palo Alto looks nothing like an AWS Security Group or a Cisco ACL. This fragmentation is what makes the map of external exposures incredibly difficult, especially when traffic traverses both on-prem hardware and cloud infrastructure.
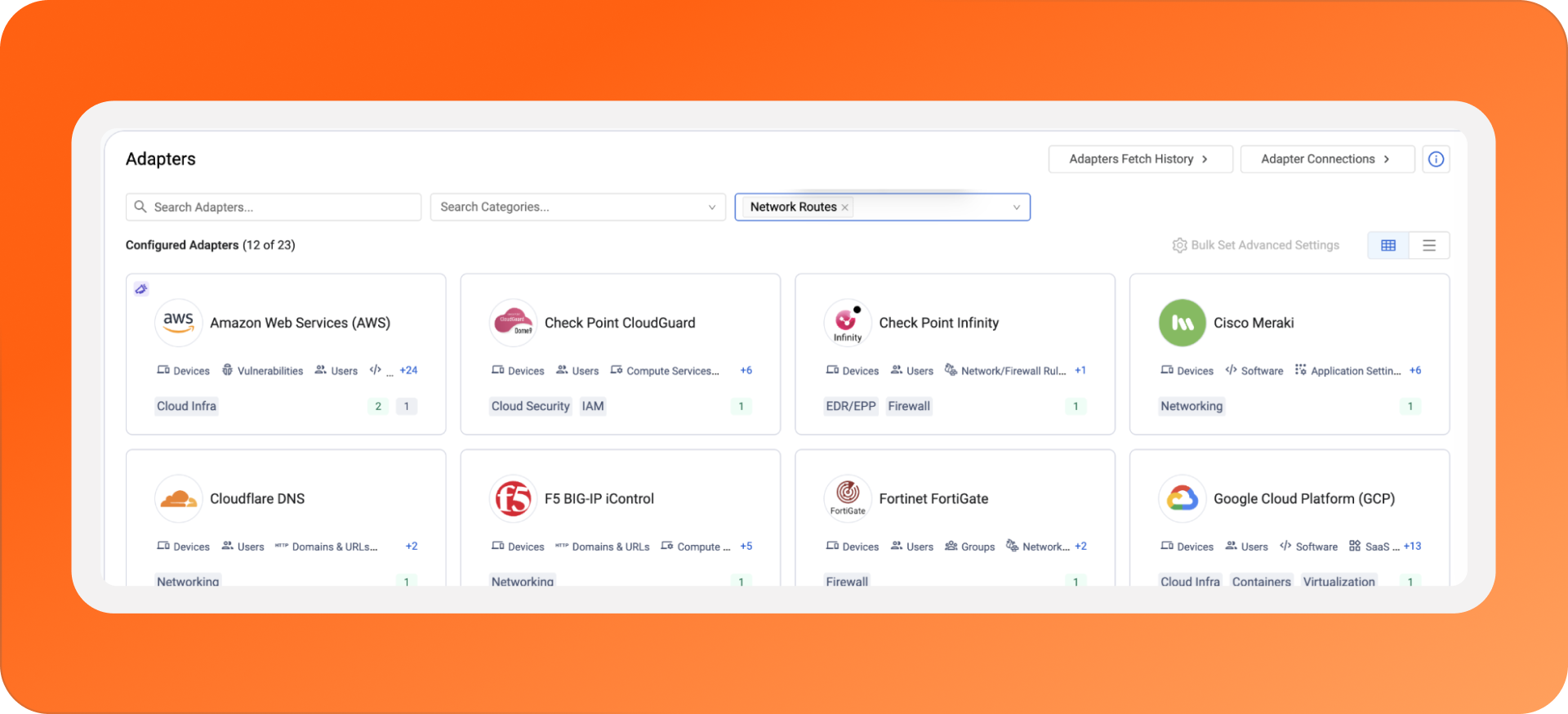
Today, we are launching 20+ dedicated network adapters to solve this. We’ve done the hard work of normalizing these proprietary policy languages into a unified view. From ground (Cisco, Palo Alto, FortiGate) to cloud (AWS, Azure, Cloudflare), we translate the "Babel" of network policies so you don't have to.
To see the full list of supported vendors, head to the Adapters page and filter for those supporting network routes:
3. Exception Management: Accountability with context
Security isn’t just about finding and fixing; it’s about managing the reality of what can’t be addressed immediately. Whether it’s a saturated resource or a legacy system that can’t be patched, accepted risks should be tracked in a different way from "overdue" noise.
We’ve updated our Exception Management engine to address this. From a single place, you can track exceptions no matter where your remediators operate (Jira, ServiceNow, PagerDuty, etc.), keeping the records for future audits in a single place.
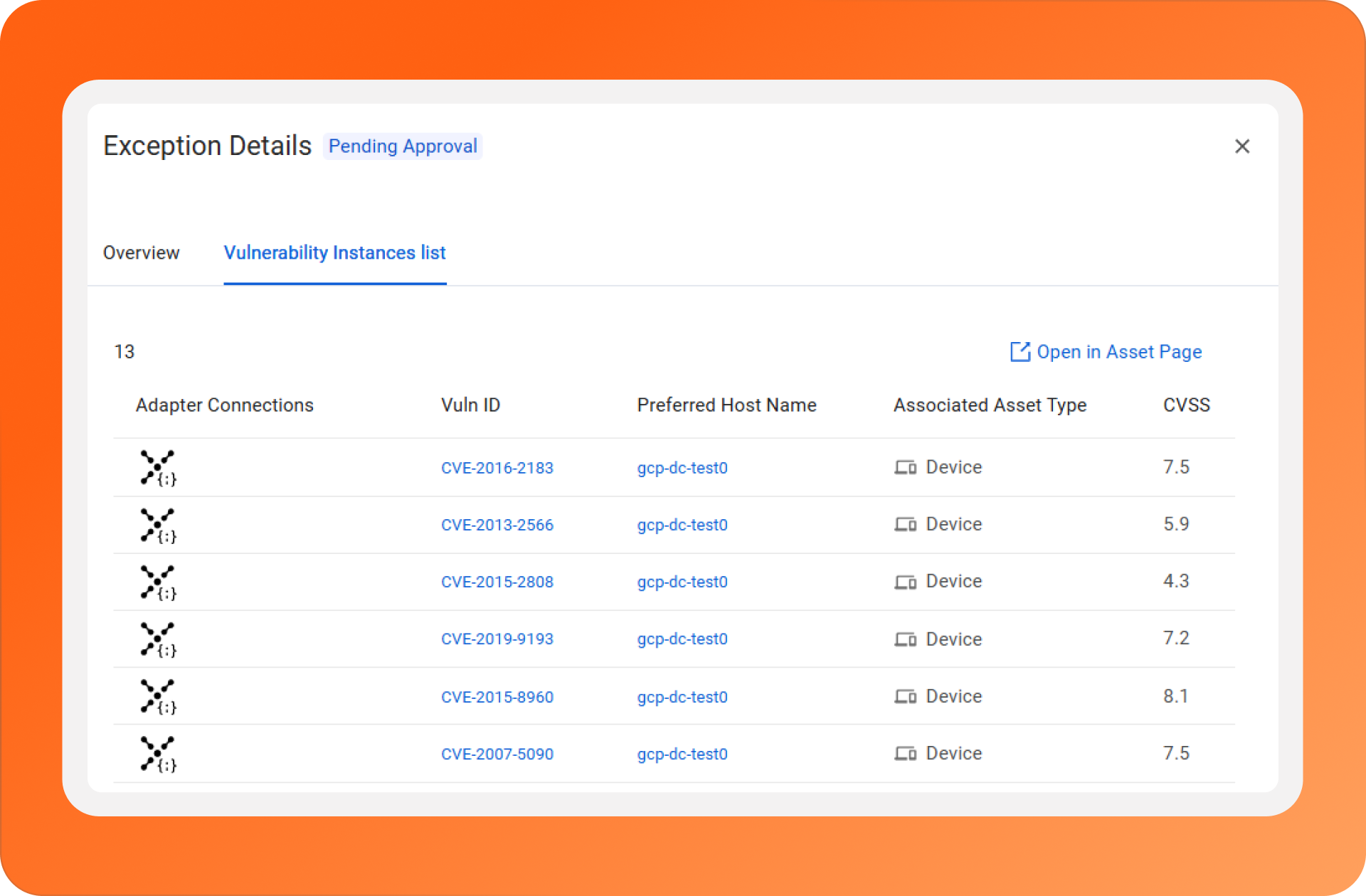
Exception Management, allied to Axonius Asset Intelligence, brings the full picture into focus. When you browse for an Exception, you get the exception request, asset, and exposure records from a single place. This gives your team the context and confidence they need at audit time.
We’re just getting started
We’re seeing incredible excitement around Axonius Exposures. Organizations are already reporting a 90% increase in focus, but we believe we can do even more.
Our cyber research team is just coming out of deep research with innovative ways to increase focus from noise. We’re working to carry that intelligence directly into our product to give you what you crave the most: focus to address risks at scale, without silos.
In less than a year, we’ve become a CTEM leader, but honestly? Wait until you see what’s next to reduce the noise. We’re just warming up.
Ready to dive deeper?
Categories
- Threats & Vulnerabilities

Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
