WHAT IS THE AXONIUS PLATFORM?
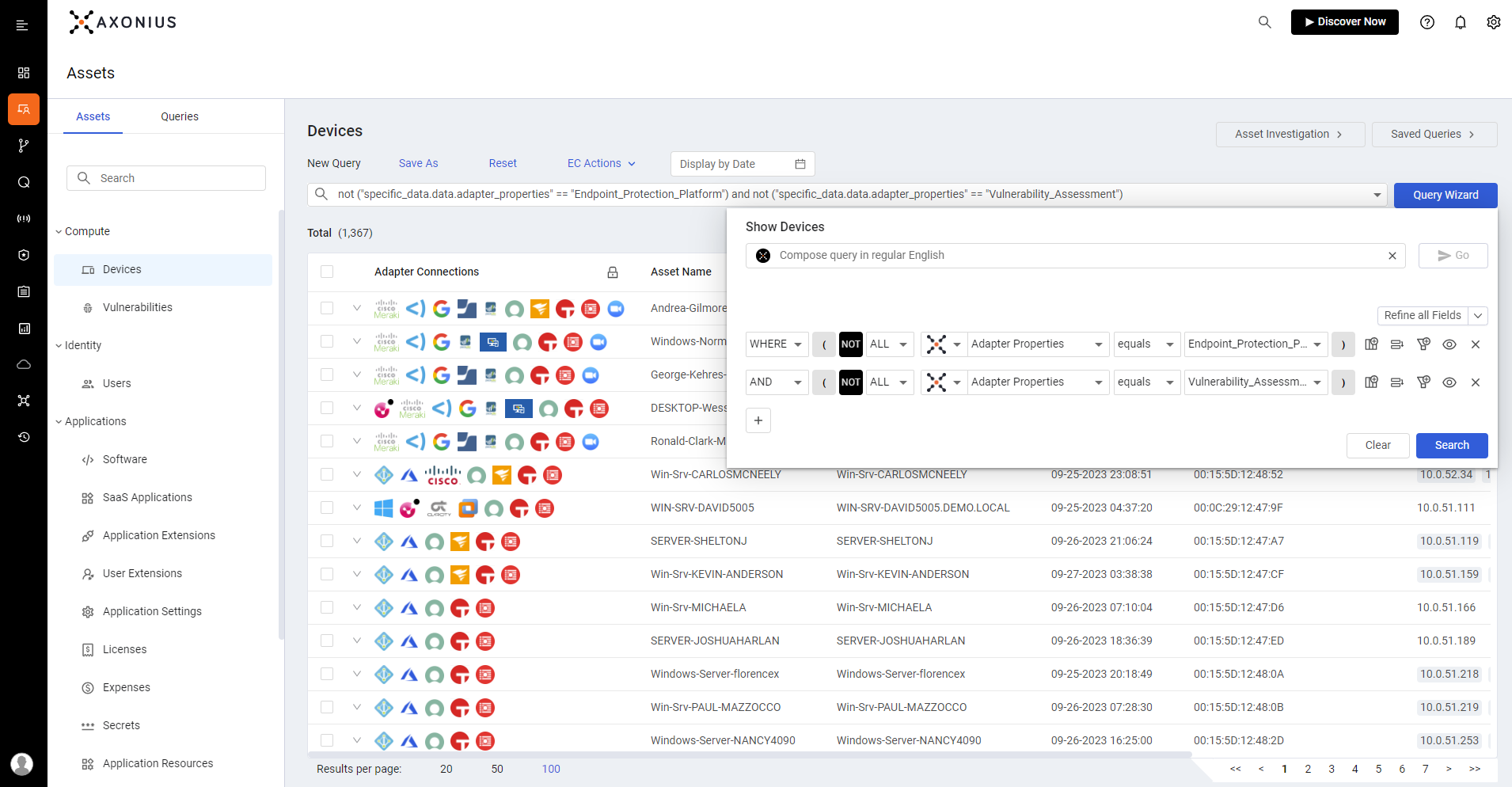
The Axonius Platform gives customers a comprehensive understanding of all assets, their relationships, and business-level context. By connecting to hundreds of data sources and aggregating, normalizing, deduplicating, and correlating data about devices, identities, cloud, software, SaaS applications, vulnerabilities, security controls, and their interrelationships, customers can ask questions, get answers, and automate action.
GET A CREDIBLE, COMPREHENSIVE INVENTORY
of all assets, their relationships, and business-level context.
DISCOVER SECURITY COVERAGE GAPS
and assess vulnerabilities, reduce cost, and prioritize risk.
AUTOMATICALLY VALIDATE AND ENFORCE POLICIES
to automate action and simplify workflows across departments and systems.
Cybersecurity Asset Management
Axonius Cybersecurity Asset Management aggregates, normalizes, deduplicates, and correlates asset data from existing data sources. Gain a complete cyber asset inventory, uncover security issues, and automate remediation action to reduce your attack surface and simplify workflows.
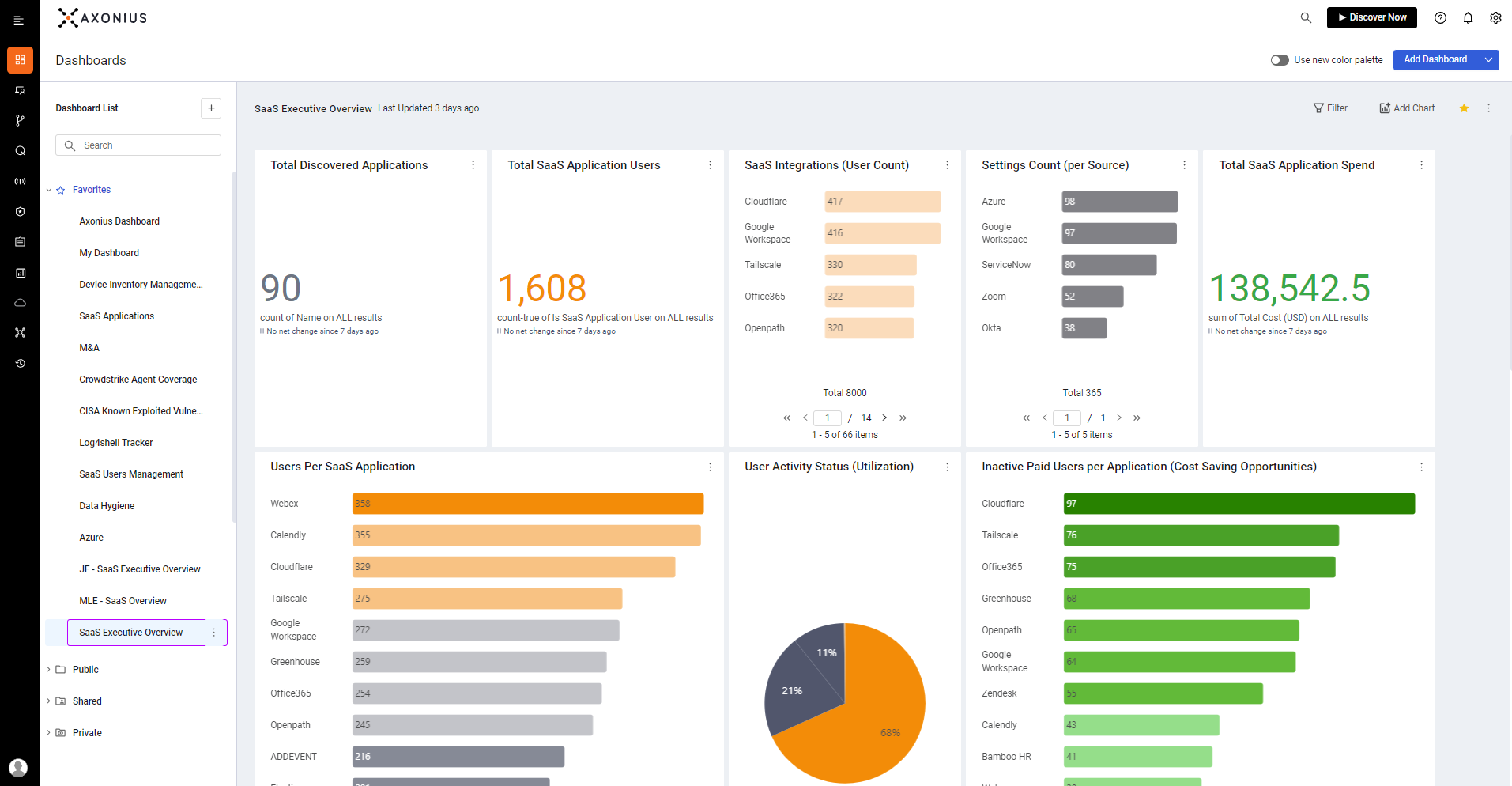
SaaS Management
Axonius SaaS Management helps customers control the complexity, cost, and risk associated with software as a service (SaaS) applications. Designed to mitigate SaaS management, security, and spend challenges, it provides organizations with a single source of truth into their SaaS environments.
Axonius Platform Modules
Learn more about both optional and included capabilities in the Axonius Platform.
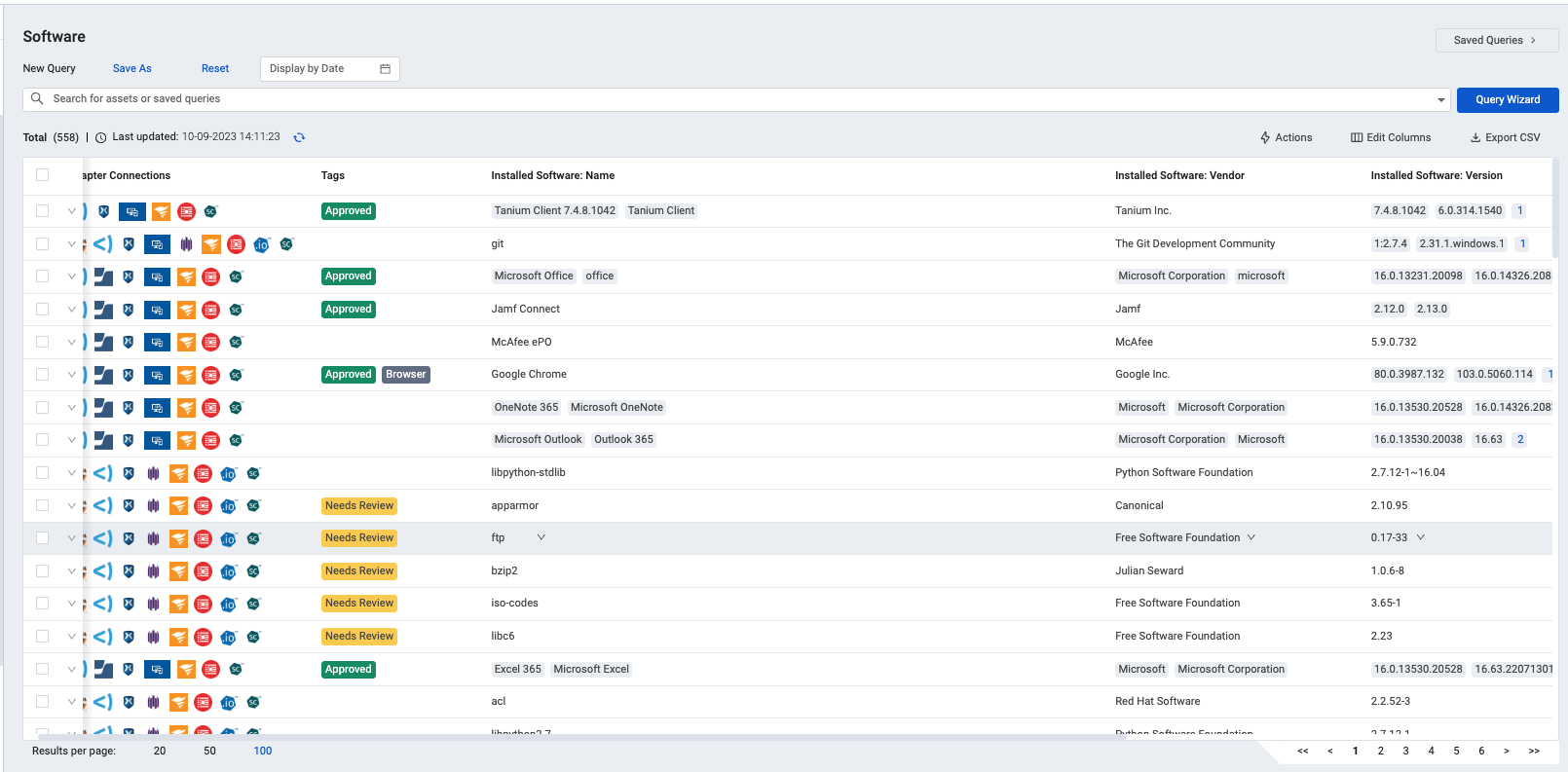
SOFTWARE MANAGEMENT
Axonius Software Management helps IT, finance, and security and risk teams automatically identify all software across the technology estate to identify unwanted and unsanctioned software, inform software spend and cost optimization, and reduce risk.
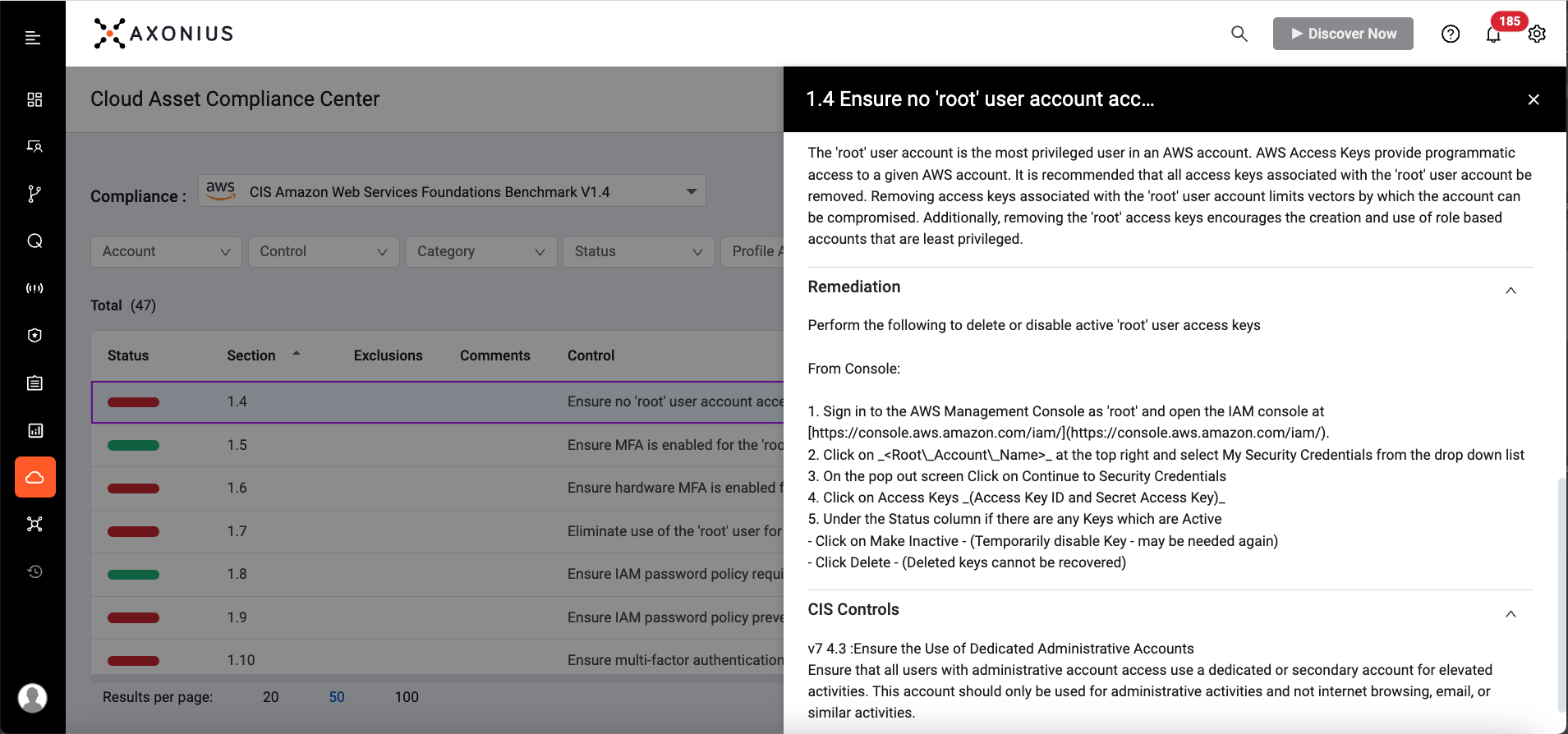
CLOUD ASSET COMPLIANCE
Axonius Cloud Asset Compliance helps customers see how their cloud instances adhere to or deviate from industry standards and benchmarks.
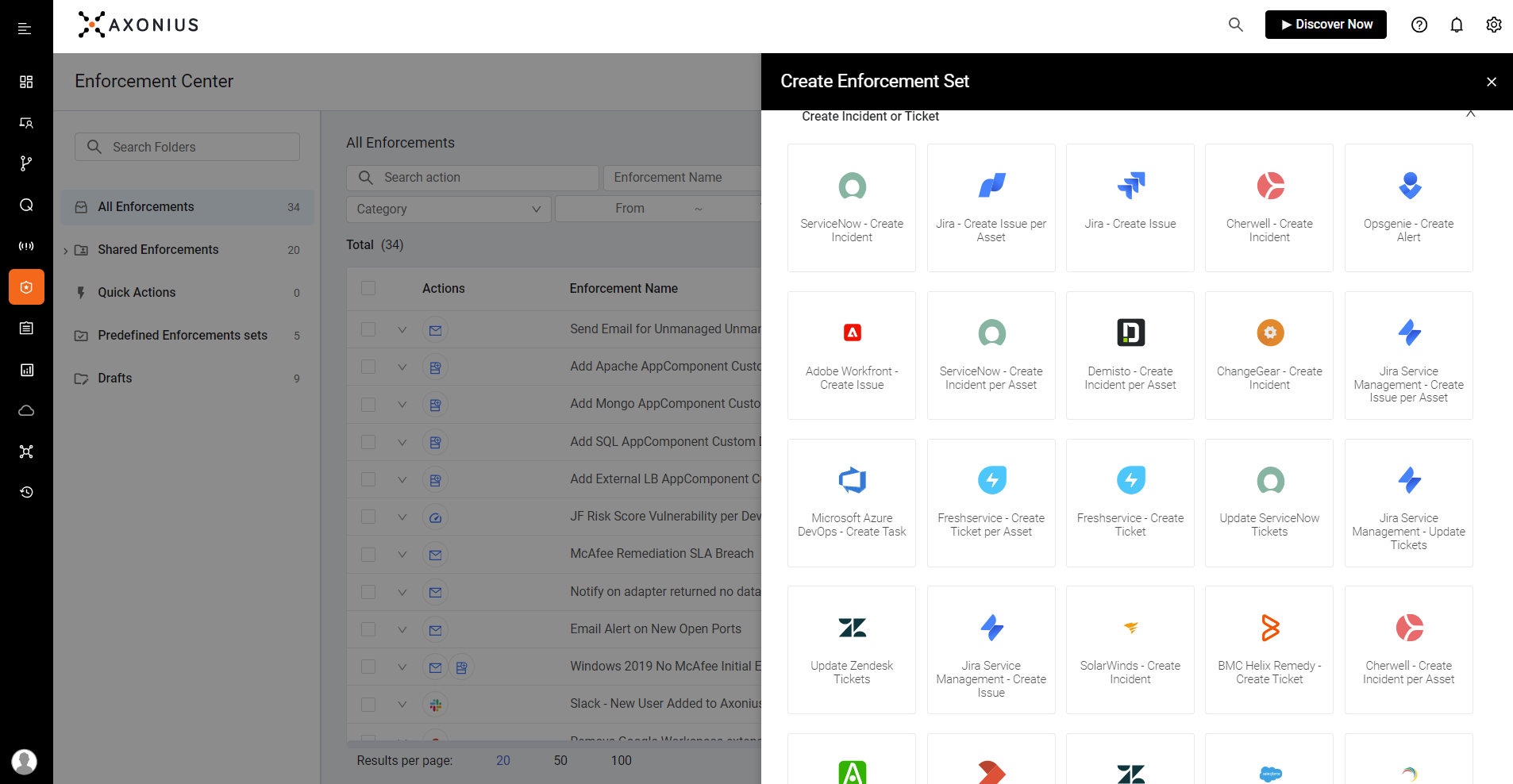
ENFORCEMENT CENTER
Automate alerting and response actions. Immediately triage and remediate vulnerabilities and IT security policy gaps.
VULNERABILITY MANAGEMENT
Uncover vulnerabilities affecting your digital infrastructure, and incorporate the necessary context to find, prioritize, and fix asset-related issues.
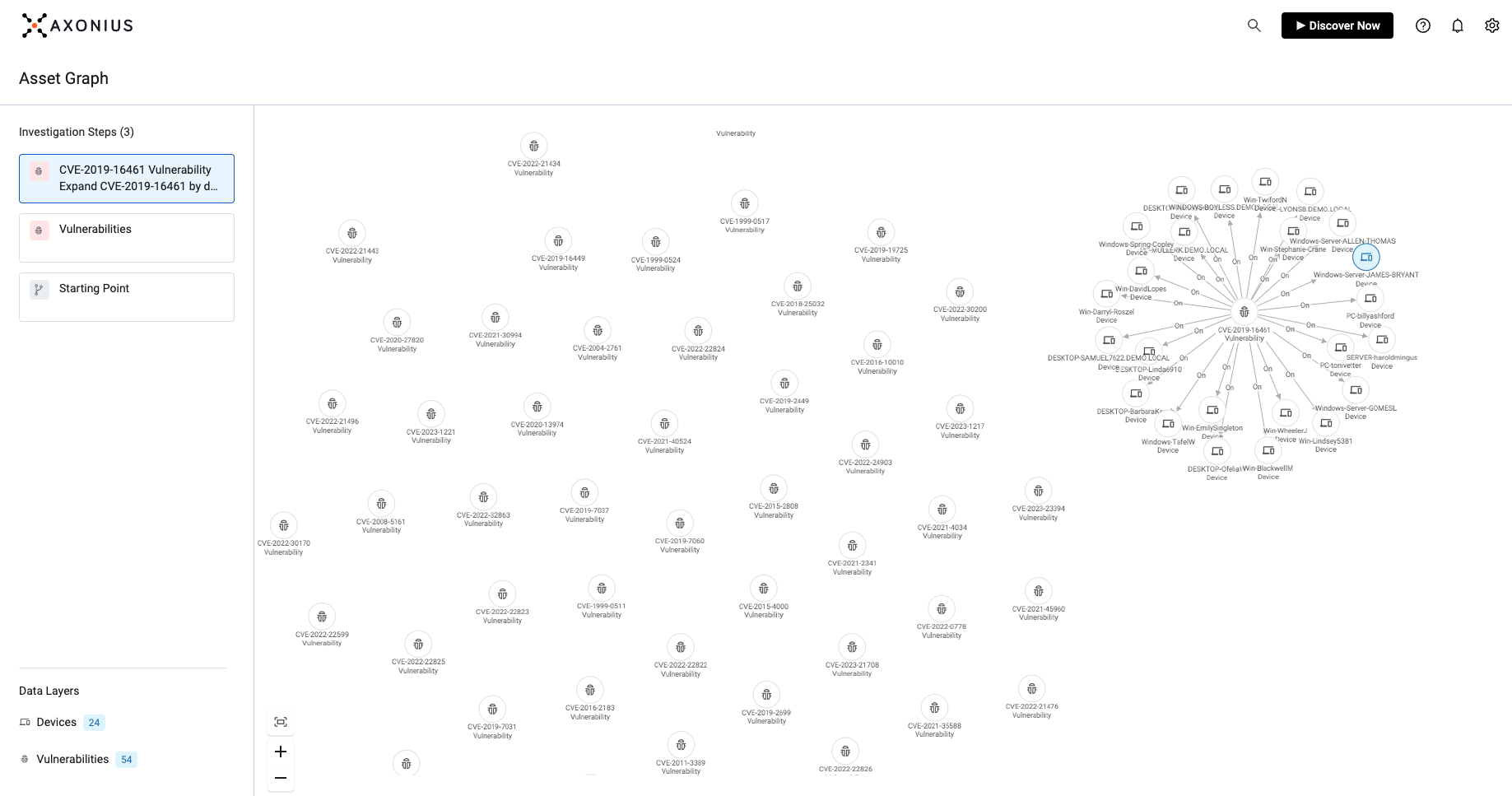




See the Platform
See the Axonius Platform for yourself with an interactive product tour, where we'll guide you through key applications of our Cybersecurity Asset Management and SaaS Management solutions.
Book a Demo
Request a demo to learn how the Axonius Platform provides a system of record for all digital infrastructure helping IT and security teams manage an always-expanding sprawl of devices, users, software, SaaS applications, cloud services, and the tools used to manage and secure them.