Axonius for Security Teams
Security engineers and teams are overwhelmed with asset complexity. Learn how the Axonius Platform helps them enforce controls, troubleshoot incidents, and report on the state of the assets in their environment.
HOW AXONIUS HELPS SECURITY TEAMS
With the number of assets per employee reaching staggering heights, and the number of cyber attacks growing exponentially, success relies on the tools and processes security teams put in place to see, manage, and secure assets. The Axonius Platform helps security teams control complexity — giving them confidence in securing their environments while optimizing resources, costs, and person-hours.
Adhere to Industry Security Standards
Implement and enhance security controls for compliance with security policies, standards, or frameworks like NIST, or CIS.
Operationalize and Enhance Security Processes
Automate security monitoring, protocol testing, and enforcement actions to prevent incidents and accelerate incident identification, containment, and resolution.
Optimize and Automate Audit Preparation
Reduce the inefficiencies of data compilation — like the cost, time, and person-hours associated with manual data collection.
Investigate Assets with Confidence
Use cross-platform, contextualized investigation to understand asset relationships and dependencies so you can make smart, informed decisions.
- Security Architecture
- Governance and Compliance
- Incident Response
Security Architecture
Credible, Comprehensive Visibility Into All Assets
Understanding your environment is a prerequisite to securing it. The Axonius Platform gives you full visibility into all assets so they can be identified, categorized, and secured appropriately. Axonius sees hardware, devices, software, user accounts, cloud instances, SaaS applications, networks, and more. Protect individual devices from misconfigurations, missing or malfunctioning agents, or security gaps. Monitor software applications for vulnerabilities, networks for rogue devices, users for over permissioning, or SaaS applications for shadow SaaS. Axonius ensures you can see, monitor, and manage all your assets.
.png?width=1906&height=992&name=Asset%20Graph%20-%20Device%20Asset%20Graph%20with%20Vuln%20and%20SaaS%20apps%20(1).png)
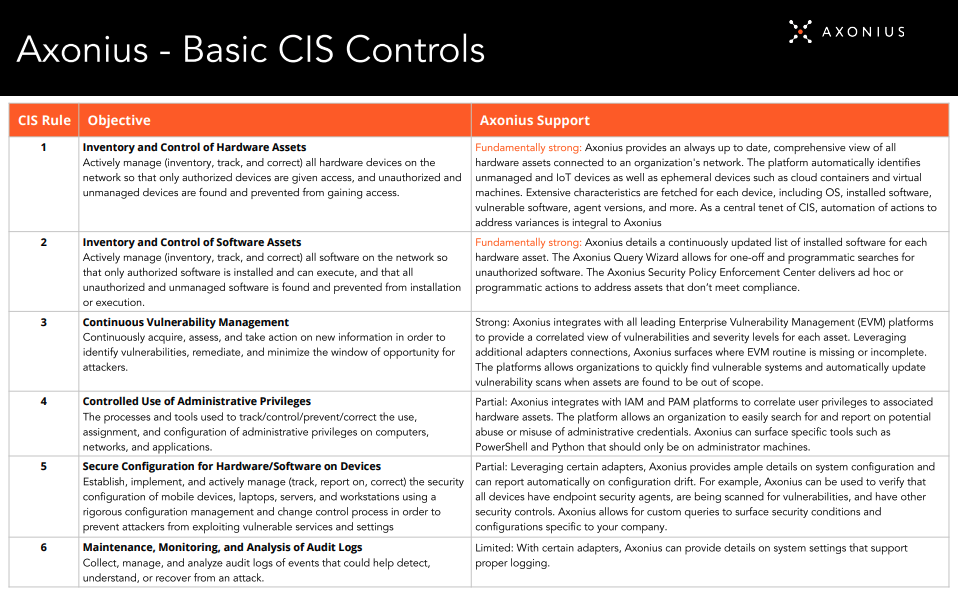
Aligning with Security Frameworks and Controls
Security best practice dictates that organizations follow multiple layers of security protocols — like adhering to accepted security frameworks or standards (i.e. NIST or CIS), and creating, monitoring, and enforcing internal or external security policies. The Axonius Platform helps security teams operationalize security protocols to achieve all of these and more. Create controls that adhere to industry standards and be alerted when the system falls out of compliance. Identify internal security policy lapses — devices missing security agents, users with outdated passwords, unsanctioned software, unauthorized cloud activity, or shadow IT. Replace manual monitoring and enforcement actions with automated actions to redirect person hours to higher value security initiatives.
Streamlining Risk Assessment and Response
Security teams can’t keep up with risk assessment and response on an individual basis — it just isn’t sustainable. The Axonius Platform automates security monitoring and protocol testing to provide credible, real-time data that helps prevent incidents and accelerate incident identification, containment, and resolution. Understand the total attack surface and confidently assess risk, resolving issues before they can be exploited.
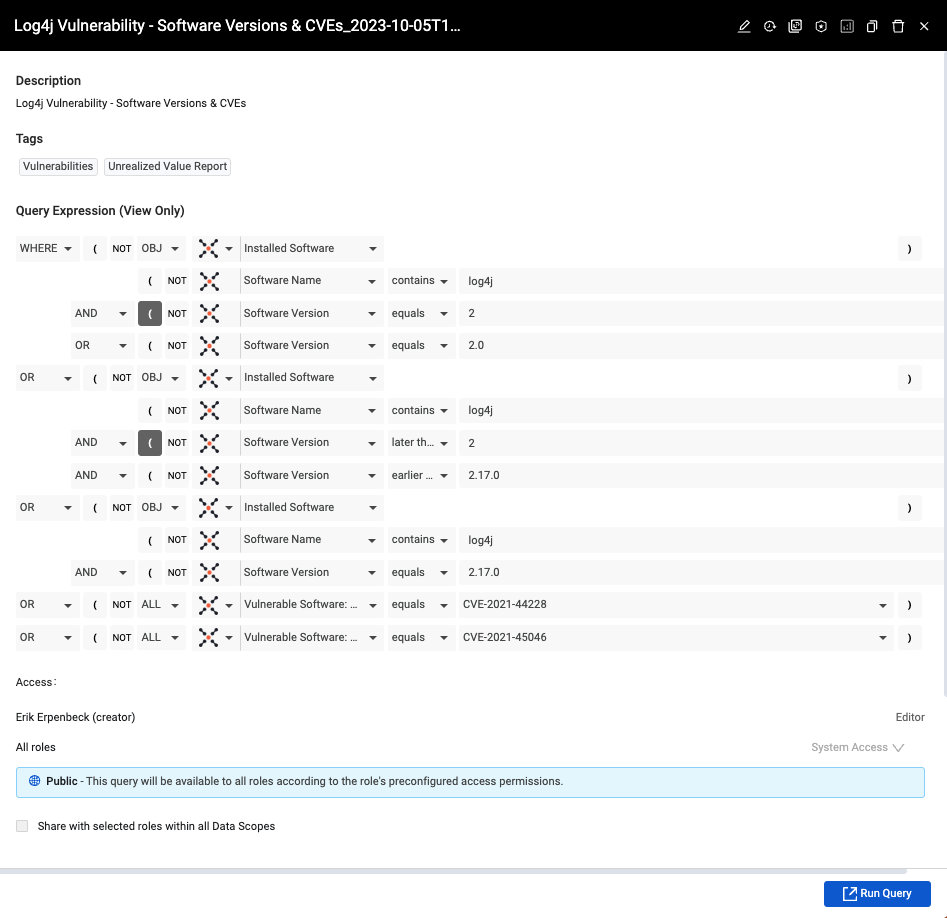
Governance and Compliance
Save Time on Audit Preparation
Security teams face seemingly endless hours of audit preparation for industry, internal, and even software vendor audits. The Axonius Platform reduces cost, time, and person-hours associated with manual data collection — lessening the burden of compiling data for reports to communicate security policy status. Regularly evaluate compliance against industry standards to be sure you’re exercising best-practices. Continually analyze internal security policies to be sure nothing falls out of expected parameters, and prepare for vendor audits by understanding software licenses and deployed instances.
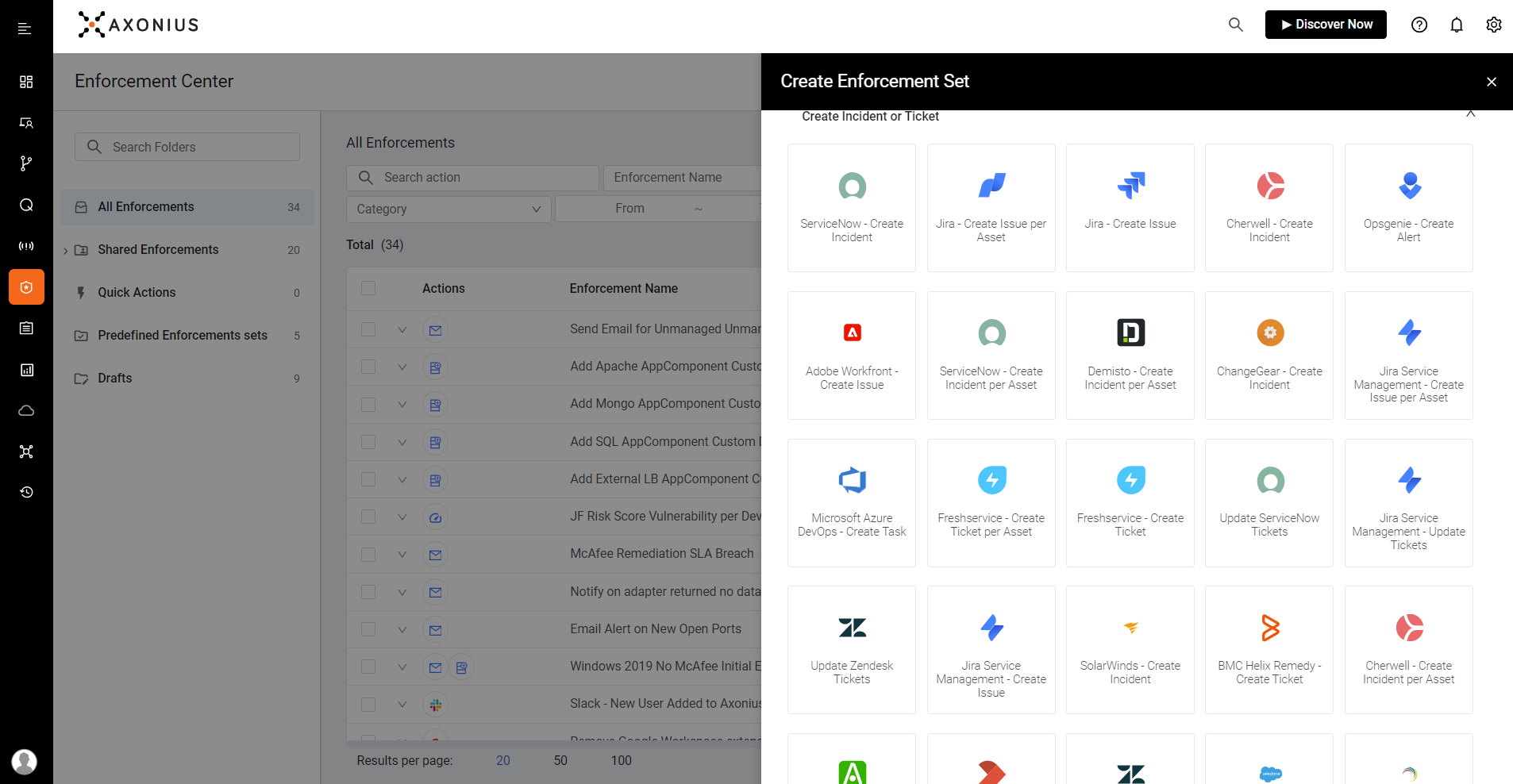
Automate Policy Enforcement
Security teams are burdened by the daily task of tracking the status of assets against policies and enforcing those that don’t comply. The Axonius Platform’s Enforcement Center automates asset monitoring and policy enforcement — helping organizations better meet expectations or avoid potential penalties. Customize automated response actions when unknown devices access the network, or unify cloud assets across all major providers to identify misconfigurations and policy lapses. Identify users with outdated passwords or shadow IT and automate responses to correct them.
Reporting On The Status Of Assets
Communicating the status of assets ensures all stakeholders are informed. The Axonius Platform enables security teams to create reports for one or multiple audiences, including data that supports decision making. Automatically generate charts and dashboards to track key asset metrics — like configuration management, vulnerability management, software management, data hygiene, user permissions, and more. Use the Axonius dashboard templates to improve time to value when determining what to track first, then incorporate individual charts, or whole dashboards into customizable, illustrated reports for external and internal reporting.
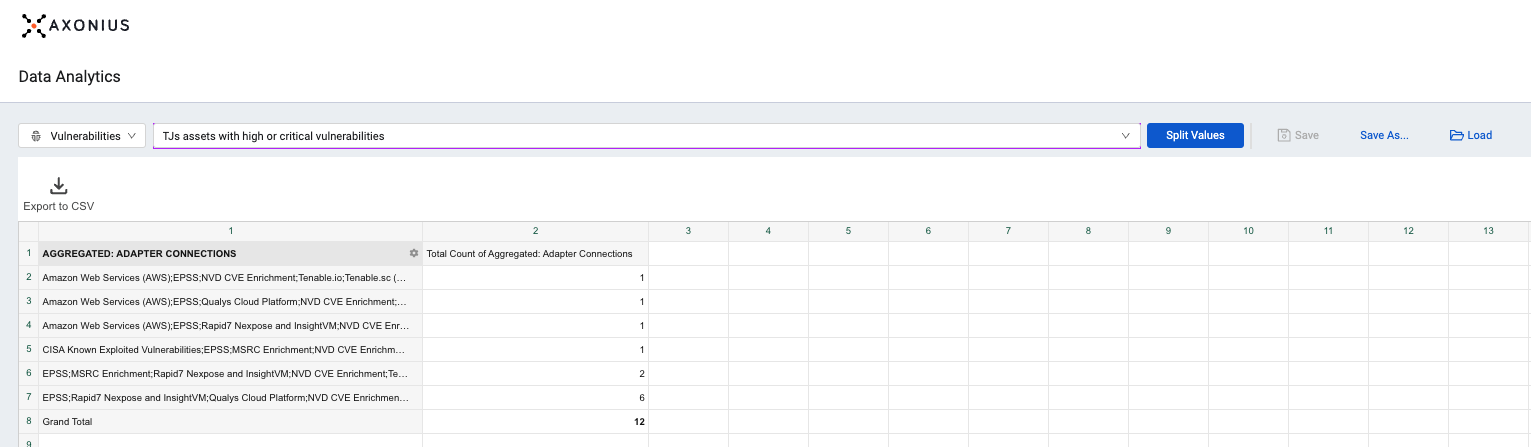
Incident Response
Analyze, Prioritize, and Remediate Vulnerabilities
When it comes to vulnerabilities, security teams rely on Axonius to tune out the noise. With over 25,000 new Common Vulnerabilities and Exposure (CVEs) a year and growing, drilling down to what really matters counts. Axonius operates on multiple levels to identify, prioritize, and remediate vulnerabilities. Understand which devices and cloud instances aren’t being scanned for vulnerabilities. Find known and unknown vulnerabilities, and contextualize them with device data, or visualize them with an asset graph to easily understand dependencies or relationships. Create automatic enforcement actions to remediate them as they emerge.

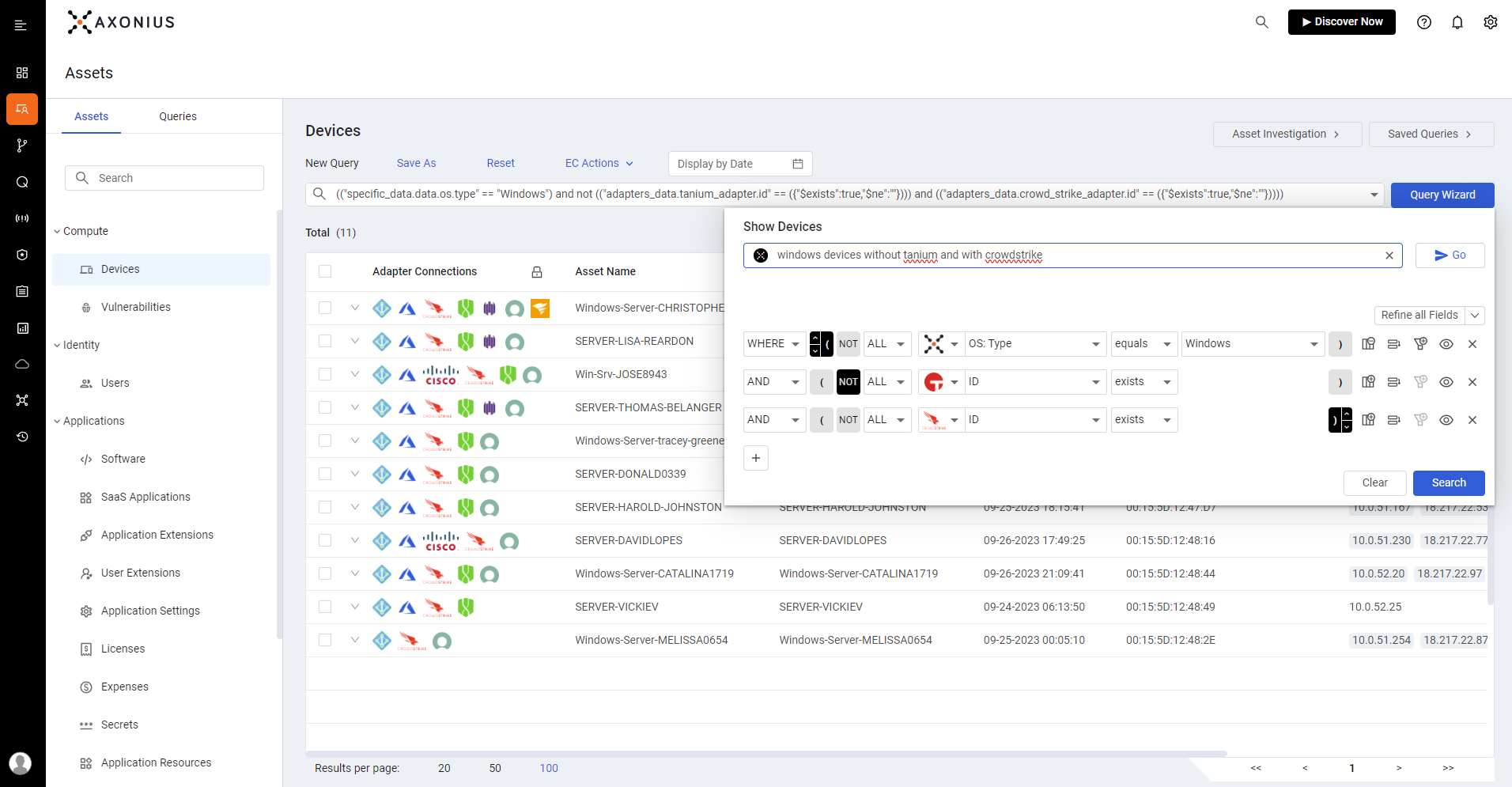
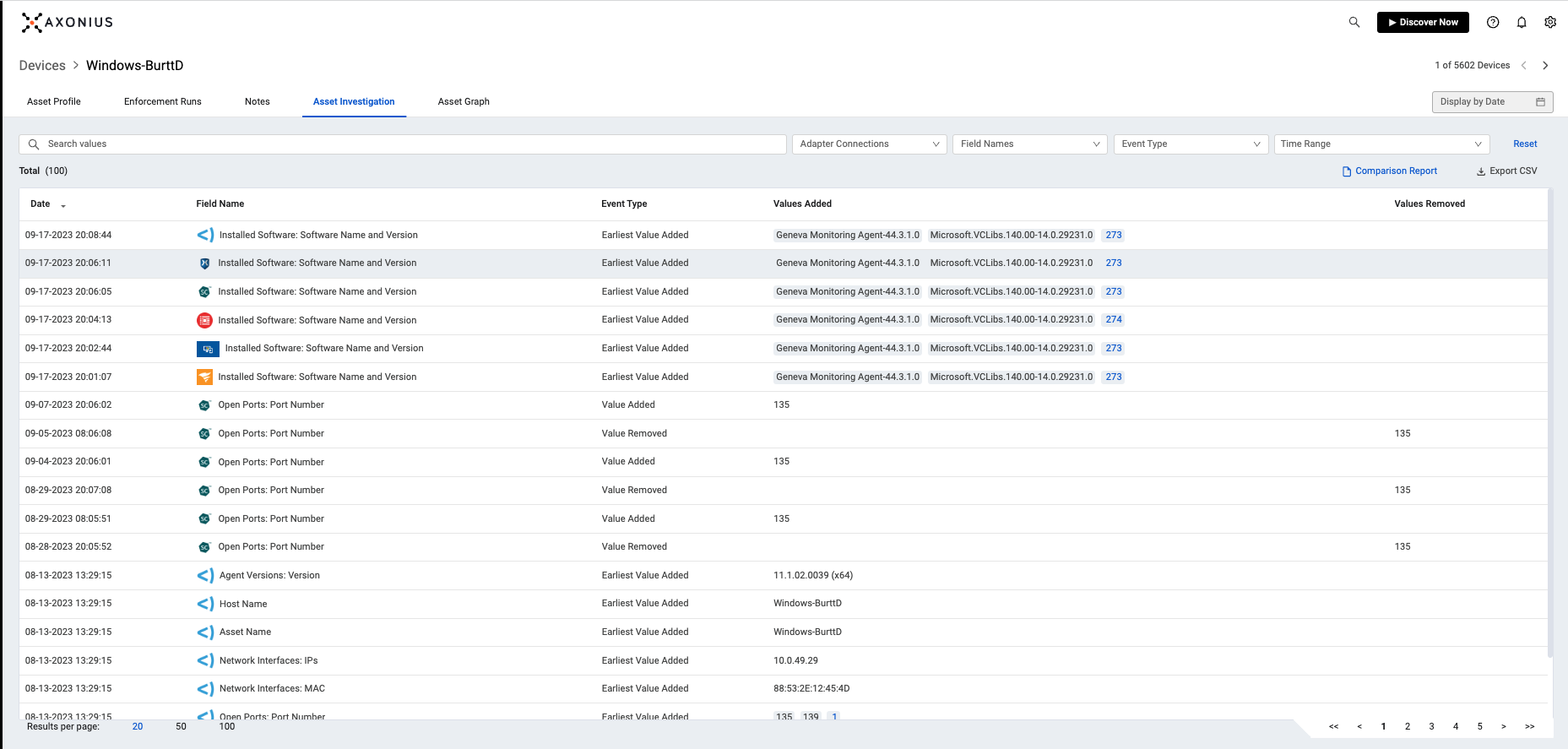
Investigating Assets and Incidents
When incidents do occur, security teams rely on the Axonius Platform for in-depth contextualization and investigation. The Axonius Query Wizard, AI-powered Query Assistant, and Asset Graph drill down to understand asset relationships and dependencies to accelerate incident response investigations. Troubleshoot escalated incidents with the Axonius Asset Investigation tool, or set rules for the Findings page to automatically discover issues so you can manage security incidents and minimize disruption.
The Right Security Tool For The Job
Security engineers experience the pressure of researching, designing, and providing ongoing evaluation of security solutions for all categories of assets. The Axonius Platform simplifies that process by identifying everything — devices, hardware, software, user accounts, cloud instances, SaaS applications, networks, and more. Find and investigate assets wherever they exist — inventory and track dynamic assets, including virtual machines and cloud workloads, throughout their entire lifecycle. Find what you’re looking for — all from the same Axonius interface — to optimize resources, costs, and person-hours, while maintaining a secure environment.
.png?width=1906&height=992&name=Asset%20Graph%20-%20Device%20Asset%20Graph%20with%20Vuln%20and%20SaaS%20apps%20(1).png)
See the Platform
See the Axonius Platform for yourself with an interactive product tour, where we'll guide you through key applications of our Cybersecurity Asset Management and SaaS Management solutions.
IT
Axonius correlates asset data from existing solutions to provide an always up-to-date inventory, uncover gaps, and automate action – giving IT and Security Teams the confidence to control complexity.
Security
Discover all SaaS applications, see data interconnectivity, identify risk, and optimize costs.