Validate Google Cloud Platform Instances Against Industry Benchmarks.
Axonius Cloud Asset Compliance for Google Cloud Platform (GCP) aggregates and correlates data from your GCP environments to show how each instance adheres to and deviates from benchmarks, such as the CIS Google Cloud Platform Foundation Benchmark.
Axonius automatically collects and aggregates information from your Google Cloud Platform and maps the data against the CIS Google Cloud Platform Foundations Benchmark.
Map Google Cloud Platform Against CIS Benchmarks
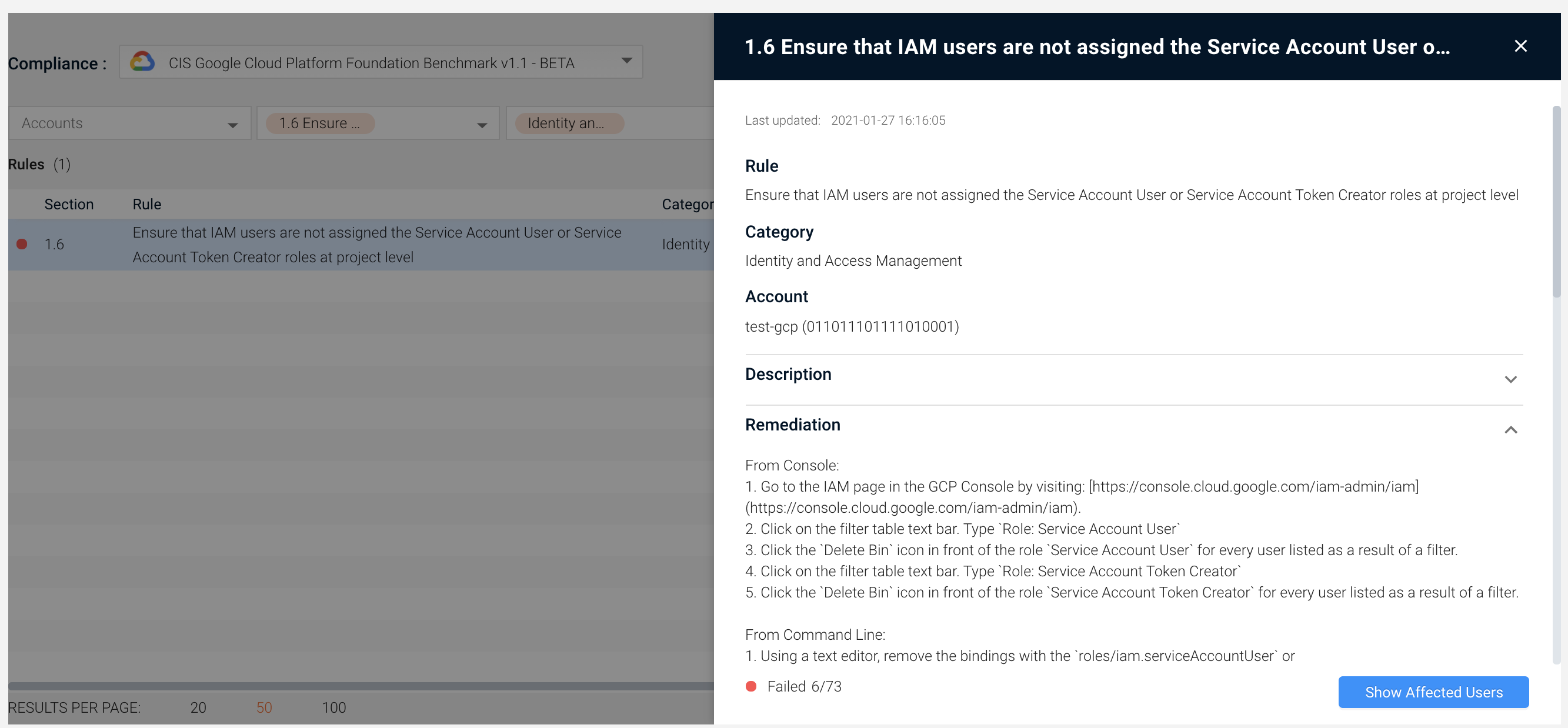
Get a Full View of IAM Across All GCP Instances
Axonius checks Identity and Access Management benchmark rules across your Google Cloud Platform ensuring corporate login credentials are used, that Google Cloud KMS cryptokeys are not anonymously or publicly accessible, and more.
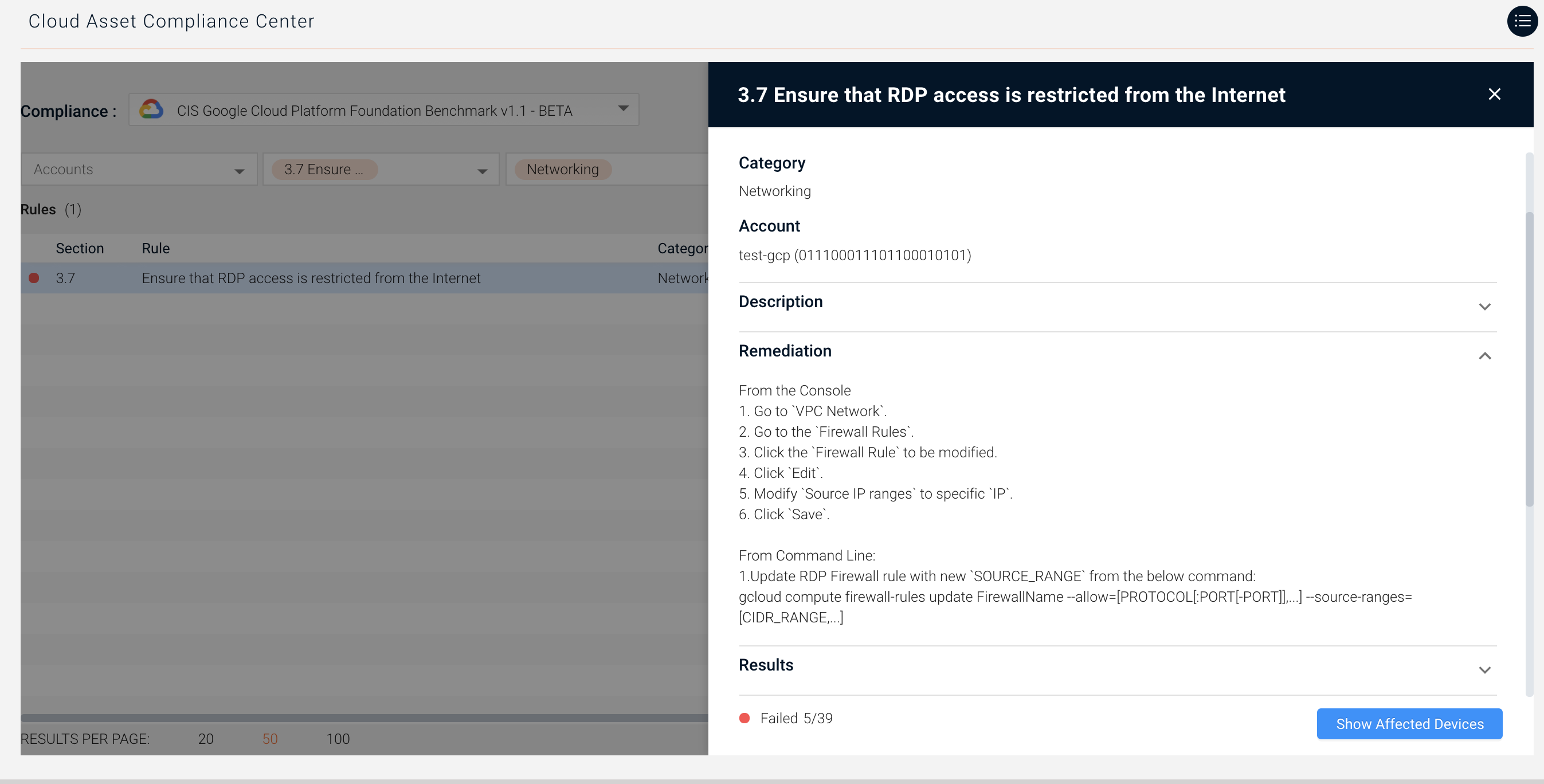
Ensure Networking Policies are Set Correctly for Google Cloud Platform Accounts
Axonius checks Networking rules in the GCP CIS Benchmark, such as whether RDP and SSH access is restricted, that no default or legacy networks exist for a project, and more.
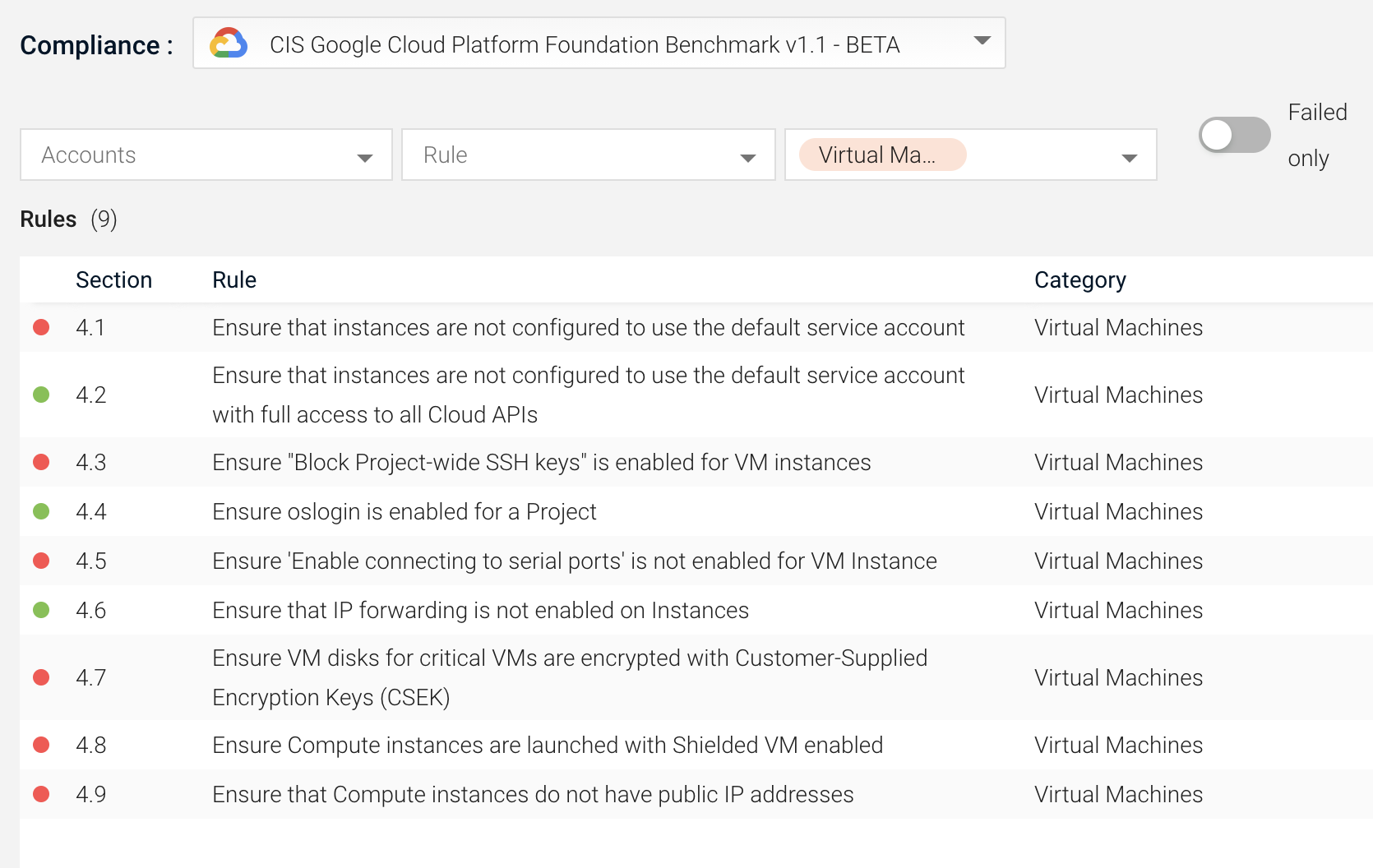
Verify that GCP Virtual Machines Meet Encryption Best Practices
Axonius examines virtual machines in GCP to ensure VM disks are encrypted, compute instances do not have public IP addresses, IP forwarding and connecting to serial ports is not enabled, and more.
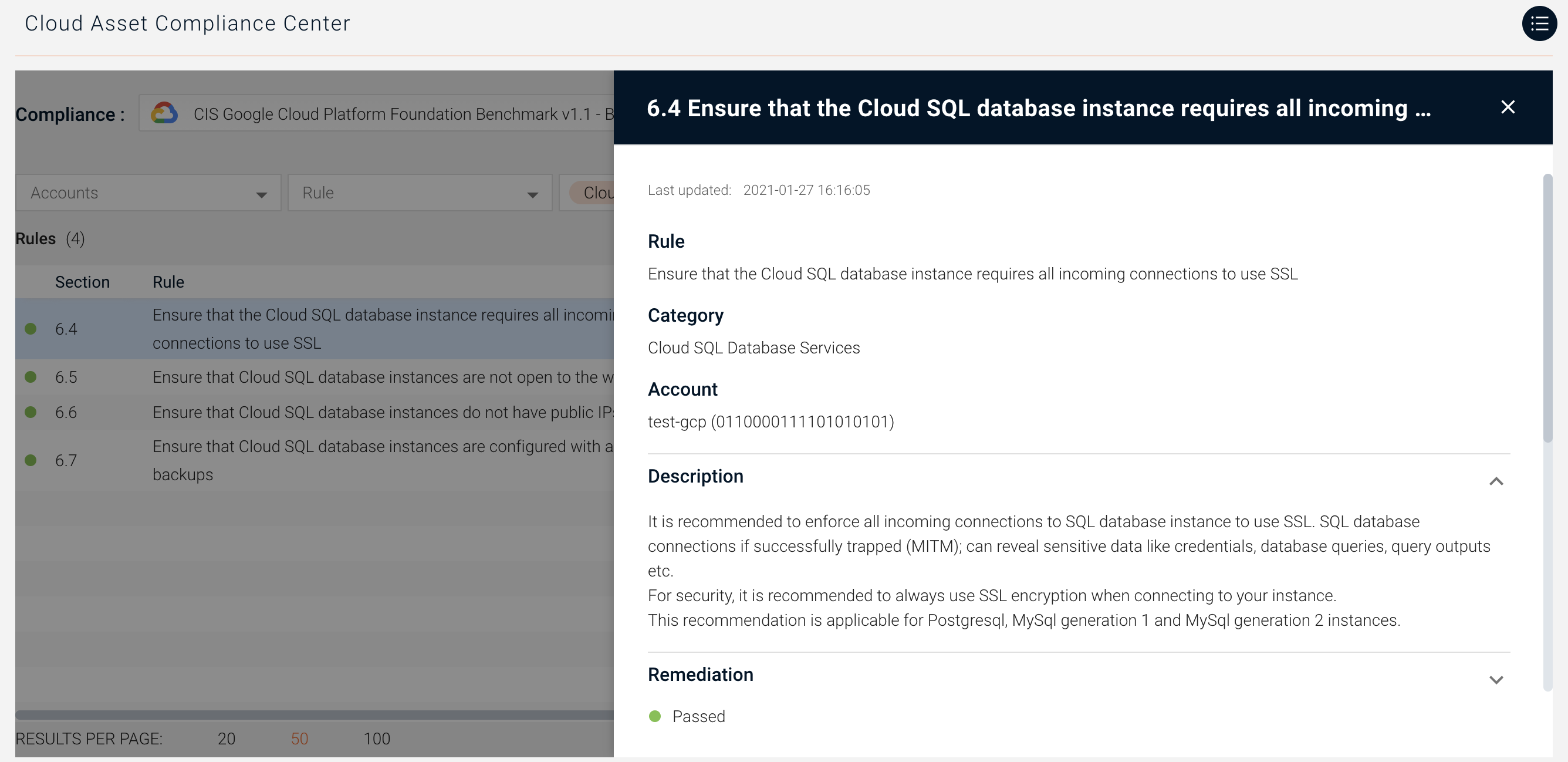
Ensure GCP Cloud SQL Database Services Are Secure and Properly Configured
Axonius examines Cloud SQL database services in GCP to ensure they are not open to the world, incoming traffic uses SSL, do not have public IP addresses, and more.
View All Categories
See a Full List of Categories for the CIS Google Cloud Platform Foundation Benchmark.





See the Platform
See the Axonius Platform for yourself with an interactive product tour, where we'll guide you through key applications of our Cybersecurity Asset Management and SaaS Management solutions.
Book a Demo
Request a demo to learn how the Axonius Platform provides a system of record for all digital infrastructure helping IT and security teams manage an always-expanding sprawl of devices, users, software, SaaS applications, cloud services, and the tools used to manage and secure them.