Cybersecurity KPIs: Metrics to Prioritize in 2024
Alexandra Lietzke

Defining metrics to showcase the value of your security program has never been more important than it is now. Why? Tasked with managing increased attack surfaces and ever evolving cyber threats, modern security teams are facing more complexity with less resources than before. If security leaders want enough budget to protect their organization, they must be able to demonstrate value by measuring security outcomes. And to do this, you need to know what specific metrics to track.
This gives you the insight to:
- Determine gaps in current measurement processes
- Understand how to map metrics to business objectives
- Justify and communicate the value of your security program to key stakeholders
But this doesn't come without challenges. Without the right tools, collecting the right data can unfortunately lead to skewed information – like incomplete, missing, biased, or outdated data. In this blog post, we'll take a deeper dive on two of the most critical metrics from our new ebook: "Mastering Cybersecurity Measurement: How to Show Metrics that Actually Matter," that can help you gain accurate context into your environments.
The first metric to measure is coverage for security controls. This could look like tracking the expected asset population that you expect would be in-scope, and then understanding what percent of that population has the specific control present and recently active. Measuring this metric will help you:
- Gain meaningful context around the extent of your security coverage
- Identify potential vulnerabilities
- Highlight where in your environment requires advanced security measures beyond what’s already in place
To gain a better understanding of your environment, you might also consider tracking metrics like the amount of anti-malware protected systems in your organization, the percentage of assets scanned for vulnerabilities, how commonly secure authentication methods are being employed, and the average number of usage activities per IT asset. This will show you where your security gaps actually are.
But how can you close them? Since agents only provide visibility when they’re deployed and functioning, cyber asset attack surface management (CAASM) solutions like Axonius identify exactly where your agents are – and where they’re not. The Axonius Platform automates, tracks, and enforces actions to ensure agent coverage and performance so you don’t have to. Axonius also tracks agent health – identifying devices with endpoint agents that haven’t communicated back to management consoles, (indicating their agents may be broken or disabled) – allowing you to address and fix problems before they become security incidents.
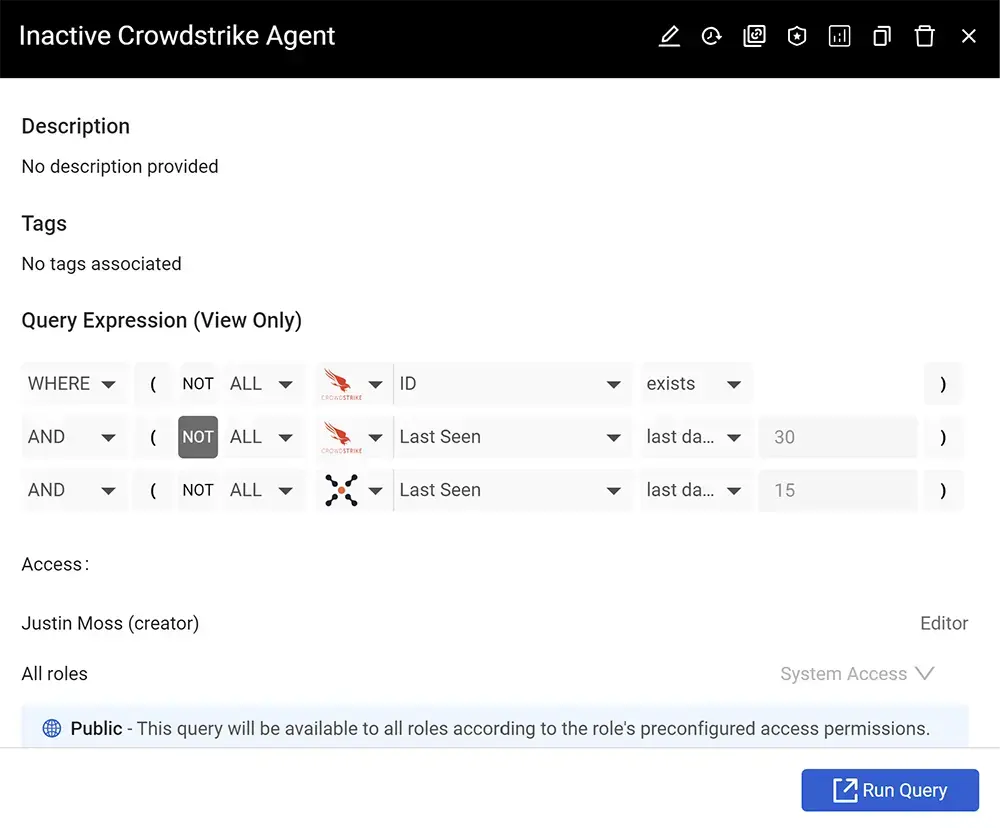
Source: Axonius, Inactive Crowdstrike Agent Query
SaaS Security Metrics
Another important metric to track is how many SaaS application integrations require a large amount of access to your environments. For example, you want to be wary of what SaaS apps you grant full permission to read all of your email. Measuring this metric will help you:
- Prevent unauthorized application usage
- Mitigate potential vulnerabilities
- Ensure proper security configurations
To better manage the risks associated with SaaS usage, you can also measure how many SaaS application settings are misconfigured, the recurrence of shadow SaaS applications, and how many third-party extensions have access to sensitive data. This gives you a better picture of what SaaS applications may be granting too much access to external parties and increasing risk.
And this can be done by using a SaaS Security Posture Management (SSPM) solution that continuously assesses and enhances the security of the SaaS application stack by detecting and remediating misconfigurations and policy drifts, ensuring compliance, and protecting sensitive data against various threats.
Axonius makes it easy to manage and mitigate existing threats by providing a comprehensive view of the SaaS apps used across an organization – giving you an extensive breakdown of existing app settings, misconfigurations, and vulnerabilities, along with guidance on mitigation steps and built-in options for remediation.
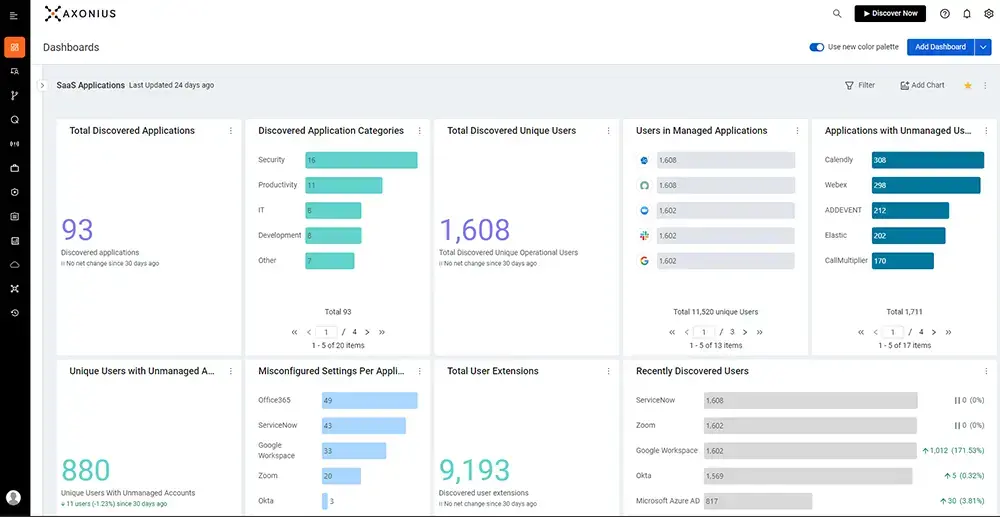
Source: Axonius SaaS Management, SaaS Applications Dashboard
These two metrics are just the beginning – and every security program has specific needs and objectives. The metrics that prove the value of one security program and what areas can be improved will look different for another. Our new ebook, "Mastering Cybersecurity Measurement: How to Show Metrics that Actually Matter," shares insights on how to choose metrics that add value to your unique security program. Once you determine what’s right for your team, you’ll have taken the first step towards proving the worth of your security efforts and addressing areas of growth.
Categories
- Cloud and SaaS Security

See Axonius in action
Discover what’s achievable with a product demo, or talk to an Axonius representative.
